The Iranian nation-point out team recognized as MuddyWater has been observed carrying out harmful attacks on hybrid environments below the guise of a ransomware operation.
That’s in accordance to new findings from the Microsoft Threat Intelligence workforce, which identified the risk actor focusing on both equally on-premises and cloud infrastructures in partnership with an additional emerging activity cluster dubbed DEV-1084.
“While the menace actors attempted to masquerade the action as a regular ransomware marketing campaign, the unrecoverable actions clearly show destruction and disruption ended up the greatest targets of the procedure,” the tech big uncovered Friday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
MuddyWater is the title assigned to an Iran-based actor that the U.S. governing administration has publicly linked to the country’s Ministry of Intelligence and Security (MOIS). It is been regarded to be lively because at least 2017.
It can be also tracked by the cybersecurity local community underneath a variety of names, which includes Boggy Serpens, Cobalt Ulster, Earth Vetala, ITG17, Mercury, Seedworm, Static Kitten, TEMP.Zagros, and Yellow Nix.
Attacks mounted by the team have mainly singled out Center Japanese nations, with intrusions observed around the previous yr leveraging the Log4Shell flaw to breach Israeli entities.
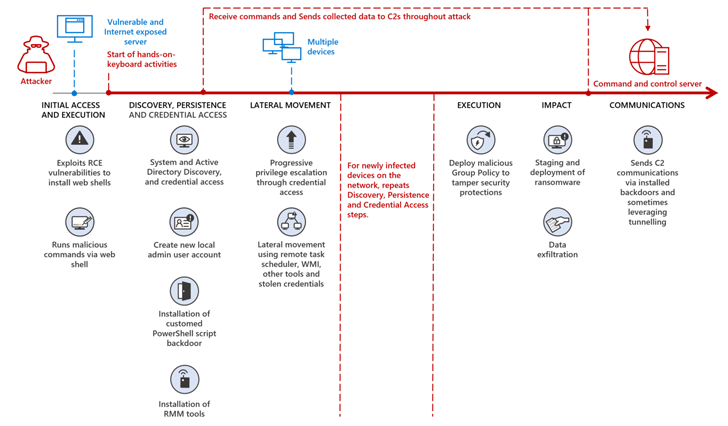
The hottest findings from Microsoft reveal the danger actor in all probability labored collectively with DEV-1084 to pull off the attack, the latter of which conducted the damaging steps immediately after MuddyWater successfully gained a foothold onto the focus on setting.
“Mercury very likely exploited recognised vulnerabilities in unpatched programs for original obtain just before handing off entry to DEV-1084 to complete comprehensive reconnaissance and discovery, establish persistence, and move laterally during the network, frequently ready weeks and occasionally months in advance of progressing to the up coming stage,” Microsoft explained.
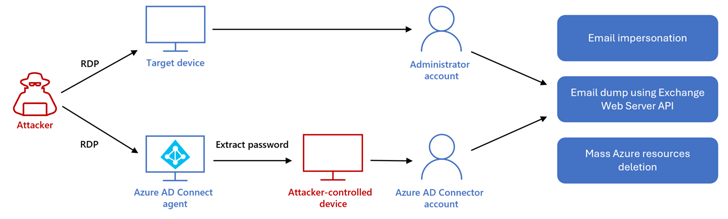
In the exercise detected by Redmond, DEV-1084 subsequently abused remarkably privileged compromised credentials to complete encryption of on-premise devices and large-scale deletion of cloud resources, which include server farms, virtual equipment, storage accounts, and virtual networks.
Moreover, the menace actors acquired whole accessibility to email inboxes through Trade Web Companies, applying it to complete “hundreds of search functions” and impersonate an unnamed superior-ranking employee to ship messages to both interior and external recipients.
All these steps are steps are believed to have transpired over a about a few-hour timeframe beginning at 12:38 a.m. (when the attacker logged into the Microsoft Azure environment by means of compromised qualifications) and ending at 3:21 a.m. (when the attacker despatched e-mail to other functions after the profitable cloud disruption).
It’s worth noting here that DEV-1084 refers to the same risk actor that assumed the “DarkBit” persona as component of a ransomware and extortion attack aimed at Technion, a leading research university in Israel, in February. The Israel National Cyber Directorate, last thirty day period, attributed the attack to MuddyWater.
Forthcoming WEBINARLearn to Safe the Id Perimeter – Confirmed Approaches
Strengthen your enterprise security with our approaching skilled-led cybersecurity webinar: Discover Id Perimeter procedures!
Do not Overlook Out – Save Your Seat!
“DEV-1084 […] introduced itself as a legal actor intrigued in extortion, possible as an attempt to obfuscate Iran’s backlink to and strategic enthusiasm for the attack,” Microsoft additional.
The hyperlinks amongst Mercury and DEV-1084 originate from infrastructure, IP handle, and tooling overlaps, with the latter noticed employing a reverse tunneling utility termed Ligolo, a staple MuddyWater artifact.
That stated, there is not ample proof to determine if DEV-1084 operates independently of MuddyWater and collaborates with other Iranian actors, or if it can be a sub-workforce which is only summoned when there is a require to carry out a damaging attack.
Cisco Talos, early final yr, described MuddyWater as a “conglomerate” comprising various scaled-down clusters alternatively than a single, cohesive team. The emergence of DEV-1084 indicates a nod in this route.
“While these groups appear to run independently, they are all determined by the similar aspects that align with Iranian countrywide security objectives, together with espionage, intellectual theft, and harmful or disruptive operations primarily based on the victims they focus on,” Talos observed in March 2022.
Located this post fascinating? Abide by us on Twitter and LinkedIn to read through a lot more special content we article.
Some pieces of this article are sourced from:
thehackernews.com

 Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari
Apple Releases Updates to Address Zero-Day Flaws in iOS, iPadOS, macOS, and Safari