Sophisticated cyber actors backed by Iran known as OilRig have been joined to a spear-phishing marketing campaign that infects victims with a new strain of malware identified as Menorah.
“The malware was designed for cyberespionage, able of identifying the machine, looking through and uploading files from the device, and downloading a different file or malware,” Craze Micro scientists Mohamed Fahmy and Mahmoud Zohdy reported in a Friday report.
The victimology of the attacks is not right away known, despite the fact that the use of decoys suggests at the very least a single of the targets is an firm situated in Saudi Arabia.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Also tracked less than the names APT34, Cobalt Gypsy, Hazel Sandstorm, and Helix Kitten, OilRig is an Iranian advanced persistent risk (APT) team that specializes in covert intelligence accumulating functions to infiltrate and preserve obtain within just specific networks.
The revelation builds on recent conclusions from NSFOCUS, which uncovered an OilRig phishing attack ensuing in the deployment of a new variant of SideTwist malware, indicating that it’s below constant enhancement.
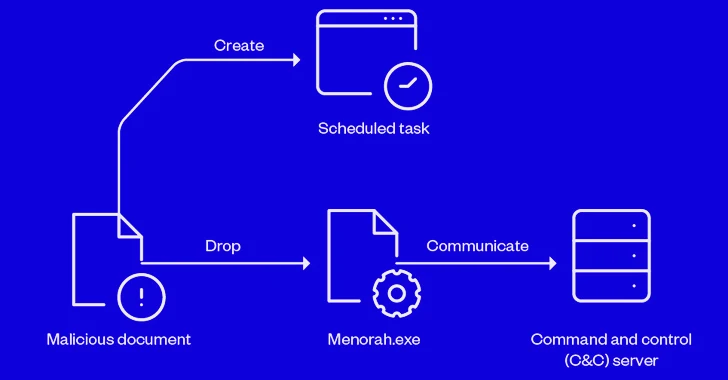
In the most recent an infection chain documented by Trend Micro, the lure document is applied to develop a scheduled job for persistence and drop an executable (“Menorah.exe”) that, for its component, establishes get in touch with with a remote server to await further more directions. The command-and-management server is currently inactive.
Upcoming WEBINARFight AI with AI — Battling Cyber Threats with Following-Gen AI Equipment
Ready to tackle new AI-driven cybersecurity troubles? Be part of our insightful webinar with Zscaler to handle the expanding risk of generative AI in cybersecurity.
Supercharge Your Abilities
The .NET malware, an improved version of the first C-based SideTwist implant discovered by Check out Position in 2021, is armed with several functions to fingerprint the focused host, listing directories and information, upload picked information from the compromised system, execute shell commands, and down load information to the method.
“The group persistently develops and enhances equipment, aiming to minimize security answers and researchers’ detection,” the scientists reported.
“Normal of APT groups, APT34 demonstrates their extensive sources and various capabilities, and will possible persist in customizing routines and social engineering approaches to use for every focused group to assure good results in intrusions, stealth, and cyber espionage.”
Uncovered this post attention-grabbing? Comply with us on Twitter and LinkedIn to study far more special information we put up.
Some elements of this posting are sourced from:
thehackernews.com

 New Critical Security Flaws Expose Exim Mail Servers to Remote Attacks
New Critical Security Flaws Expose Exim Mail Servers to Remote Attacks