The Iranian country-condition actor recognized as TA453 has been linked to a new established of spear-phishing attacks that infect the two Windows and macOS running devices with malware.
“TA453 finally made use of a assortment of cloud hosting providers to supply a novel an infection chain that deploys the recently recognized PowerShell backdoor GorjolEcho,” Proofpoint explained in a new report.
“When given the chance, TA453 ported its malware and attempted to launch an Apple flavored infection chain dubbed NokNok. TA453 also employed multi-persona impersonation in its never-ending espionage quest.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
TA453, also recognized by the names APT35, Charming Kitten, Mint Sandstorm, and Yellow Garuda, is a threat team joined to Iran’s Islamic Innovative Guard Corps (IRGC) that has been energetic due to the fact at least 2011. Most a short while ago, Volexity highlighted the adversary’s use of an current edition of a Powershell implant known as CharmPower (aka GhostEcho or POWERSTAR).
In the attack sequence learned by the organization security organization in mid-Might 2023, the hacking crew despatched phishing e-mail to a nuclear security pro at a U.S.-based consider tank targeted on foreign affairs that sent a destructive hyperlink to a Google Script macro that would redirect the goal to a Dropbox URL hosting a RAR archive.
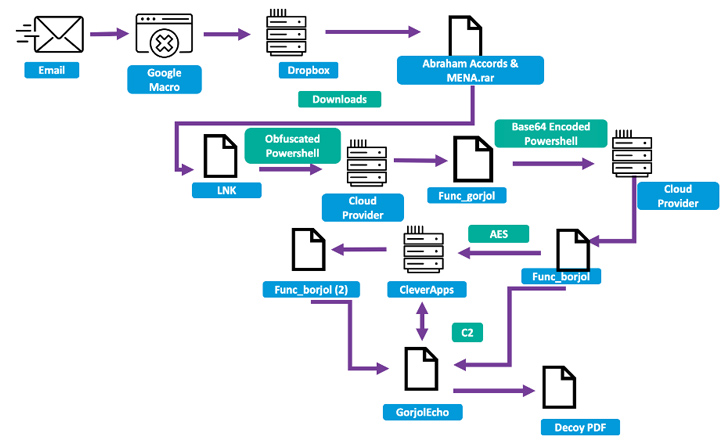
Current in the file is an LNK dropper that kicks off a multi-phase technique to finally deploy GorjolEcho, which, in flip, displays a decoy PDF doc, even though covertly awaiting following-stage payloads from a distant server.
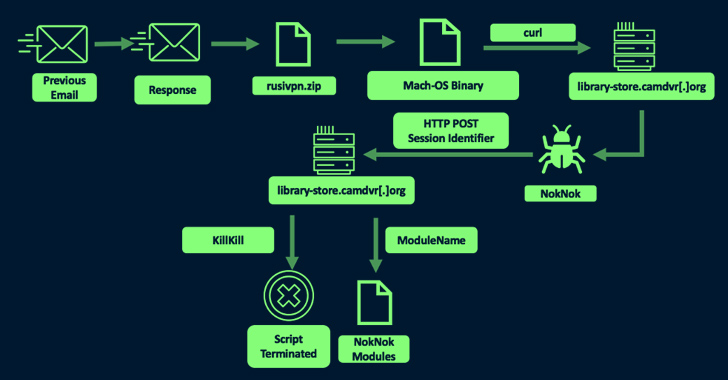
But upon realizing that the target is working with an Apple personal computer, TA453 is said to have tweaked its modus operandi to send a 2nd email with a ZIP archive embedding a Mach-O binary that masquerades as a VPN application, but in truth, is an AppleScript that reaches out to a remote server to down load a Bash script-primarily based backdoor termed NokNok.
Forthcoming WEBINAR🔐 Privileged Obtain Administration: Discover How to Conquer Crucial Issues
Uncover unique strategies to conquer Privileged Account Management (PAM) challenges and level up your privileged access security technique.
Reserve Your Location
NokNok, for its element, fetches as lots of as four modules that are able of accumulating working procedures, put in apps, and procedure metadata as nicely as location persistence working with LaunchAgents.
The modules “mirror a vast majority of the operation” of the modules affiliated with CharmPower, with NokNok sharing some supply code overlaps with macOS malware beforehand attributed to the team in 2017.
Also place to use by the actor is a bogus file-sharing site that very likely features to fingerprint guests and act as a system to track effective victims.
“TA453 proceeds to adapt its malware arsenal, deploying novel file types, and targeting new running devices,” the researchers reported, incorporating the actor “continues to work towards its very same stop plans of intrusive and unauthorized reconnaissance” when simultaneously complicating detection efforts.
Identified this short article intriguing? Abide by us on Twitter and LinkedIn to examine much more unique material we write-up.
Some elements of this report are sourced from:
thehackernews.com

 Surviving the 800 Gbps Storm: Gain Insights from Gcore’s 2023 DDoS Attack Statistics
Surviving the 800 Gbps Storm: Gain Insights from Gcore’s 2023 DDoS Attack Statistics