The Iranian risk actor regarded as MuddyWater is continuing its time-examined custom of relying on reputable remote administration applications to commandeer focused systems.
While the country-point out group has previously used ScreenConnect, RemoteUtilities, and Syncro, a new examination from Team-IB has revealed the adversary’s use of the SimpleHelp remote aid software in June 2022.
MuddyWater, energetic considering the fact that at minimum 2017, is assessed to be a subordinate aspect in Iran’s Ministry of Intelligence and Security (MOIS). Some of the top rated targets include Turkey, Pakistan, the U.A.E., Iraq, Israel, Saudi Arabia, Jordan, the U.S., Azerbaijan, and Afghanistan.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“MuddyWater utilizes SimpleHelp, a genuine remote machine regulate and administration tool, to guarantee persistence on target equipment,” Nikita Rostovtsev, senior threat analyst at Group-IB, mentioned.
“SimpleHelp is not compromised and is used as intended. The danger actors observed a way to download the tool from the formal web site and use it in their attacks.”
The correct distribution method used to fall the SimpleHelp samples is currently unclear, even though the group is known to mail spear-phishing messages bearing malicious links from currently compromised corporate mailboxes.
Group-IB’s findings ended up corroborated by Slovak cybersecurity agency ESET previously this January, detailing MuddyWater’s attacks in Egypt and Saudi Arabia that entailed the use of SimpleHelp to deploy its Ligolo reverse tunneling instrument and a credential harvester dubbed MKL64.
Upcoming WEBINARMaster the Artwork of Dark Web Intelligence Gathering
Understand the artwork of extracting menace intelligence from the dark web – Sign up for this expert-led webinar!
Save My Seat!
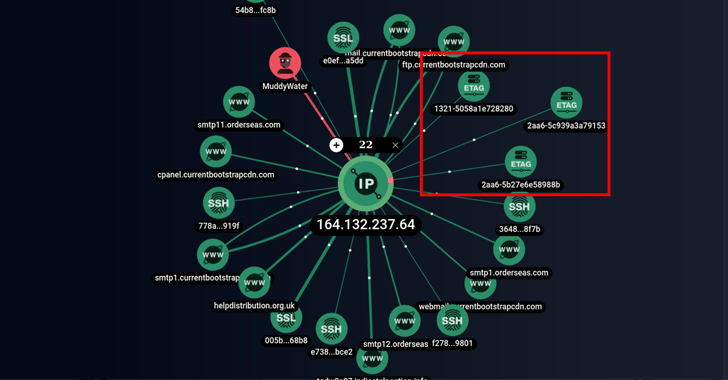
The Singapore-headquartered corporation additional reported it was capable to discover hitherto not known infrastructure operated by the group as nicely as a PowerShell script that is capable of receiving instructions from a remote server, the effects of which are sent again to the server.
The disclosure comes weeks just after Microsoft specific the group’s modus operandi of carrying out destructive attacks on hybrid environments less than the guise of a ransomware operation.
Observed this report intriguing? Observe us on Twitter and LinkedIn to study more distinctive written content we publish.
Some sections of this short article are sourced from:
thehackernews.com

 UK’s SMEs to Benefit From New Cyber Advisors
UK’s SMEs to Benefit From New Cyber Advisors