The Iranian threat actor recognized as MuddyWater has been attributed to a new command-and-manage (C2) infrastructure termed DarkBeatC2, turning out to be the hottest this sort of device in its arsenal immediately after SimpleHarm, MuddyC3, PhonyC2, and MuddyC2Go.
“Although once in a while switching to a new remote administration instrument or switching their C2 framework, MuddyWater’s approaches continue being regular,” Deep Instinct security researcher Simon Kenin reported in a specialized report published very last 7 days.
MuddyWater, also referred to as Boggy Serpens, Mango Sandstorm, and TA450, is assessed to be affiliated with Iran’s Ministry of Intelligence and Security (MOIS). It is regarded to be lively due to the fact at minimum 2017, orchestrating spear-phishing attacks that direct to the deployment of several genuine Distant Checking and Administration (RMM) solutions on compromised methods.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Prior conclusions from Microsoft display that the group has ties with a different Iranian risk exercise cluster tracked as Storm-1084 (aka DarkBit), with the latter leveraging the obtain to orchestrate harmful wiper attacks from Israeli entities.

The latest attack campaign, information of which were being also beforehand unveiled by Proofpoint previous month, commences with spear-phishing e-mails despatched from compromised accounts that have backlinks or attachments hosted on products and services like Egnyte to provide the Atera Agent application.
A single of the URLs in issue is “kinneretacil.egnyte[.]com,” where the subdomain “kinneretacil” refers to “kinneret.ac.il,” an educational institution in Israel and a consumer of Rashim, which, in convert, was breached by Lord Nemesis (aka Nemesis Kitten or TunnelVision) as portion of a source chain attack focusing on the tutorial sector in the region.
Lord Nemesis is suspected of being a “faketivist” procedure directed against Israel. It is also worthy of noting that Nemesis Kitten is a personal contracting company identified as Najee Technology, a subgroup inside of Mint Sandstorm which is backed by Iran’s Islamic Revolutionary Guard Corps (IRGC). The business was sanctioned by the U.S. Treasury in September 2022.
“This is important because if ‘Lord Nemesis’ ended up equipped to breach Rashim’s email method, they may possibly have breached the email devices of Rashim’s prospects working with the admin accounts that now we know they received from ‘Rashim,'” Kenin described.
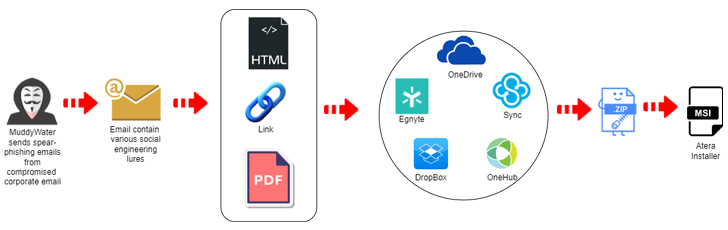
The web of connections has elevated the risk that MuddyWater may well have applied the email account linked with Kinneret to distribute the hyperlinks, thus supplying the messages an illusion of have faith in and tricking the recipients into clicking them.
“While not conclusive, the timeframe and context of the situations show a potential hand-off or collaboration amongst IRGC and MOIS to inflict as a lot damage as achievable on Israeli businesses and persons,” Kenin further additional.
The attacks are also notable for relying on a established of domains and IP addresses collectively dubbed DarkBeatC2 that are responsible for running the contaminated endpoints. This is accomplished by suggests of PowerShell code made to set up get in touch with with the C2 server on attaining initial access via other signifies.
According to independent results from Palo Alto Networks Device 42, the menace actor has been noticed abusing the Windows Registry’s AutodialDLL operate to facet-load a destructive DLL and eventually set up connections with a DarkBeatC2 area.
The mechanism, in certain, consists of establishing persistence as a result of a scheduled job that operates PowerShell to leverage the AutodialDLL registry key and load the DLL for C2 framework. The cybersecurity company claimed the method was put to use in a cyber attack aimed at an unnamed Middle East target.
Other procedures adopted by MuddyWater to establish a C2 relationship consist of the use of a first-phase payload shipped by way of the spear-phishing email and leveraging DLL side-loading to execute a malicious library.
A profitable call permits the contaminated host to get PowerShell responses that, for its aspect, fetches two far more PowerShell scripts from the exact server.
When one particular of the scripts is developed to read the contents of a file named “C:ProgramDataSysInt.log” and transmit them to the C2 server by means of an HTTP Publish ask for, the 2nd script periodically polls the server to attain supplemental payloads and writes the outcomes of the execution to “SysInt.log.” The actual character of the subsequent-phase payload is currently not known.

“This framework is equivalent to the previous C2 frameworks employed by MuddyWater,” Kenin reported. “PowerShell remains their ‘bread and butter.'”
Curious Serpens Targets Defense Sector with FalseFont Backdoor
The disclosure arrives as Unit 42 unpacked the inner workings of a backdoor termed FalseFont that’s used by an Iranian threat actor recognized as Peach Sandstorm (aka APT33, Curious Serpens, Elfin, and Refined Kitten) in attacks focusing on the aerospace and defense sectors.
“The danger actors mimic legitimate human methods application, using a bogus task recruitment approach to trick victims into setting up the backdoor,” security researchers Tom Fakterman, Daniel Frank, and Jerome Tujague mentioned, describing FalseFont as “remarkably focused.”
As soon as put in, it presents a login interface impersonating an aerospace firm and captures the qualifications as effectively as the instructional and work record entered by the sufferer to a risk-actor controlled C2 server in JSON format.
The implant, in addition to its graphical consumer interface (GUI) element for person inputs, also stealthily activates a next component in the track record that establishes persistence on the method, gathers process metadata, and executes commands and processes despatched from the C2 server.
Other attributes of FalseFont contain the capacity to download and upload information, steal credentials, capture screenshots, terminate unique procedures, run PowerShell commands, and self-update the malware.
Found this article interesting? Abide by us on Twitter and LinkedIn to study more distinctive written content we publish.
Some sections of this short article are sourced from:
thehackernews.com


 Zero-Day Alert: Critical Palo Alto Networks PAN-OS Flaw Under Active Attack
Zero-Day Alert: Critical Palo Alto Networks PAN-OS Flaw Under Active Attack