The Iranian nation-point out hacking group known as OilRig has continued to concentrate on govt corporations in the Middle East as section of a cyber espionage marketing campaign that leverages a new backdoor to exfiltrate facts.
“The marketing campaign abuses genuine but compromised email accounts to mail stolen information to exterior mail accounts controlled by the attackers,” Pattern Micro researchers Mohamed Fahmy, Sherif Magdy, and Mahmoud Zohdy said.
Whilst the strategy in by itself is not unheard of, the growth marks the 1st time OilRig has adopted it in its playbook, indicating the continued evolution of its procedures to bypass security protections.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The advanced persistent danger (APT) team, also referred to as APT34, Cobalt Gypsy, Europium, and Helix Kitten, has been documented for its qualified phishing attacks in the Center East given that at the very least 2014.
Linked to Iran’s Ministry of Intelligence and Security (MOIS), the team is recognized to use a varied toolset in its operations, with recent attacks in 2021 and 2022 employing backdoors these types of as Karkoff, Shark, Marlin, and Saitama for information theft.
The setting up issue of the most current activity is a .NET-based mostly dropper which is tasked with providing four different information, such as the most important implant (“DevicesSrv.exe”) responsible for exfiltrating particular files of desire.
Also put to use in the 2nd phase is a dynamic-url library (DLL) file which is capable of harvesting credentials from domain users and neighborhood accounts.
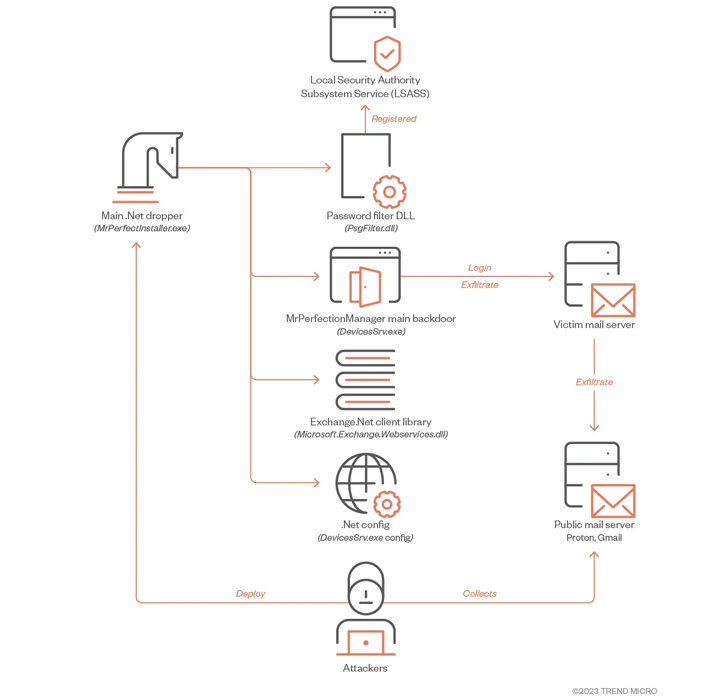
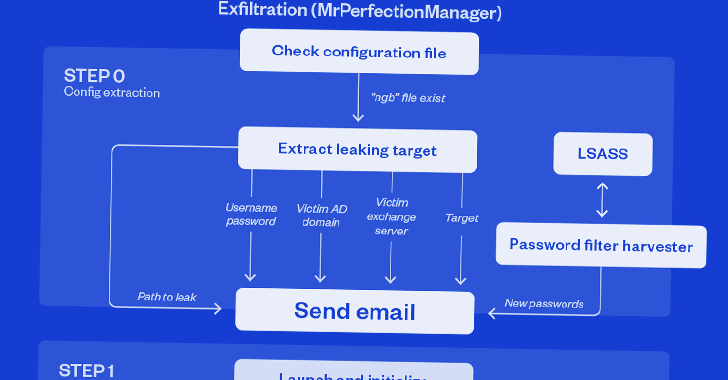
The most notable aspect of the .NET backdoor is its exfiltration regime, which involves employing the stolen credentials to deliver digital missives to actor-managed email Gmail and Proton Mail addresses.
“The threat actors relay these e-mail by using authorities Trade Servers utilizing vaild accounts with stolen passwords,” the researchers explained.
The campaign’s connections to APT34 stems from similarities in amongst the initial-phase dropper and Saitama, the victimology patterns, and the use of internet-going through exchange servers as a communication system, as observed in the situation of Karkoff.
If anything, the expanding variety of malicious equipment related with OilRig signifies the risk actor’s “overall flexibility” to come up with new malware dependent on the targeted environments and the privileges possessed at a specified phase of the attack.
“Inspite of the routine’s simplicity, the novelty of the second and very last phases also show that this complete routine can just be a modest part of a greater campaign targeting governments,” the researchers claimed.
Found this post fascinating? Stick to us on Twitter and LinkedIn to study additional exceptional content we article.
Some components of this post are sourced from:
thehackernews.com

 The Pivot: How MSPs can Turn a Challenge Into a Once-in-a-Decade Opportunity
The Pivot: How MSPs can Turn a Challenge Into a Once-in-a-Decade Opportunity