At the very least eight internet sites affiliated with delivery, logistics, and fiscal expert services businesses in Israel have been targeted as portion of a watering hole attack.
Tel Aviv-based cybersecurity firm ClearSky attributed the attacks with very low confidence to an Iranian risk actor tracked as Tortoiseshell, which is also called Crimson Sandstorm (earlier Curium), Imperial Kitten, and TA456.
“The contaminated web pages gather preliminary user information via a script,” ClearSky explained in a technical report published Tuesday. Most of the impacted internet websites have been stripped of the rogue code.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Tortoiseshell is recognized to be active because at minimum July 2018, with early attacks focusing on IT vendors in Saudi Arabia. It has also been noticed setting up pretend using the services of internet sites for U.S. armed service veterans in a bid to trick them into downloading distant access trojans.
That reported, this is not the initial time Iranian exercise clusters have established their sights on the Israeli shipping and delivery sector with watering holes.
The attack technique, also named strategic web site compromises, is effective by infecting a site that’s known to be frequently visited by a group of customers or individuals within just a distinct market to allow the distribution of malware.
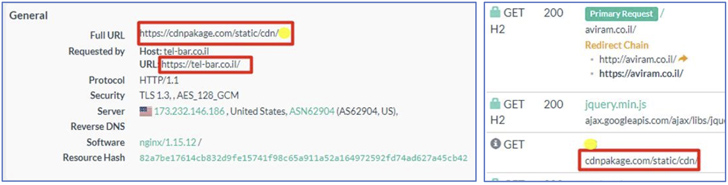
In August 2022, an emerging Iranian actor named UNC3890 was attributed to a watering gap hosted on a login website page of a respectable Israeli shipping and delivery firm that is intended to transmit preliminary details about the logged-in user to an attacker-managed area.
The most current intrusions documented by ClearSky demonstrate that the destructive JavaScript injected into the websites capabilities in a identical manner, gathering information about the system and sending it to a remote server.
Future WEBINARZero Trust + Deception: Discover How to Outsmart Attackers!
Find out how Deception can detect state-of-the-art threats, end lateral movement, and enrich your Zero Believe in system. Be part of our insightful webinar!
Conserve My Seat!
The JavaScript code further tries to identify the user’s language preference, which ClearSky explained could be “useful to the attacker to customize their attack based on the user’s language.”
On top of that, the attacks also make use of a area named jquery-stack[.]online for command-and-management (C2). The objective is to fly less than the radar by impersonating the authentic jQuery JavaScript framework.
The advancement will come as Israel continues to be the most popular focus on for Iranian condition-sponsored crews. Microsoft, before this month, highlighted their new approach of combining “offensive cyber operations with multi-pronged affect operations to fuel geopolitical alter in alignment with the regime’s goals.”
Found this report fascinating? Adhere to us on Twitter and LinkedIn to examine additional exclusive written content we put up.
Some pieces of this report are sourced from:
thehackernews.com


 Private Sector Cybersecurity Task Force Called for to Defend Democracies
Private Sector Cybersecurity Task Force Called for to Defend Democracies