A financially enthusiastic menace actor known as UNC4990 is leveraging weaponized USB devices as an preliminary an infection vector to target organizations in Italy.
Google-owned Mandiant stated the attacks solitary out multiple industries, like wellbeing, transportation, development, and logistics.
“UNC4990 functions usually include common USB an infection adopted by the deployment of the EMPTYSPACE downloader,” the firm stated in a Tuesday report.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“All through these functions, the cluster relies on third-party web sites this sort of as GitHub, Vimeo, and Ars Technica to host encoded more levels, which it downloads and decodes by using PowerShell early in the execution chain.”

UNC4990, energetic considering the fact that late 2020, is assessed to be running out of Italy primarily based on the extensive use of Italian infrastructure for command-and-regulate (C2) functions.
It’s presently not identified if UNC4990 features only as an preliminary accessibility facilitator for other actors. The end target of the menace actor is not apparent, although in one particular instance an open-source cryptocurrency miner is claimed to have been deployed just after months of beaconing exercise.
Aspects of the marketing campaign had been beforehand documented by Fortgale and Yoroi in early December 2023, with the former tracking the adversary under the title Nebula Broker.
The infection commences when a target double-clicks on a destructive LNK shortcut file on a detachable USB gadget, top to the execution of a PowerShell script that is accountable for downloading EMPTYSPACE (aka BrokerLoader or Vetta Loader) from a distant server via a further intermedia PowerShell script hosted on Vimeo.
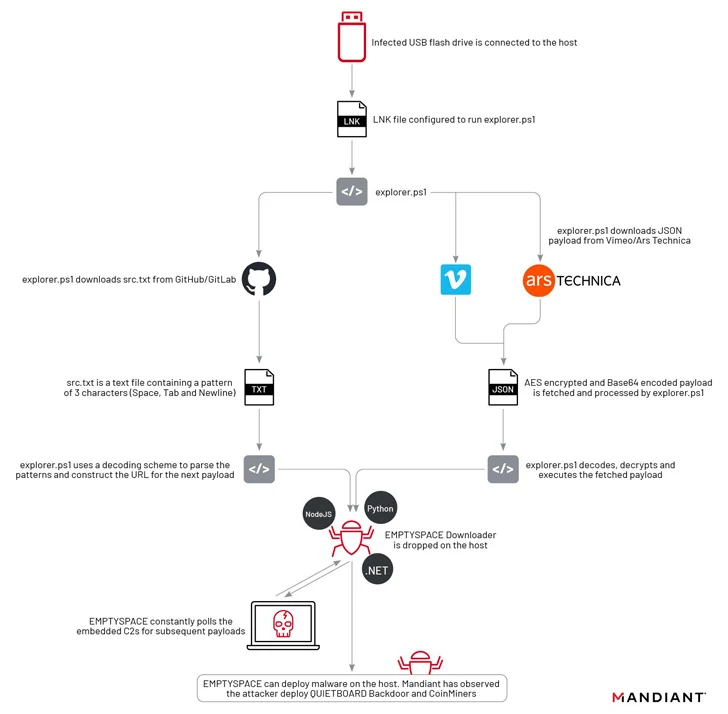
Yoroi stated it identified four various variants of EMPTYSPACE created in Golang, .NET, Node.js, and Python, which subsequently acts as a conduit for fetching upcoming-stage payloads more than HTTP from the C2 server, together with a backdoor dubbed QUIETBOARD.
A noteworthy element of this period is the use of popular sites like Ars Technica, GitHub, GitLab, and Vimeo for hosting the malicious payload.
“The articles hosted on these providers posed no immediate risk for the everyday people of these solutions, as the material hosted in isolation was completely benign,” Mandiant scientists stated. “Anybody who may well have inadvertently clicked or considered this material in the earlier was not at risk of remaining compromised.”

QUIETBOARD, on the other hand, is a Python-based mostly backdoor with a large assortment of characteristics that let it to execute arbitrary instructions, change crypto wallet addresses copied to clipboard to redirect fund transfers to wallets below their regulate, propagate the malware to removable drives, get screenshots, and collect procedure information and facts.
Moreover, the backdoor is able of modular expansion and jogging unbiased Python modules like coin miners as very well as dynamically fetching and executing Python code from the C2 server.
“The evaluation of both of those EMPTYSPACE and QUIETBOARD suggests how the danger actors took a modular method in developing their toolset,” Mandiant mentioned.
“The use of multiple programming languages to create diverse variations of the EMPTYSPACE downloader and the URL transform when the Vimeo movie was taken down exhibit a predisposition for experimentation and adaptability on the danger actors’ facet.”
Discovered this post interesting? Abide by us on Twitter and LinkedIn to read far more exclusive written content we put up.
Some areas of this article are sourced from:
thehackernews.com


 Chinese Hackers Exploiting Critical VPN Flaws to Deploy KrustyLoader Malware
Chinese Hackers Exploiting Critical VPN Flaws to Deploy KrustyLoader Malware