Cybersecurity scientists have learned that the malware identified as BLOODALCHEMY utilized in attacks targeting authorities businesses in Southern and Southeastern Asia is in reality an updated edition of Deed RAT, which is considered to be a successor to ShadowPad.
“The origin of BLOODALCHEMY and Deed RAT is ShadowPad and provided the heritage of ShadowPad staying utilized in a lot of APT campaigns, it is crucial to shell out specific awareness to the utilization pattern of this malware,” Japanese enterprise ITOCHU Cyber & Intelligence said.
BLOODALCHEMY was 1st documented by Elastic Security Labs in Oct 2023 in connection with a campaign mounted by an intrusion set it tracks as REF5961 targeting the Affiliation of Southeast Asian Nations (ASEAN) nations.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

A barebones x86 backdoor penned in C, it can be injected into a signed benign process (“BrDifxapi.exe”) working with a procedure referred to as DLL facet-loading, and is capable of overwriting the toolset, collecting host facts, loading added payloads, and uninstalling and terminating by itself.
“Though unconfirmed, the presence of so couple of productive commands indicates that the malware may perhaps be a subfeature of a larger sized intrusion set or malware offer, even now in improvement, or an exceptionally focused piece of malware for a unique tactical usage,” Elastic researchers noted at the time.
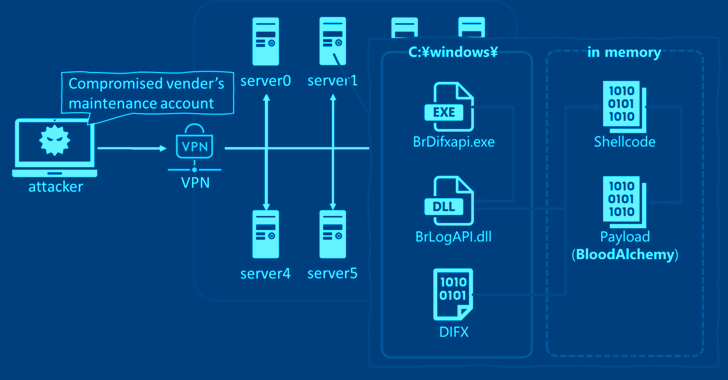
Attack chains deploying have been noticed compromising a servicing account on a VPN unit to attain first entry to deploy BrDifxapi.exe, which is then applied to sideload BrLogAPI.dll, a loader that’s responsible for executing the BLOODALCHEMY shellcode in memory immediately after extracting it from a file named DIFX.
The malware employs what’s identified as a operate manner that decides its habits, efficiently allowing for it to evade investigation in sandbox environments, established up persistence, set up contact with a distant server, and control the infected host by means of the carried out backdoor instructions.

ITOCHU’s evaluation of BLOODALCHEMY has also determined code similarities with Deed RAT, a multifaceted malware completely used by a danger actor recognized as Room Pirates and is viewed as the up coming iteration of ShadowPad, which in alone is an evolution of PlugX.
“The to start with remarkably equivalent point is the exceptional details structures of the payload header in each BloodAlchemy and Deed RAT,” the business stated. “Some similarities have been discovered in the loading course of action of shellcode, and the DLL file used to go through the shellcode as properly.”

It truly is really worth noting that equally PlugX (Korplug) and ShadowPad (aka PoisonPlug) have been extensively used by China-nexus hacking teams around the yrs.
The disclosure arrives as a China-joined danger actor regarded as Sharp Dragon (earlier Sharp Panda) has expanded their targeting to contain governmental companies in Africa and the Caribbean as section of an ongoing cyber espionage marketing campaign.
Uncovered this posting intriguing? Comply with us on Twitter and LinkedIn to read much more unique material we article.
Some components of this posting are sourced from:
thehackernews.com

 Ransomware Attacks Exploit VMware ESXi Vulnerabilities in Alarming Pattern
Ransomware Attacks Exploit VMware ESXi Vulnerabilities in Alarming Pattern