The North Korean espionage-centered actor acknowledged as Kimsuky has been observed utilizing 3 various Android malware strains to focus on customers found in its southern counterpart.
That is according to results from South Korean cybersecurity company S2W, which named the malware families FastFire, FastViewer, and FastSpy.
“The FastFire malware is disguised as a Google security plugin, and the FastViewer malware disguises itself as ‘Hancom Office Viewer,’ [while] FastSpy is a distant accessibility tool based on AndroSpy,” scientists Lee Sebin and Shin Yeongjae explained.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Kimsuky, also recognized by the names Black Banshee, Thallium, and Velvet Chollima, is considered to be tasked by the North Korean regime with a global intelligence-collecting mission, disproportionately focusing on individuals and companies in South Korea, Japan, and the U.S.
This previous August, Kaspersky unearthed a beforehand undocumented an infection chain dubbed GoldDragon to deploy a Windows backdoor capable of thieving facts from the victim this kind of as file lists, person keystrokes, and stored web browser login credentials.
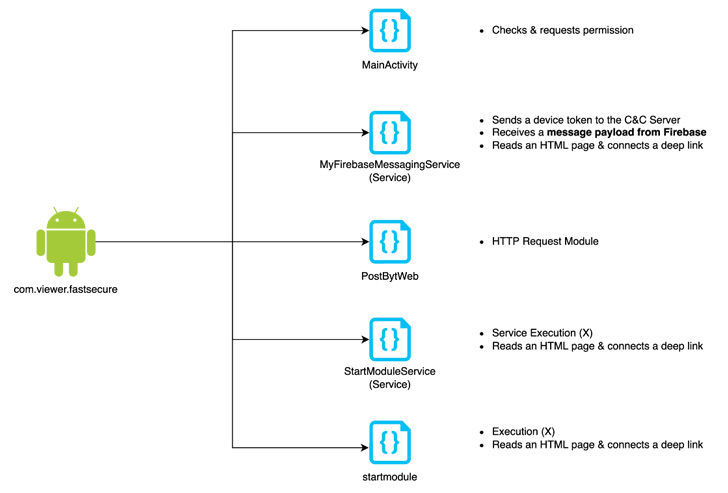
The innovative persistent risk is also recognized to an Android version of AppleSeed implant to execute arbitrary actions and exfiltrate data from the contaminated products.
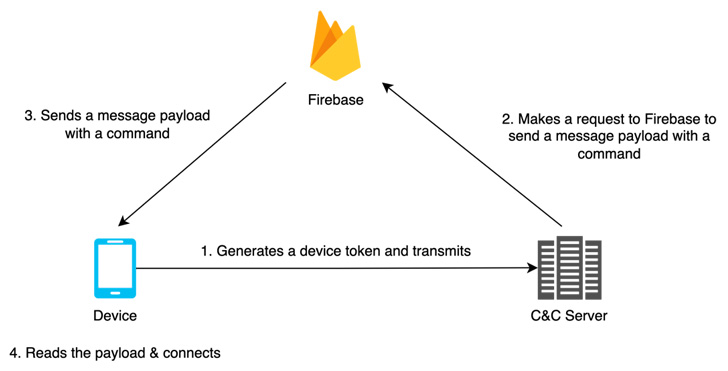
FastFire, FastViewer, and FastSpy are the most up-to-date additions to its evolving Android malware arsenal, which are made to acquire instructions from Firebase and down load supplemental payloads.
“FastViewer is a repackaged APK by adding arbitrary destructive code inserted by an attacker to the regular Hancom Place of work Viewer app,” the researchers stated, incorporating the malware also downloads FastSpy as a up coming-phase.
The rogue applications in problem are down below –
- com.viewer.fastsecure (Google 보안 Plugin)
- com.tf.thinkdroid.secviewer (FastViewer)
Both equally FastViewer and FastSpy abuse Android’s accessibility API permissions to satisfy its spying behaviors, with the latter automating consumer clicks to grant alone considerable permissions in a method analogous to MaliBot.

FastSpy, after introduced, allows the adversary to seize control of the qualified devices, intercept phone phone calls and SMSes, keep track of users’ destinations, harvest files, seize keystrokes, and history information and facts from the phone’s digicam, microphone, and speaker.
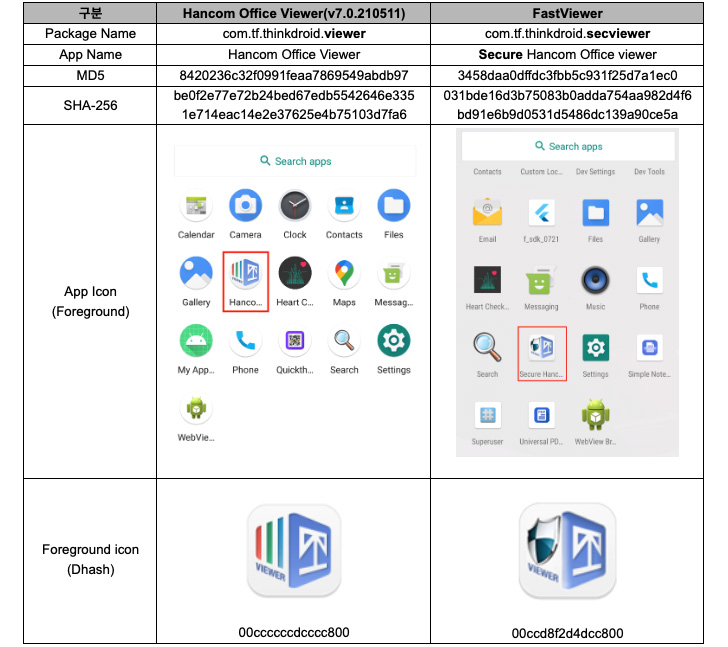
S2W’s attribution of the malware to Kimsuky is based on overlaps with a server domain named “mc.pzs[.]kr,” which was previously used in a Could 2022 marketing campaign recognized as orchestrated by the group to distribute malware disguised as North Korea linked press releases.
“Kimsuky team has constantly done attacks to steal the target’s information and facts focusing on cell units,” the researchers explained. “In addition, many attempts are currently being produced to bypass detection by customizing Androspy, an open up resource RAT.”
“Considering that Kimsuky group’s cell concentrating on approach is finding more highly developed, it is important to be mindful about subtle attacks targeting Android gadgets.”
Discovered this write-up exciting? Comply with THN on Fb, Twitter and LinkedIn to read much more exclusive articles we submit.
Some areas of this report are sourced from:
thehackernews.com


 Hive Ransomware Group Leaks Data Stolen in Tata Power Cyber-Attack
Hive Ransomware Group Leaks Data Stolen in Tata Power Cyber-Attack