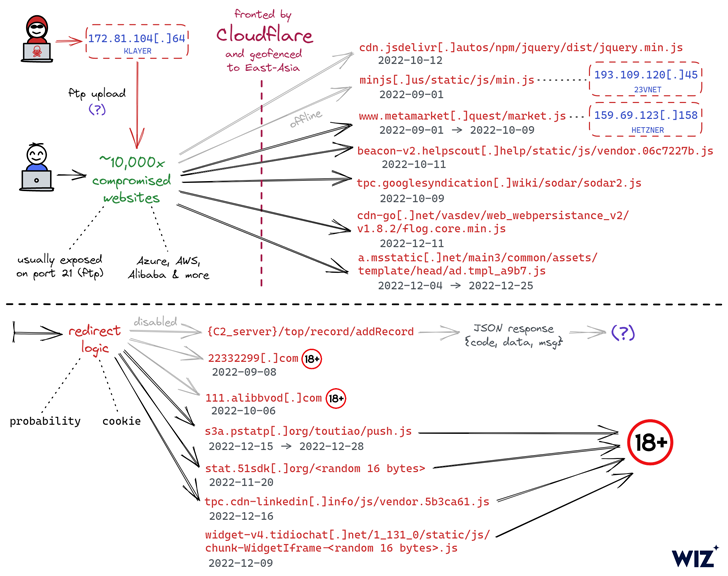
A common malicious cyber procedure has hijacked hundreds of web sites aimed at East Asian audiences to redirect website visitors to grownup-themed material since early September 2022.
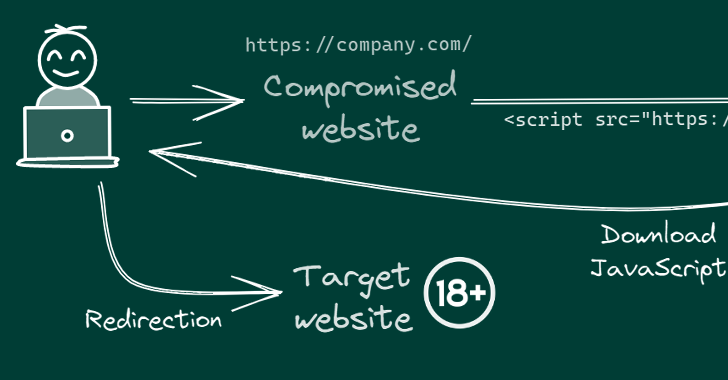
The ongoing marketing campaign involves injecting malicious JavaScript code to the hacked web-sites, typically connecting to the goal web server utilizing legitimate FTP credentials the threat actor beforehand acquired via an unfamiliar strategy.
“In several instances, these had been very safe vehicle-generated FTP credentials which the attacker was in some way in a position to receive and leverage for internet site hijacking,” Wiz explained in a report released this thirty day period.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The simple fact that the breached websites – owned by both of those compact corporations and multinational companies – utilize diverse tech stacks and hosting services companies has designed it challenging to trace a prevalent attack vector, the cloud security enterprise pointed out.
That getting stated, 1 of the typical denominators in between the websites is that a vast majority of them are both hosted in China or hosted in a diverse state but are primed for Chinese buyers.
What’s far more, the URLs hosting the rogue JavaScript code are geofenced to restrict its execution in specified East Asian nations.
There are also indications that the marketing campaign has established its sights on Android as nicely, with the redirection script top site visitors to gambling web-sites that urge them to put in an application (APK bundle identify “com.tyc9n1999co.coandroid”).
The identification of the threat actor is unknown as but, and even though their specific motives are still to be determined, it is suspected that the purpose is to have out advertisement fraud and Search engine marketing manipulation, or alternatively, travel inorganic website traffic to these internet websites.
WEBINARDiscover the Concealed Potential risks of 3rd-Party SaaS Apps
Are you aware of the hazards involved with 3rd-party application accessibility to your company’s SaaS applications? Be part of our webinar to learn about the types of permissions currently being granted and how to reduce risk.
RESERVE YOUR SEAT
An additional notable facet of the attacks is the absence of phishing, web skimming, or malware an infection.
“We remain uncertain as to how the threat actor has been getting first accessibility to so numerous web sites, and we have however to identify any major commonalities between the impacted servers other than their use of FTP,” scientists Amitai Cohen and Barak Sharoni said.
“Despite the fact that it truly is not likely that the risk actor is using a -working day vulnerability provided the apparently minimal sophistication of the attack, we are unable to rule this out as an solution.”
Located this short article attention-grabbing? Observe us on Twitter and LinkedIn to read through much more exceptional information we write-up.
Some pieces of this post are sourced from:
thehackernews.com

 An in-depth analysis of the Microsoft 365 threat landscape
An in-depth analysis of the Microsoft 365 threat landscape