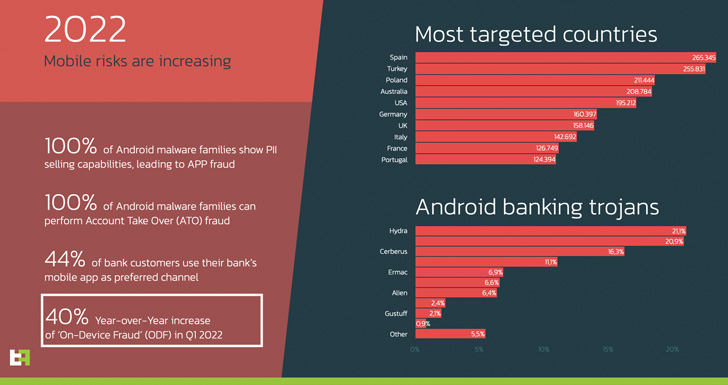
An examination of the cellular danger landscape in 2022 shows that Spain and Turkey are the most targeted nations for malware strategies, even as a blend of new and existing banking trojans are ever more concentrating on Android equipment to carry out on-machine fraud (ODF).
Other routinely focused nations around the world include things like Poland, Australia, the U.S., Germany, the U.K., Italy, France, and Portugal.
“The most worrying leitmotif is the growing consideration to On-Gadget Fraud (ODF),” Dutch cybersecurity organization ThreatFabric stated in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Just in the initial five months of 2022 there has been an improve of more than 40% in malware families that abuse Android OS to execute fraud making use of the system alone, generating it nearly unachievable to detect them making use of traditional fraud scoring engines.”

Hydra, FluBot (aka Cabassous), Cerberus, Octo, and ERMAC accounted for the most lively banking trojans based mostly on the amount of samples noticed in the course of the identical time period.

Accompanying this trend is the ongoing discovery of new dropper applications on Google Play Keep that appear less than the guise of seemingly innocuous productivity and utility purposes to distribute the malware –
- Nano Cleaner (com.casualplay.leadbro)
- QuickScan (com.zynksoftware.docuscanapp)
- Chrome (com.talkleadihr)
- Perform Retailer (com.girltold85)
- Pocket Screencaster (com.cutthousandjs)
- Chrome (com.biyitunixiko.populolo)
- Chrome (Cellular com.xifoforezuma.kebo)
- BAWAG PSK Security (com.qjlpfydjb.bpycogkzm)
What’s extra, on-product fraud — which refers to a stealthy method of initiating rogue transactions from victim’s units — has designed it feasible to use previously stolen qualifications to login to banking apps and have out economical transactions.
To make matters worse, the banking trojans have also been observed continually updating their abilities, with Octo devising an enhanced approach to steal credentials from overlay screens even ahead of they are submitted.
“This is done in purchase to be equipped to get the credentials even if [the] victim suspected one thing and closed the overlay devoid of basically urgent the fake ‘login’ current in the overlay website page,” the scientists described.
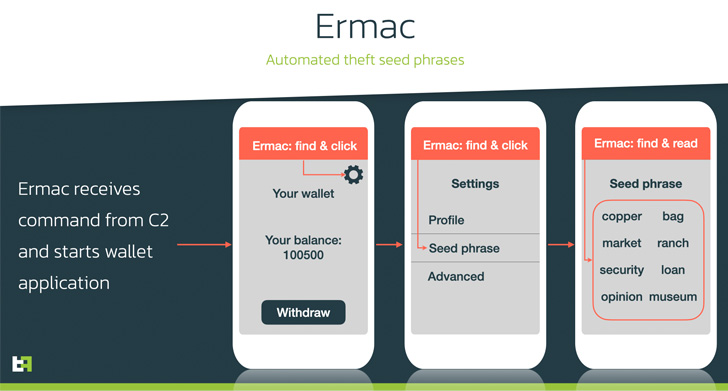
ERMAC, which emerged past September, has gained visible updates of its very own that enable it to siphon seed phrases from diverse cryptocurrency wallet applications in an automatic style by getting advantage of Android’s Accessibility Assistance.

Accessibility Company has been Android’s Achilles’ heel in new yrs, permitting menace actors to leverage the authentic API to provide unsuspecting consumers with pretend overlay screens and capture delicate info.
Previous 12 months, Google attempted to deal with the dilemma by making sure that “only services that are intended to enable people with disabilities access their unit or otherwise get over difficulties stemming from their disabilities are eligible to declare that they are accessibility instruments.”
But the tech huge is going a stage more in Android 13, which is at this time in beta, by proscribing API access for apps that the user has sideloaded from outdoors of an application keep, successfully building it tougher for probably harmful apps to misuse the company.
That said, ThreatFabric noted it was ready to bypass these limitations trivially by usually means of a tweaked set up course of action, suggesting the require for a additional stricter approach to counteract this kind of threats.
It is really recommended that people adhere to downloading apps from the Google Perform Retailer, prevent granting strange permissions to applications that have no intent asking for them (e.g., a calculator app inquiring to access call lists), and observe out for any phishing attempts aimed at setting up rogue applications.
“The openness of Android OS serves equally excellent and bad as malware carries on to abuse the legitimate capabilities, even though future restrictions appear to rarely interfere with the destructive intentions of this sort of apps,” the scientists explained.
Identified this article exciting? Stick to THN on Facebook, Twitter and LinkedIn to go through additional exceptional content material we write-up.
Some elements of this short article are sourced from:
thehackernews.com


 EnemyBot Malware Targets Web Servers, CMS Tools and Android OS
EnemyBot Malware Targets Web Servers, CMS Tools and Android OS