The North Korea-connected Lazarus Group has been observed weaponizing flaws in an undisclosed software to breach a fiscal enterprise entity in South Korea two times in a span of a year.
Even though the first attack in May possibly 2022 entailed the use of a vulnerable edition of a certificate computer software which is extensively applied by community institutions and universities, the re-infiltration in October 2022 associated the exploitation of a zero-day in the identical program.
Cybersecurity agency AhnLab Security Crisis Reaction Center (ASEC) claimed it is really refraining from mentioning the computer software owing to the reality that “the vulnerability has not been absolutely verified nonetheless and a software package patch has not been released.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The adversarial collective, right after obtaining an preliminary foothold by an unfamiliar technique, abused the zero-day bug to carry out lateral motion, soon following which the AhnLab V3 anti-malware engine was disabled by way of a BYOVD attack.
It’s value noting here that the Bring Your Have Susceptible Driver, aka BYOVD, technique has been regularly employed by the Lazarus Group in recent months, as documented by equally ESET and AhnLab in a sequence of stories late last 12 months.
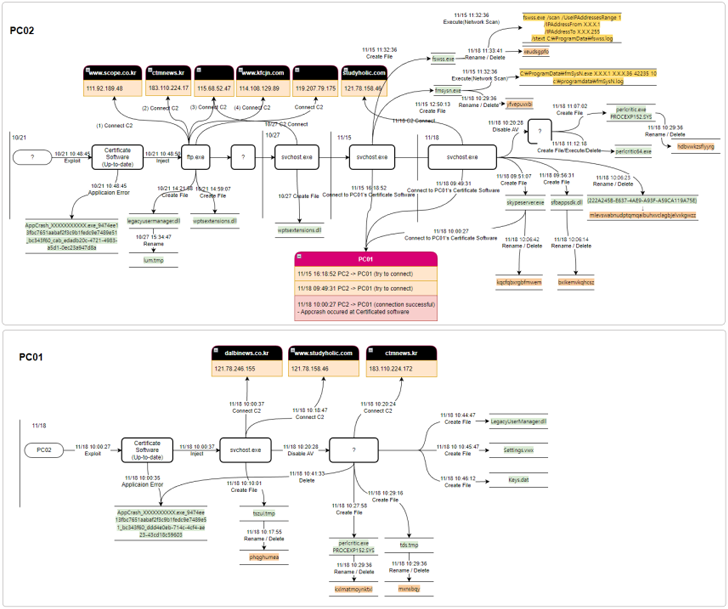
Amongst other ways to conceal its destructive habits consist of transforming file names prior to deleting them and modifying timestamps applying an anti-forensic strategy referred to as timestomping.
The attack in the end paved the way for a number of backdoor payloads (Keys.dat and Configurations.vwx) that are built to join to a remote command-and-manage (C2) server and retrieve extra binaries and execute them in a fileless method.
Learn the Most recent Malware Evasion Strategies and Avoidance Strategies
All set to bust the 9 most hazardous myths about file-centered attacks? Join our impending webinar and turn into a hero in the fight towards affected individual zero bacterial infections and zero-working day security occasions!
RESERVE YOUR SEAT
The development will come a 7 days following ESET lose light on a new implant referred to as WinorDLL64 that’s deployed by the notorious danger actor by usually means of a malware loader named Wslink.
“The Lazarus group is investigating the vulnerabilities of many other program and are consistently shifting their TTPs by altering the way they disable security solutions and have out anti-forensic approaches to interfere or delay detection and assessment in get to infiltrate Korean institutions and businesses,” ASEC claimed.
Uncovered this write-up attention-grabbing? Comply with us on Twitter and LinkedIn to read through additional unique information we post.
Some elements of this short article are sourced from:
thehackernews.com


 Government Claims New UK GDPR Will Save Firms Billions
Government Claims New UK GDPR Will Save Firms Billions