A new backdoor linked with a malware downloader named Wslink has been learned, with the software probably made use of by the notorious North Korea-aligned Lazarus Group, new results reveal.
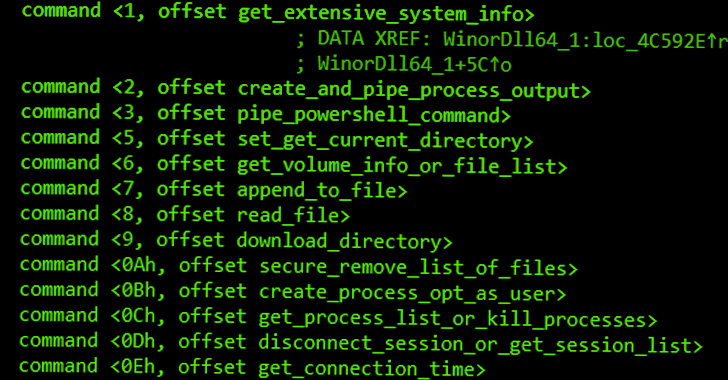
The payload, dubbed WinorDLL64 by ESET, is a fully-featured implant that can exfiltrate, overwrite, and delete data files execute PowerShell instructions and attain comprehensive info about the underlying device.
Its other attributes comprise listing energetic sessions, producing and terminating processes, enumerating drives, and compressing directories.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
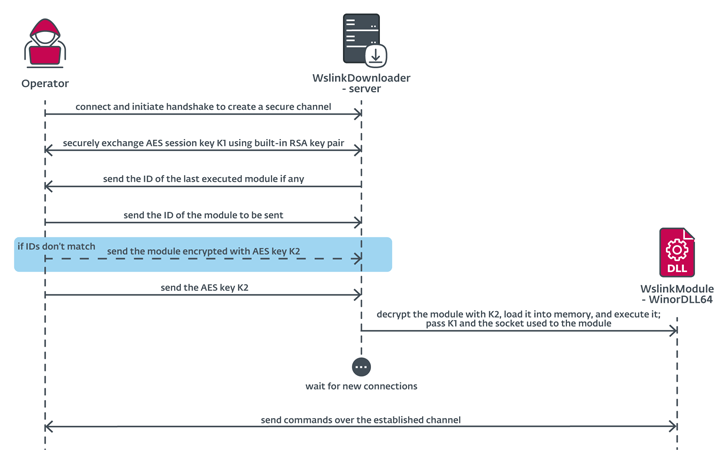
Wslink was to start with documented by the Slovak cybersecurity firm in October 2021, describing it as a “easy nevertheless amazing” malware loader that is capable of executing gained modules in memory.
“The Wslink payload can be leveraged later on for lateral motion, because of to its distinct interest in network sessions,” ESET researcher Vladislav Hrčka said. “The Wslink loader listens on a port specified in the configuration and can serve further connecting purchasers, and even load many payloads.”
Intrusions leveraging the malware are mentioned to be extremely focused owing to the reality that only a handful of detections have been observed to day in Central Europe, North The united states, and the Middle East.
In March 2022, ESET elaborated on the malware’s use of an “advanced multi-layered virtual machine” obfuscator to evade detection and resist reverse engineering.
The inbound links to Lazarus Group stem from overlaps in conduct and code to that of previous strategies – Procedure GhostSecret and Bankshot – which have been attributed to the advanced persistent risk.
This incorporates similarities with the GhostSecret samples in-depth by McAfee in 2018, which occur with a “knowledge-gathering and implant-installation ingredient” that operates as a service, mirroring the exact conduct of Wslink.
ESET said the payload was uploaded to the VirusTotal malware databases from South Korea, wherever some of the victims are located, incorporating credence to the Lazarus involvement.
The results are once once more demonstrative of the large arsenal of hacking tools utilized by the Lazarus Group to infiltrate its targets.
“Wslink’s payload is committed to furnishing suggests for file manipulation, execution of additional code, and getting substantial data about the fundamental method that possibly can be leveraged later for lateral movement,” ESET mentioned.
Uncovered this write-up appealing? Adhere to us on Twitter and LinkedIn to browse a lot more exceptional content we post.
Some elements of this article are sourced from:
thehackernews.com

 Belfast to house new ‘Cyber-AI Hub’ following £18.9 million government investment
Belfast to house new ‘Cyber-AI Hub’ following £18.9 million government investment