The North Korean risk actor recognized as the Lazarus Team has been noticed shifting its focus and quickly evolving its instruments and practices as part of a prolonged-working action called DeathNote.
Whilst the nation-point out adversary is regarded for its persistent attacks on the cryptocurrency sector, it has also targeted automotive, educational, and defense sectors in Jap Europe and other components of the entire world, in what is perceived as a “significant” pivot.
“At this issue, the actor switched all the decoy files to job descriptions associated to protection contractors and diplomatic solutions,” Kaspersky researcher Seongsu Park mentioned in an examination published Wednesday.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The deviation in targeting, along with the use of up-to-date infection vectors, is said to have happened in April 2020. It is really worthy of noting that the DeathNote cluster is also tracked less than the monikers Procedure Dream Work or NukeSped. Google-owned Mandiant also tied a subset of the exercise to a group it phone calls UNC2970.
The phishing attacks directed versus crypto corporations normally entail making use of bitcoin mining-themed lures in email messages to entice likely targets into opening macro-laced paperwork in get to drop the Manuscrypt (aka NukeSped) backdoor on the compromised equipment.
The focusing on of the automotive and tutorial verticals is tied to Lazarus Group’s broader attacks against the defense field, as documented by the Russian cybersecurity firm in October 2021, primary to the deployment of BLINDINGCAN (aka AIRDRY or ZetaNile) and COPPERHEDGE implants.
In an option attack chain, the threat actor used a trojanzied version of a legitimate PDF reader application referred to as SumatraPDF Reader to initiate its destructive schedule. The Lazarus Group’s use of rogue PDF reader applications was formerly discovered by Microsoft.
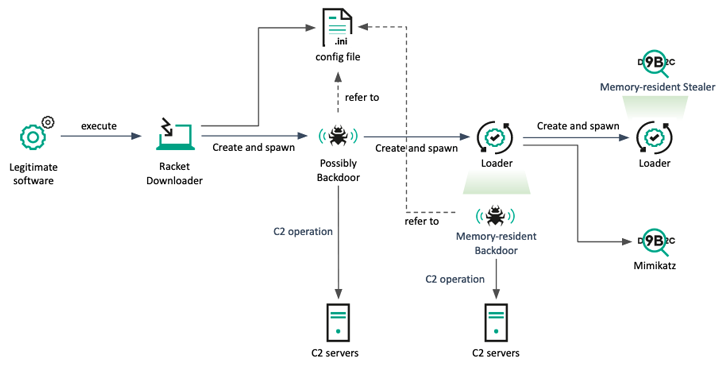
The targets of these attacks provided an IT asset checking answer seller based in Latvia and a assume tank found in South Korea, the latter of which entailed the abuse of legitimate security software program which is widely employed in the nation to execute the payloads.
Future WEBINARLearn to Safe the Identity Perimeter – Confirmed Approaches
Improve your small business security with our impending specialist-led cybersecurity webinar: Take a look at Identity Perimeter approaches!
Do not Pass up Out – Help save Your Seat!
The twin attacks “position to Lazarus building source chain attack abilities,” Kaspersky famous at the time. The adversarial crew has due to the fact been blamed for the source chain attack aimed at business VoIP service company 3CX that arrived to mild final month.
Kaspersky mentioned it found an additional attack in March 2022 that specific a number of victims in South Korea by exploiting the exact same security software to supply downloader malware able of providing a backdoor as perfectly as an data stealer for harvesting keystroke and clipboard facts.
“The newly implanted backdoor is capable of executing a retrieved payload with named-pipe interaction,” Park reported, including it is also “accountable for accumulating and reporting the victim’s information.”
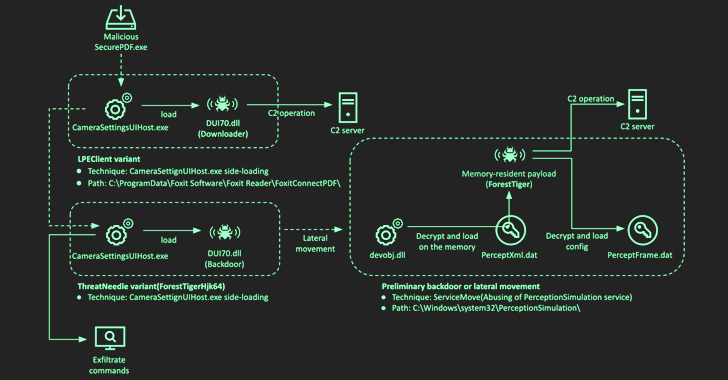
About the exact time, the exact backdoor is mentioned to have been used to breach a defense contractor in Latin America utilizing DLL aspect-loading approaches on opening a specially-crafted PDF file employing a trojanized PDF reader.
The Lazarus Group has also been connected to a thriving breach of another protection contractor in Africa last July in which a “suspicious PDF application” was sent about Skype to eventually drop a variant of a backdoor dubbed ThreatNeedle and yet another implant recognised as ForestTiger to exfiltrate details.
“The Lazarus group is a notorious and very skilled risk actor,” Park reported. “As the Lazarus group carries on to refine its techniques, it is critical for businesses to maintain vigilance and get proactive actions to protect against its destructive routines.”
Observed this short article interesting? Stick to us on Twitter and LinkedIn to browse extra special information we post.
Some areas of this post are sourced from:
thehackernews.com

 Rapid7 Has Good News for UK Security Posture
Rapid7 Has Good News for UK Security Posture