LinkedIn has develop into by considerably the most impersonated manufacturer for phishing attacks, according to new research by Check Place Research (CPR).
The cybersecurity vendor’s 2022 Q1 Brand Phishing Report revealed that phishing attacks impersonating the specialist social networking internet site made up over fifty percent (52%) of all tries globally in the first quarter of 2022. This represents a 44% maximize in comparison to the prior quarter, Q4 2021, when LinkedIn was the fifth most impersonated manufacturer.
CPR reported the results mirrored an rising development of social engineering ripoffs shifting absent from delivery firms and tech giants towards social media networks. In Q1 2022, social networks ended up the most qualified group, adopted by shipping.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Following LinkedIn, the most frequently impersonated models in phishing attacks had been DHL (14%), Google (7%), Microsoft (6%), FedEx (6%), WhatsApp (4%), Amazon (2%), Maersk (1%), AliExpress (.8%) and Apple (.8%).
Omer Dembinsky, data investigation group supervisor at Verify Stage Computer software, commented: “These phishing makes an attempt are attacks of option, basic and uncomplicated. Legal teams orchestrate these phishing makes an attempt on a grand scale, with a view to receiving as several folks to section with their particular facts as probable. Some attacks will attempt to attain leverage in excess of men and women or steal their details, these types of as those people we’re viewing with LinkedIn. Others will be tries to deploy malware on enterprise networks, this sort of as the pretend emails made up of spoof carrier files that we’re seeing with the likes of Maersk.
“If there was ever any doubt that social media would grow to be 1 of the most intensely focused sectors by prison teams, Q1 has laid those people uncertainties to rest. Even though Facebook has dropped out of the top 10 rankings, LinkedIn has soared to variety a single and has accounted for additional than 50 percent of all phishing makes an attempt so significantly this 12 months. The ideal protection against phishing threats, as ever, is information. Workers, in distinct, really should be skilled to location suspicious anomalies this sort of as misspelled domains, typos, incorrect dates and other particulars that can expose a malicious email or text message. LinkedIn people, in certain, really should be extra vigilant more than the study course of the future couple of months.”
CPR also furnished examples of phishing attacks it observed throughout Q1. In one particular of these, a malicious email was designed to steal the victim’s LinkedIn qualifications by engaging them to click on a destructive website link that redirects the user to a fraudulent LinkedIn login page.
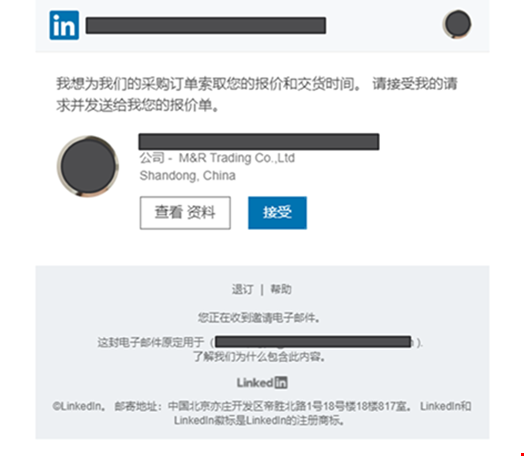 Malicious email instance
Malicious email instance
The new conclusions tie in with research conducted by Egress earlier this 12 months, which identified that email phishing attacks impersonating LinkedIn surged by 232% amid the ‘Great Resignation.’ In reaction, a LinkedIn spokesperson highlighted steps the company has set in area to safeguard its associates from these types of impersonation attacks: “Our internal groups operate to just take motion from all those who try to harm LinkedIn customers by way of phishing. We inspire customers to report suspicious messages and assist them find out much more about what they can do to defend on their own, which includes turning on two-action verification. To master a lot more about how customers can detect phishing messages, see our Assistance Center here.”
Some elements of this posting are sourced from:
www.infosecurity-journal.com


 New Lenovo UEFI Firmware Vulnerabilities Affect Millions of Laptops
New Lenovo UEFI Firmware Vulnerabilities Affect Millions of Laptops