The leak of the LockBit 3. ransomware builder final year has led to risk actors abusing the instrument to spawn new variants.
Russian cybersecurity corporation Kaspersky claimed it detected a ransomware intrusion that deployed a edition of LockBit but with a markedly unique ransom need procedure.
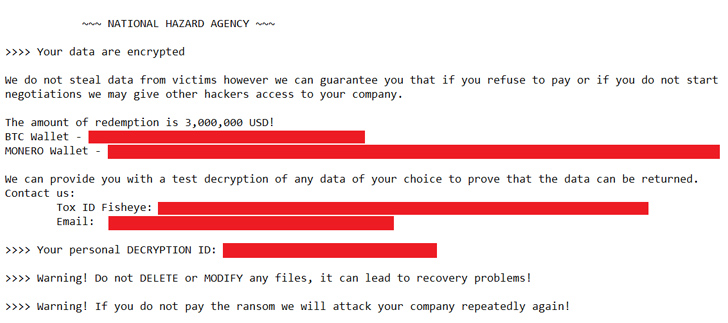
“The attacker driving this incident resolved to use a diverse ransom note with a headline associated to a beforehand unknown team, called National HAZARD Company,” security researchers Eduardo Ovalle and Francesco Figurelli mentioned.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The revamped ransom notice right specified the volume to be compensated to receive the decryption keys, and directed communications to a Tox company and email, as opposed to the LockBit team, which isn’t going to point out the amount and uses its individual conversation and negotiation platform.
Nationwide HAZARD Agency is far from the only cybercrime gang to use the leaked LockBit 3. builder. Some of the other menace actors recognized to leverage it incorporate Bl00dy and Buhti.
Kaspersky observed it detected a whole of 396 unique LockBit samples in its telemetry, of which 312 artifacts have been made applying the leaked builders. As numerous as 77 samples make no reference to “LockBit” in the ransom take note.
“Quite a few of the detected parameters correspond to the default configuration of the builder, only some have insignificant improvements,” the scientists mentioned. “This indicates the samples had been likely produced for urgent requires or probably by lazy actors.”
The disclosure arrives as Netenrich delved into a ransomware strain termed ADHUBLLKA that has rebranded several situations given that 2019 (Little bit, LOLKEK, OBZ, U2K, and TZW), though focusing on people today and small firms in trade for meager payouts in the selection of $800 to $1,600 from every single victim.

Whilst each of these iterations occur with slight modifications to encryption techniques, ransom notes, and conversation methods, a closer inspection has tied them all again to ADHUBLLKA owing to resource code and infrastructure similarities.
“When a ransomware is prosperous out in the wild, it is frequent to see cybercriminals use the identical ransomware samples — somewhat tweaking their codebase — to pilot other assignments,” security researcher Rakesh Krishnan mentioned.
“For example, they may adjust the encryption plan, ransom notes, or command-and-command (C2) interaction channels and then rebrand on their own as a ‘new’ ransomware.”
Ransomware continues to be an actively evolving ecosystem, witnessing recurrent shifts in strategies and focusing on to more and more target on Linux environments working with households these as Trigona, Monti, and Akira, the latter of which shares inbound links to Conti-affiliated danger actors.
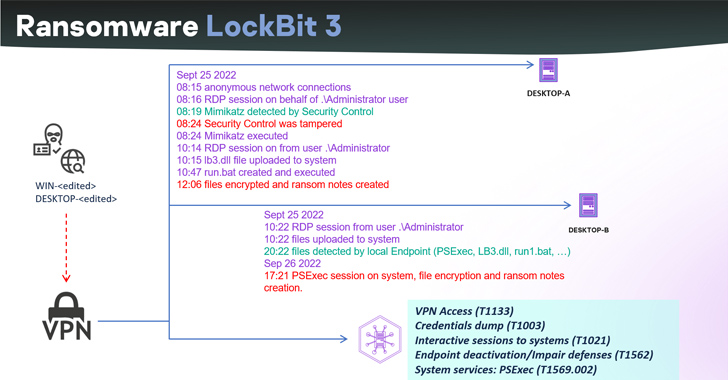
Akira has also been linked to attacks weaponizing Cisco VPN goods as an attack vector to acquire unauthorized entry to business networks. Cisco has since acknowledged that the risk actors are focusing on Cisco VPNs that are not configured for multi-factor authentication.
“The attackers frequently concentrate on the absence of or regarded vulnerabilities in multi-factor authentication (MFA) and regarded vulnerabilities in VPN software package,” the networking products big explained.
“After the attackers have acquired a foothold into a focus on network, they try out to extract qualifications as a result of LSASS (Area Security Authority Subsystem Service) dumps to aid even further motion within just the network and elevate privileges if needed.”
The development also will come amid a history surge in ransomware attacks, with the Cl0p ransomware team getting breached 1,000 identified organizations by exploiting flaws in MOVEit Transfer app to acquire first entry and encrypt focused networks.

U.S.-primarily based entities account for 83.9% of the corporate victims, adopted by Germany (3.6%), Canada (2.6%), and the U.K. (2.1%). A lot more than 60 million folks are reported to have been impacted by the mass-exploitation marketing campaign that began in May well 2023.
Nevertheless, the blast radius of the offer chain ransomware attack is possible to be a lot better. Estimates exhibit that the risk actors are anticipated to net illicit revenue in the range of $75 million to $100 million from their endeavors.
“While the MOVEit marketing campaign might conclude up impacting around 1,000 companies immediately, and an get of magnitude more indirectly, a extremely really little percentage of victims bothered hoping to negotiate, permit alone contemplated having to pay,” Coveware explained.
“Individuals that did pay, paid out substantially much more than prior CloP strategies, and a number of moments much more than the global Regular Ransom Amount of money of $740,144 (+126% from Q1 2023).”
What is far more, according to Sophos 2023 Active Adversary Report, the median dwell time for ransomware incidents dropped from nine days in 2022 to 5 days in the initially half of 2023, indicating that “ransomware gangs are transferring a lot quicker than at any time.”
In distinction, the median dwell time for non-ransomware incidents improved from 11 to 13 days. The optimum dwell time noticed in the course of the time period of time was 112 times.
“In 81% of ransomware attacks, the final payload was introduced outdoors of common doing the job hours, and for people that ended up deployed for the duration of enterprise hours, only five transpired on a weekday,” the cybersecurity business said. “Just about half (43%) of ransomware attacks were being detected on both Friday or Saturday.”
Located this article fascinating? Follow us on Twitter and LinkedIn to go through a lot more unique articles we post.
Some elements of this post are sourced from:
thehackernews.com

 Kroll Suffers Data Breach: Employee Falls Victim to SIM Swapping Attack
Kroll Suffers Data Breach: Employee Falls Victim to SIM Swapping Attack