Copycat web-sites for prompt messaging apps like Telegram and WhatApp are being applied to distribute trojanized versions and infect Android and Windows end users with cryptocurrency clipper malware.
“All of them are just after victims’ cryptocurrency resources, with various targeting cryptocurrency wallets,” ESET researchers Lukáš Štefanko and Peter Strýček explained in a new investigation.
Whilst the 1st occasion of clipper malware on the Google Perform Shop dates back to 2019, the advancement marks the 1st time Android-based mostly clipper malware has been crafted into prompt messaging applications.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“What’s more, some of these applications use optical character recognition (OCR) to acknowledge textual content from screenshots saved on the compromised products, which is yet another initially for Android malware.”
The attack chain begins with unsuspecting users clicking on fraudulent ads on Google search final results that lead to hundreds of sketchy YouTube channels, which then direct them to lookalike Telegram and WhatsApp websites.
What is novel about the most recent batch of clipper malware is that it is really able of intercepting a victim’s chats and replacing any sent and received cryptocurrency wallet addresses with addresses controlled by the menace actors.
An additional cluster of clipper malware will make use of OCR to locate and steal seed phrases by leveraging a reputable machine finding out plugin termed ML Kit on Android, thus producing it doable to vacant the wallets.
A 3rd cluster is developed to continue to keep tabs on Telegram conversations for particular Chinese keywords and phrases, equally really hard-coded and received from a server, relevant to cryptocurrencies, and if so, exfiltrate the comprehensive message, alongside with the username, group or channel name, to a distant server.
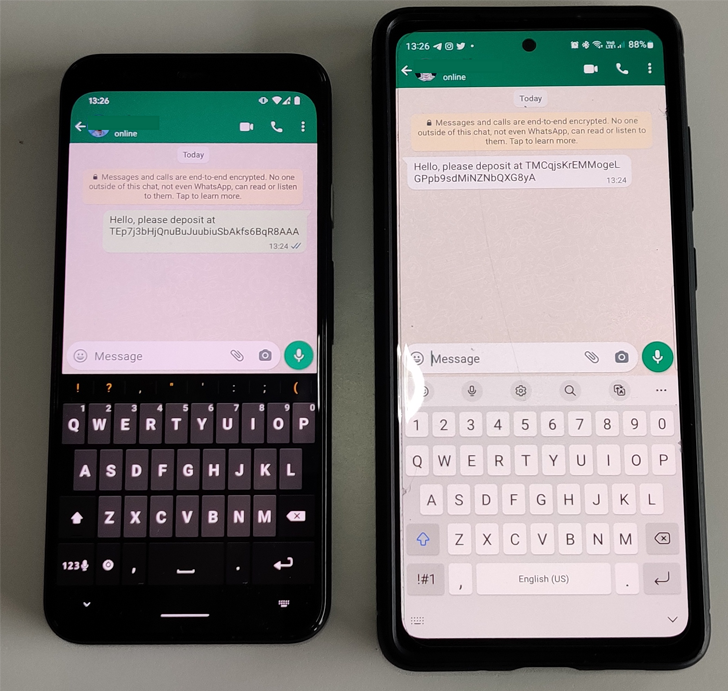
Last of all, a fourth set of Android clippers come with capabilities to swap the wallet handle as nicely as harvest system facts and Telegram details this sort of as messages and contacts.
The rogue Android APK deal names are outlined down below –
- org.telegram.messenger
- org.telegram.messenger.web2
- org.tgplus.messenger
- io.busniess.va.whatsapp
- com.whatsapp
ESET explained it also identified two Windows clusters, one particular which is engineered to swap wallet addresses and a next team that distributes remote accessibility trojans (RATs) in location of clippers to get manage of contaminated hosts and perpetrate crypto theft.
WEBINARDiscover the Hidden Dangers of Third-Party SaaS Applications
Are you informed of the dangers connected with 3rd-party application access to your company’s SaaS apps? Join our webinar to find out about the forms of permissions currently being granted and how to decrease risk.
RESERVE YOUR SEAT
All the analyzed RAT samples are dependent on the publicly available Gh0st RAT, barring a single, which employs more anti-investigation runtime checks all through its execution and works by using the HP-socket library to communicate with its server.
It can be also worth pointing out that these clusters, regardless of following a identical modus operandi, stand for disparate sets of exercise very likely formulated by distinctive threat actors.
The marketing campaign, like a very similar malicious cyber operation that came to light last 12 months, is geared in the direction of Chinese-speaking end users, primarily determined by the truth that both equally Telegram and WhatsApp are blocked in the state.
“Persons who want to use these products and services have to resort to oblique means of getting them,” the scientists said. “Unsurprisingly, this constitutes a ripe chance for cybercriminals to abuse the problem.”
Uncovered this article interesting? Stick to us on Twitter and LinkedIn to go through far more exceptional content we put up.
Some parts of this posting are sourced from:
thehackernews.com


 Russian Military Preparing New Destructive Attacks: Microsoft
Russian Military Preparing New Destructive Attacks: Microsoft