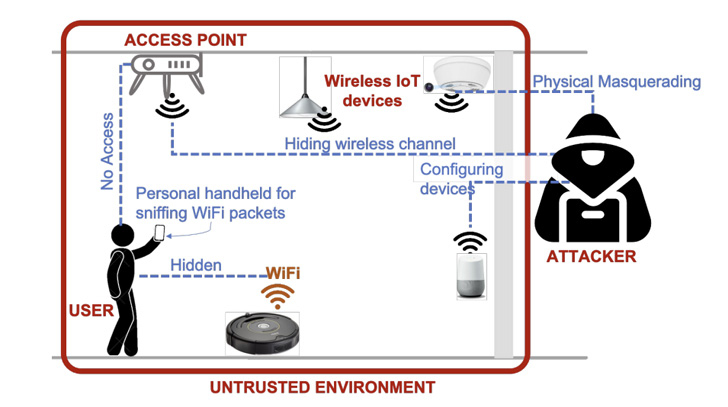
A group of academics has devised a process that can be applied on a phone or a laptop computer to determine and locate Wi-Fi-connected hidden IoT equipment in unfamiliar physical spaces.
With concealed cameras currently being more and more made use of to snoop on people today in hotel rooms and Airbnbs, the target is to be capable to pinpoint these types of rogue gadgets with no considerably of a problem.
The technique, dubbed Lumos, is created with this intent in thoughts and to “visualize their presence working with an augmented reality interface,” said Rahul Anand Sharma, Elahe Soltanaghaei, Anthony Rowe, and Vyas Sekar of Carnegie Mellon College in a new paper.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

At its main, the platform functions by snuffing and accumulating encrypted wi-fi packets more than the air to detect and recognize concealed equipment. Subsequently, it estimates the place of every single discovered device with regard to the consumer as they wander all around the perimeter of the place.
The localization module, for its portion, brings together signal strength measurements that are offered in 802.11 packets (aka Gained Signal Energy Indicator or RSSI) with relative consumer place identified by visible inertial odometry (VIO) facts on cellular telephones.
On Apple’s iOS gadgets, for instance, the positional monitoring is obtained by means of ARKit, a developer API that helps make it achievable to build augmented reality encounters by having gain of the phone’s digicam, CPU, GPU, and motion sensors.
“As the person walks closer to every device, the RSSI values corresponding to people info details maximize and then lessen as she walks away from the product,” the scientists mentioned. “Lumos leverages the spatial measurements of RSSI values and their variations to estimate the locale of every single product.”
What’s a lot more, Lumos can localize IoT gadgets irrespective of the user’s walking pace. Also integrated is a fingerprinting module that analyzes the captured 802.11 traffic designs using a device mastering model to determine the products primarily based on the MAC addresses.

The research evaluated Lumos across 44 distinctive IoT products spanning many types, types, and models throughout six different environments, finding that it can establish hidden equipment with 95% precision and track down them with a median mistake of 1.5m inside 30 minutes in a two-bedroom, 1000 sq.ft. condominium.
That stated, an superior attacker can leverage methods like MAC deal with randomization to evade detection and sidestep localization by arbitrarily modifying the devices’ transmit electric power.
“Lumos can most likely generalize throughout distinct gadget brands and products, as extensive as it has seen at the very least a single machine with very similar conduct in the teaching stage,” the researchers mentioned, pointing to how the process can even determine unprofiled devices.
Uncovered this short article interesting? Adhere to THN on Fb, Twitter and LinkedIn to examine far more special articles we write-up.
Some components of this short article are sourced from:
thehackernews.com


 Link Found Connecting Chaos, Onyx and Yashma Ransomware
Link Found Connecting Chaos, Onyx and Yashma Ransomware