A monetarily enthusiastic danger actor named Magnet Goblin is quickly adopting a single-working day security vulnerabilities into its arsenal in get to opportunistically breach edge equipment and general public-experiencing solutions and deploy malware on compromised hosts.
“Risk actor team Magnet Goblin’s hallmark is its means to quickly leverage recently disclosed vulnerabilities, notably targeting community-struggling with servers and edge gadgets,” Check out Point said.
“In some scenarios, the deployment of the exploits is inside 1 working day after a [proof-of-concept] is released, appreciably expanding the risk level posed by this actor.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

Attacks mounted by the adversary have leveraged unpatched Ivanti Join Safe VPN, Magento, Qlik Sense, and perhaps Apache ActiveMQ servers as an original infection vector to obtain unauthorized obtain. The team is said to be active since at the very least January 2022.
A prosperous exploitation is followed by the deployment of a cross-platform remote access trojan (RAT) dubbed Nerbian RAT, which was 1st disclosed by Proofpoint in Might 2022, as properly as its simplified variant identified as MiniNerbian. The use of the Linux edition of Nerbian RAT was beforehand highlighted by Darktrace.
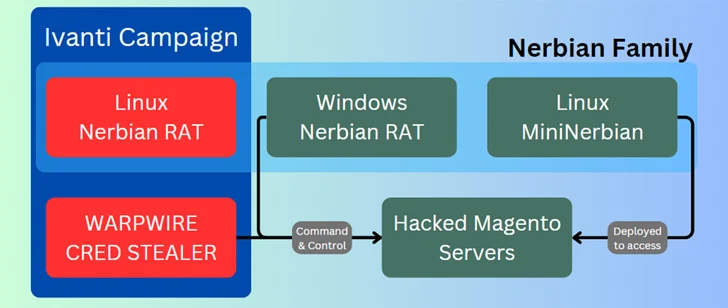
Both equally the strains make it possible for for execution of arbitrary instructions been given from a command-and-command (C2) server and exfiltrating the effects backed to it.
Some of the other applications applied by Magnet Goblin contain the WARPWIRE JavaScript credential stealer, the Go-primarily based tunneling computer software identified as Ligolo, and legit remote desktop offerings these kinds of as AnyDesk and ScreenConnect.

“Magnet Goblin, whose strategies surface to be fiscally determined, has been speedy to adopt 1-working day vulnerabilities to supply their customized Linux malware, Nerbian RAT and MiniNerbian,” the enterprise explained.
“These tools have operated under the radar as they primarily reside on edge-equipment. This is element of an ongoing pattern for threat actors to focus on regions which until now have been left unprotected.”
Found this write-up interesting? Abide by us on Twitter and LinkedIn to study a lot more exceptional content material we submit.
Some components of this short article are sourced from:
thehackernews.com


 Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets
Microsoft Confirms Russian Hackers Stole Source Code, Some Customer Secrets