Buyers of Metabase, a well-liked small business intelligence and details visualization software package deal, are being suggested to update to the most current variation following the discovery of an “exceptionally critical” flaw that could final result in pre-authenticated distant code execution on influenced installations.
Tracked as CVE-2023-38646, the issue impacts open-source editions prior to .46.6.1 and Metabase Business versions prior to 1.46.6.1.
“An unauthenticated attacker can operate arbitrary instructions with the identical privileges as the Metabase server on the server you are running Metabase on,” Metabase stated in an advisory released final week.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The issue has also been tackled in the pursuing older versions –
- .45.4.1 and 1.45.4.1
- .44.7.1 and 1.44.7.1, and
- .43.7.2 and 1.43.7.2
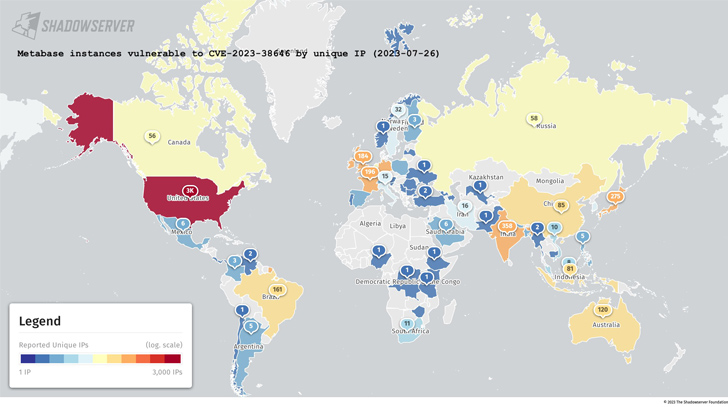
Whilst there is no proof that the issue has been exploited in the wild, details gathered by the Shadowserver Basis reveals that 5,488 out of the complete 6,936 Metabase cases are vulnerable as of July 26, 2023. A vast majority of the occasions are found in the U.S., India, Germany, France, the U.K., Brazil, and Australia.
Approaching WEBINARShield Versus Insider Threats: Grasp SaaS Security Posture Administration
Worried about insider threats? We have obtained you coated! Be part of this webinar to explore practical tactics and the tricks of proactive security with SaaS Security Posture Management.
Be a part of These days
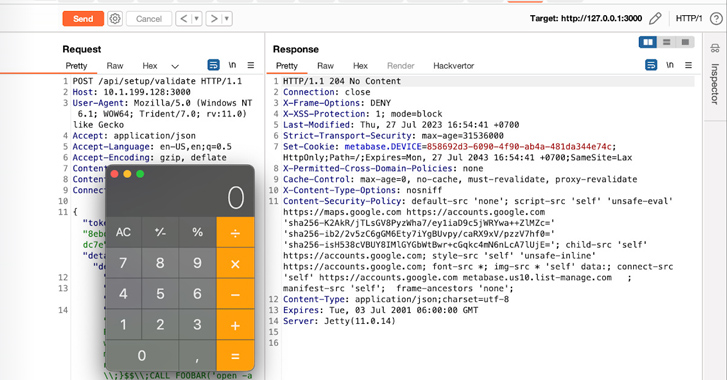
Assetnote, which claimed it learned and noted the bug to Metabase, stated the vulnerability is thanks to a JDBC connection issue in the API endpoint “/api/setup/validate,” enabling a destructive actor to receive a reverse shell on the technique by signifies of a specially crafted request that takes advantage of an SQL injection flaw in the H2 databases driver.
Customers who cannot use the patches promptly are advised to block requests to the /api/setup endpoint, isolate the Metabase occasion from your generation network, and observe for suspicious requests to the endpoint in problem.
Discovered this article interesting? Follow us on Twitter and LinkedIn to read extra unique material we write-up.
Some sections of this report are sourced from:
thehackernews.com

 Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches
Cybersecurity Agencies Warn Against IDOR Bugs Exploited for Data Breaches