Threat actors are leveraging a procedure referred to as versioning to evade Google Perform Store’s malware detections and focus on Android people.
“Campaigns using versioning typically concentrate on users’ credentials, info, and funds,” Google Cybersecurity Motion Team (GCAT) stated in its August 2023 Risk Horizons Report shared with The Hacker News.
Although versioning is not a new phenomenon, it truly is sneaky and really hard to detect. In this approach, a developer releases an initial version of an application on the Enjoy Shop that passes Google’s pre-publication checks, but is later on up to date with a malware ingredient.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This is realized by pushing an update from an attacker-controlled server to provide destructive code on the conclusion user system using a technique known as dynamic code loading (DCL), properly turning the app into a backdoor.

Before this May, ESET discovered a monitor recording application named “iRecorder – Screen Recorder” that remained innocuous for almost a calendar year immediately after it was very first uploaded to the Engage in Retail outlet right before malicious alterations ended up launched sneakily to spy on its buyers.
An additional illustration of malware working with the DCL method is SharkBot, which has repeatedly produced an physical appearance on the Perform Retail store by masquerading as security and utility applications.
SharkBot is a financial trojan that initiates unauthorized money transfers from compromised gadgets applying the Automated Transfer Assistance (ATS) protocol.
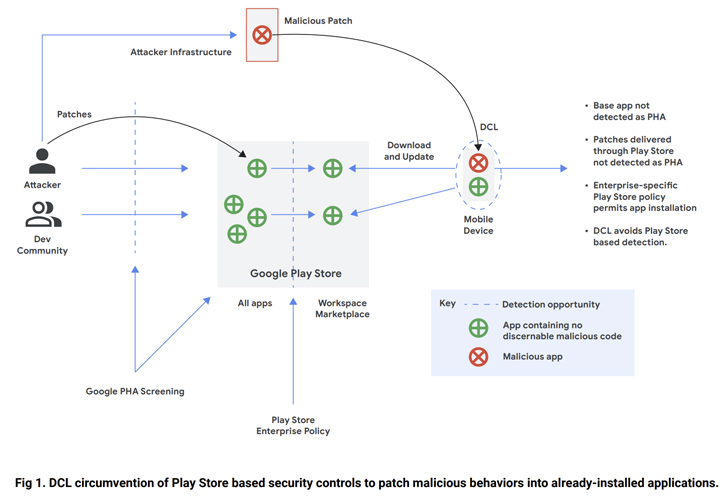
Dropper purposes that look on the storefront appear with lowered features that, when installed by the victims, down load a comprehensive model of the malware in a bid to catch the attention of less awareness.
“In an organization ecosystem, versioning demonstrates a will need for defense-in-depth principles, together with but not confined to restricting application installation sources to trustworthy sources these types of as Google Engage in or handling corporate devices through a cell gadget management (MDM) platform,” the company mentioned.
The conclusions arrive as ThreatFabric uncovered that malware purveyors have been exploiting a bug in Android to move off malicious applications as benign by “corrupting elements of an application” this sort of that the application as a total remains legitimate, in accordance to KrebsOnSecurity.

“Actors can have many applications printed in the retailer at the same time less than diverse developer accounts, however, only a person is performing as destructive, whilst the other is a backup to be utilized soon after takedown,” the Dutch cybersecurity corporation famous in June.
“This sort of a tactic will help actors to manage very lengthy campaigns, minimizing the time wanted to publish yet another dropper and proceed the distribution marketing campaign.”
To mitigate any opportunity threats, it’s suggested that Android buyers stick to reliable sources for downloading apps and enable Google Enjoy Defend to obtain notifications when a possibly hazardous app (PHA) is found on the machine.
Uncovered this write-up interesting? Abide by us on Twitter and LinkedIn to go through more distinctive content material we put up.
Some elements of this short article are sourced from:
thehackernews.com


 New Version of Rilide Data Theft Malware Adapts to Chrome Extension Manifest V3
New Version of Rilide Data Theft Malware Adapts to Chrome Extension Manifest V3