Menace hunters have discovered a suspicious offer in the NuGet bundle manager which is likely designed to target developers working with resources designed by a Chinese business that specializes in industrial- and electronic gear manufacturing.
The package in query is SqzrFramework480, which ReversingLabs reported was initially published on January 24, 2024. It has been downloaded 2,999 instances as of writing.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The software package source chain security firm explained it did not come across any other deal that exhibited equivalent habits.
It, nevertheless, theorized the campaign could possible be utilized for orchestrating industrial espionage on systems geared up with cameras, device vision, and robotic arms.

The indicator that SqzrFramework480 is seemingly tied to a Chinese organization named Bozhon Precision Industry Technology Co., Ltd. will come from the use of a edition of the firm’s brand for the package’s icon. It was uploaded by a Nuget person account identified as “zhaoyushun1999.”
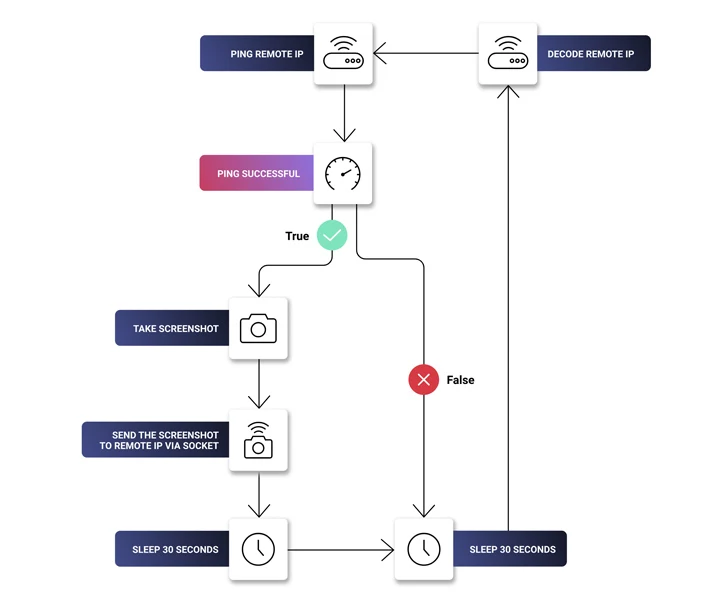
Current within the library is a DLL file “SqzrFramework480.dll” that comes with features to consider screenshots, ping a distant IP tackle right after every single 30 seconds until finally the procedure is successful, and transmit the screenshots above a socket established and connected to stated IP deal with.
“None of those behaviors are resolutely destructive. Having said that, when taken alongside one another, they increase alarms,” security researcher Petar Kirhmajer reported. “The ping serves as a heartbeat test to see if the exfiltration server is alive.”
The destructive use of sockets for facts interaction and exfiltration has been observed in the wild beforehand, as in the situation of the npm package nodejs_net_server.
The precise motive guiding the offer is unclear as however, though it truly is a acknowledged reality that adversaries are steadily resorting to concealing nefarious code in seemingly benign computer software to compromise victims.

An alternate, innocuous explanation could be that the bundle was leaked by a developer or a third party that works with the firm.
“They could also describe seemingly destructive steady display screen capture habits: it could basically be a way for a developer to stream pictures from the digital camera on the primary watch to a worker station,” Kirhmajer claimed.
The ambiguity surrounding the deal apart, the results underscore the intricate mother nature of source chain threats, generating it imperative that buyers scrutinize libraries prior to downloading them.
“Open up-resource repositories like NuGet are more and more hosting suspicious and destructive offers developed to bring in developers and trick them into downloading and incorporating malicious libraries and other modules into their growth pipelines,” Kirhmajer stated.
Identified this short article fascinating? Abide by us on Twitter and LinkedIn to browse extra exclusive written content we publish.
Some pieces of this article are sourced from:
thehackernews.com


 U.S. Charges 7 Chinese Nationals in Major 14-Year Cyber Espionage Operation
U.S. Charges 7 Chinese Nationals in Major 14-Year Cyber Espionage Operation