Cybersecurity scientists have uncovered a new established of destructive deals revealed to the NuGet package deal manager using a lesser-acknowledged process for malware deployment.
Software provide chain security organization ReversingLabs explained the campaign as coordinated and ongoing since August 1, 2023, even though linking it to a host of rogue NuGet packages that have been observed delivering a remote obtain trojan known as SeroXen RAT.
“The danger actors guiding it are tenacious in their wish to plant malware into the NuGet repository, and to continually publish new destructive packages,” Karlo Zanki, reverse engineer at ReversingLabs, claimed in a report shared with The Hacker Information.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The names of some of the offers are beneath –
- Pathoschild.Stardew.Mod.Make.Config
- KucoinExchange.Net
- Kraken.Trade
- DiscordsRpc
- SolanaWallet
- Monero
- Modern.Winform.UI
- MinecraftPocket.Server
- IAmRoot
- ZendeskApi.Shopper.V2
- Betalgo.Open up.AI
- Forge.Open up.AI
- Pathoschild.Stardew.Mod.BuildConfig
- CData.NetSuite.Net.Framework
- CData.Salesforce.Net.Framework
- CData.Snowflake.API
These offers, which span numerous versions, imitate well known offers and exploit NuGet’s MSBuild integrations characteristic in order to implant destructive code on their victims, a element called inline responsibilities to attain code execution.
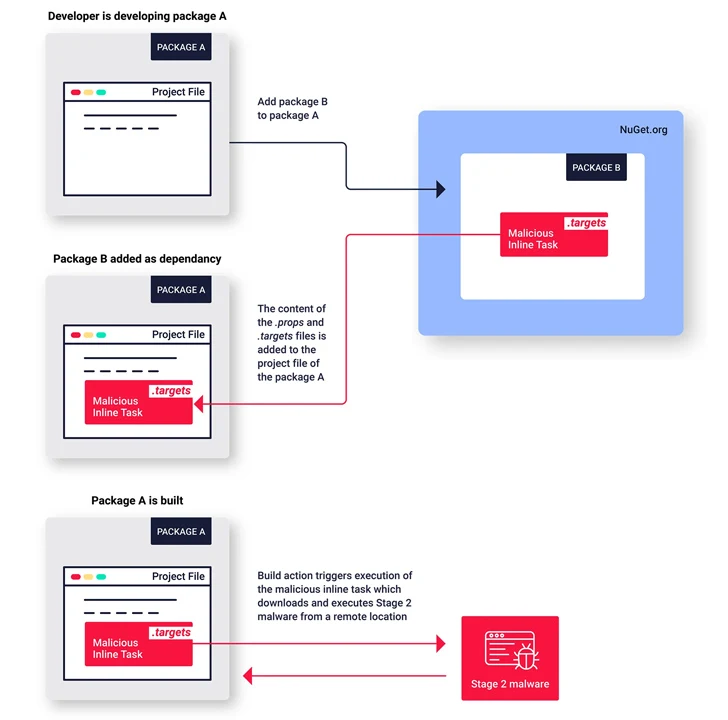
“This is the initially acknowledged example of malware published to the NuGet repository exploiting this inline jobs attribute to execute malware,” Zanki claimed.
The now-taken off packages show very similar qualities in that the menace actors behind the operation tried to conceal the malicious code by making use of areas and tabs to transfer it out of see of the default monitor width.
As beforehand disclosed by Phylum, the packages also have artificially inflated downloaded counts to make them surface a lot more reputable. The final goal of the decoy deals is to act as a conduit for retrieving a next-phase .NET payload hosted on a throwaway GitHub repository.
“The risk actor at the rear of this marketing campaign is being very careful and having to pay awareness to information, and is determined to keep this malicious campaign alive and lively,” Zanki explained.
Found this short article interesting? Follow us on Twitter and LinkedIn to read through extra exceptional content we post.
Some elements of this post are sourced from:
thehackernews.com


 PentestPad: Platform for Pentest Teams
PentestPad: Platform for Pentest Teams