Information have emerged about a malvertising marketing campaign that leverages Google Advertisements to direct users looking for common program to fictitious landing web pages and distribute up coming-phase payloads.
Malwarebytes, which learned the action, said it really is “one of a kind in its way to fingerprint customers and distribute time sensitive payloads.”
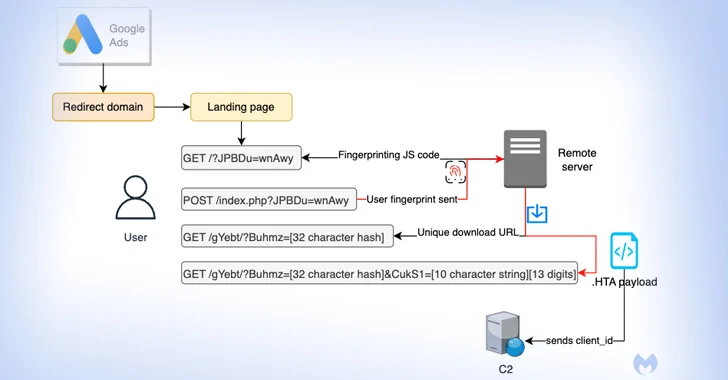
The attack singles out buyers browsing for Notepad++ and PDF converters to serve bogus adverts on the Google look for results webpage that, when clicked, filters out bots and other unintended IP addresses by displaying a decoy website.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Need to the customer be deemed of interest to the menace actor, the sufferer is redirected to a replica web-site promoting the application, while silently fingerprinting the technique to identify if the ask for is originating from a virtual device.
Users who are unsuccessful the check out are taken to the respectable Notepad++ internet site, even though a probable goal is assigned a exclusive ID for “monitoring functions but also to make every single download exceptional and time sensitive.”

The last-stage malware is an HTA payload that establishes a connection to a distant domain (“mybigeye[.]icu”) on a customized port and serves abide by-on malware.
“Risk actors are successfully making use of evasion approaches that bypass ad verification checks and permit them to goal sure varieties of victims,” Jérôme Segura, director of threat intelligence, reported.

“With a dependable malware delivery chain in hand, destructive actors can aim on improving their decoy web pages and craft tailor made malware payloads.”
The disclosure overlaps with a similar marketing campaign that targets buyers looking for the KeePass password manager with destructive adverts that immediate victims to a area utilizing Punycode (keepass[.]information vs ķeepass[.]data), a particular encoding applied to convert Unicode characters to ASCII.
“Persons who simply click on the advert will be redirected by using a cloaking company that is meant to filter sandboxes, bots and everyone not considered to be a real target,” Segura famous. “The danger actors have set up a non permanent domain at keepasstacking[.]web-site that performs the conditional redirect to the ultimate destination.”

Buyers who land on the decoy web site are tricked into downloading a malicious installer that in the end leads to the execution of FakeBat (aka EugenLoader), a loader engineered to download other destructive code.
The abuse of Punycode is not solely novel, but combining it with rogue Google Adverts is a indication that malvertising by way of search engines is getting extra complex. By employing Punycode to register identical area names as genuine website, the intention is to pull off a homograph attack and entice victims into setting up malware.

“Even though Punycode with internationalized domain names has been employed for years by danger actors to phish victims, it shows how effective it remains in the context of brand impersonation by way of malvertising,” Segura mentioned.
Speaking of visual trickery, multiple threat actors – TA569 (aka SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), ClearFake, and EtherHiding – have been observed getting gain of themes linked to fake browser updates to propagate Cobalt Strike, loaders, stealers, and distant accessibility trojans, a signal that these attacks are a continual, evolving menace.
“Phony browser updates abuse conclude consumer belief with compromised web sites and a lure personalized to the user’s browser to legitimize the update and fool people into clicking,” Proofpoint researcher Dusty Miller claimed in an examination posted this week.
“The threat is only in the browser and can be initiated by a click on from a legit and envisioned email, social media web page, lookup engine question, or even just navigating to the compromised site.”
Discovered this post interesting? Observe us on Twitter and LinkedIn to read through additional special articles we put up.
Some parts of this post are sourced from:
thehackernews.com

 Vietnamese Hackers Target U.K., U.S., and India with DarkGate Malware
Vietnamese Hackers Target U.K., U.S., and India with DarkGate Malware