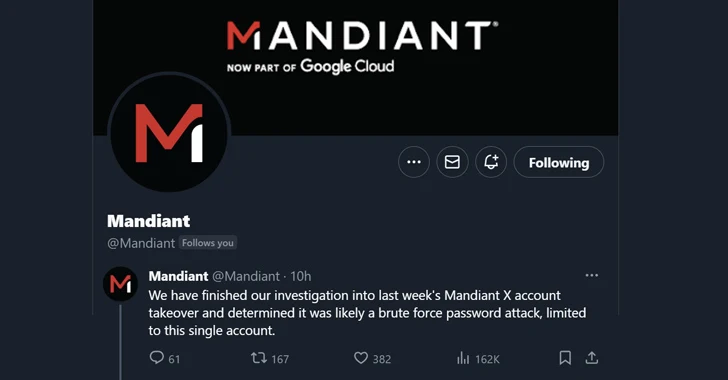
The compromise of Mandiant’s X (formerly Twitter) account previous 7 days was most likely the end result of a “brute-drive password attack,” attributing the hack to a drainer-as-a-provider (DaaS) group.
“Generally, [two-factor authentication] would have mitigated this, but thanks to some workforce transitions and a improve in X’s 2FA plan, we had been not adequately protected,” the risk intelligence organization explained in a write-up shared on X.
The attack, which took area on January 3, 2023, enabled the danger actor to consider handle of the firm’s X account and distribute links to a phishing site hosting a cryptocurrency drainer tracked as CLINKSINK.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Drainers refer to malicious scripts and intelligent contracts that facilitate the theft of digital assets from the victim’s wallets immediately after they are tricked into approving the transactions.

In accordance to the Google-owned subsidiary, many menace actors are believed to have leveraged CLINKSINK since December 2023 to siphon cash and tokens from Solana (SOL) cryptocurrency people.
As noticed in the circumstance of other drainers like Angel Drainer and Inferno Drainer, affiliate marketers are roped in by the DaaS operators to perform the attacks in exchange for a reduce (normally 20%) of the stolen belongings.
The determined exercise cluster entails at the very least 35 affiliate IDs and 42 one of a kind Solana wallet addresses, collectively netting the actors no a lot less than $900,000 in unlawful income.
The attack chains contain the use of social media and chat programs this kind of as X and Discord to distribute cryptocurrency-themed phishing internet pages that persuade the targets to connect their wallets to assert a bogus token airdrop.
“Just after connecting their wallet, the target is then prompted to indicator a transaction to the drainer support, which lets it to siphon resources from the sufferer,” security scientists Zach Riddle, Joe Dobson, Lukasz Lamparski, and Stephen Eckels said.
CLINKSINK, a JavaScript drainer, is intended to open up a pathway to the qualified wallets, verify the present equilibrium on the wallet, and finally pull off the theft after asking the target to signal a fraudulent transaction. This also indicates that the tried theft will not thrive if the victim rejects the transaction.
The drainer has also spawned quite a few variants, like Chick Drainer (or Rainbow Drainer), raising the risk that the supply code is out there to many danger actors, enabling them to mount unbiased draining campaigns.
“The huge availability and very low cost of quite a few drainers, combined with a fairly high potential for financial gain, possible would make them interesting functions for numerous fiscally inspired actors,” Mandiant explained.

“Offered the enhance in cryptocurrency values and the very low barrier to entry for draining functions, we foresee that monetarily motivated risk actors of different degrees of sophistication will proceed to carry out drainer operations for the foreseeable long run.”
The progress comes amid an uptick in attacks targeting genuine X accounts to distribute cryptocurrency cons.
Earlier this 7 days, the X account affiliated with the U.S. Securities and Exchange Fee (SEC) was breached to falsely claim that the regulatory human body experienced authorised the “listing and trading of location bitcoin trade-traded solutions,” causing bitcoin charges to spike briefly.
X has since unveiled the hack was the end result of “an unidentified specific obtaining command above a phone range linked with the @SECGov account by way of a third-party,” and that the account did not have two-factor authentication enabled.
Found this report appealing? Abide by us on Twitter and LinkedIn to study much more unique articles we write-up.
Some elements of this short article are sourced from:
thehackernews.com

 Chinese Hackers Exploit Zero-Day Flaws in Ivanti Connect Secure and Policy Secure
Chinese Hackers Exploit Zero-Day Flaws in Ivanti Connect Secure and Policy Secure