Researchers have shut down an “expansive” advert fraud scheme that spoofed extra than 1,700 programs from 120 publishers and impacted roughly 11 million equipment.
“VASTFLUX was a malvertising attack that injected destructive JavaScript code into digital ad creatives, making it possible for the fraudsters to stack various invisible video clip ad players guiding just one a further and sign-up advert sights,” fraud prevention firm HUMAN said.
The procedure will get its title from the use of a DNS evasion procedure named Rapidly Flux and Wide, a Electronic Video clip Advertisement Serving Template which is used to provide ads to movie players.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The innovative operation specifically exploited the restricted in-app environments that operate advertisements on iOS to spot bids for exhibiting advert banners. Really should the auction be won, the hijacked ad slot is leveraged to inject rogue JavaScript that establishes get in touch with with a distant server to retrieve the list of apps to be specific.
The features the bundle IDs that belong to legit applications so as to perform what’s known as as an application spoofing attack, in which a fraudulent app passes off as a really-regarded app in an attempt to trick advertisers into bidding for the advert house.
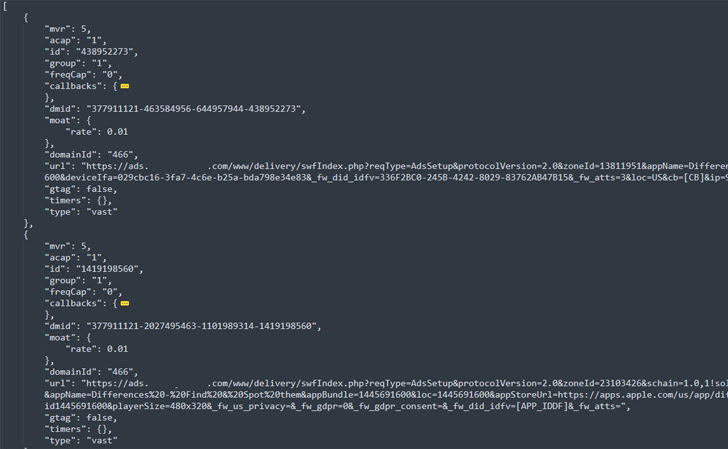
The best objective, for each HUMAN, was to sign-up views for as several as 25 movie adverts by layering them atop one particular another in a method which is absolutely invisible to the buyers and generates illicit earnings.
“It does not quit with the stacked advertisements, while,” the organization explained. “For as several of those people as could be rendering on a user’s machine at as soon as, they hold loading new adverts until finally the ad slot with the destructive ad code is closed.”
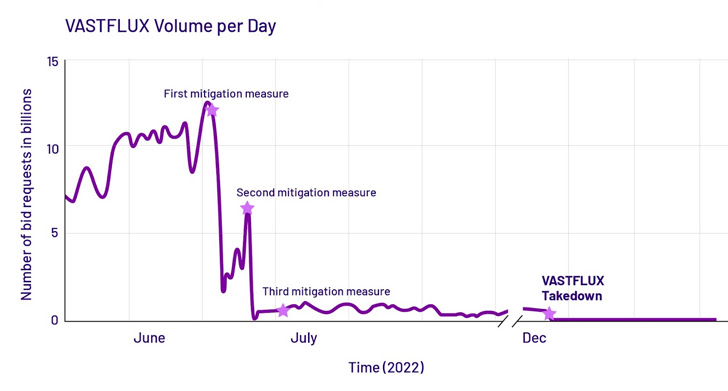
“The actors guiding the VASTFLUX scheme obviously have an personal comprehending of the electronic promoting ecosystem,” it more included, stating the campaign also rendered an countless “playlist” of advertisements to defraud equally the promoting organizations and applications that exhibit ads.
The takedown of VASTFLUX arrives three months soon after the disruption of Scylla, a fraud operation focusing on promotion software development kits (SDKs) inside of 80 Android applications and 9 iOS apps printed on the formal storefronts.
VASTFLUX, which created around 12 billion bid requests for every day at its peak, is only the latest in a extend of advert fraud botnets that have been shuttered in modern a long time, soon after 3ve, PARETO, and Methbot.
Located this short article attention-grabbing? Adhere to us on Twitter and LinkedIn to read additional exceptional information we post.
Some areas of this posting are sourced from:
thehackernews.com

 The Cookie Law is finally crumbling – good riddance
The Cookie Law is finally crumbling – good riddance