The risk actors behind the black hat redirect malware marketing campaign have scaled up their campaign to use a lot more than 70 bogus domains mimicking URL shorteners and contaminated about 10,800 websites.
“The principal aim is nevertheless advert fraud by artificially growing targeted traffic to web pages which contain the AdSense ID which comprise Google adverts for revenue era,” Sucuri researcher Ben Martin explained in a report revealed previous 7 days.
Information of the malicious activity ended up first uncovered by the GoDaddy-owned business in November 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The marketing campaign, which is claimed to have been active since September final calendar year, is orchestrated to redirect people to compromised WordPress web pages to phony Q&A portals. The purpose, it appears, is to boost the authority of spammy web sites in search motor success.
“It can be feasible that these poor actors are merely attempting to influence Google that true individuals from different IPs using distinctive browsers are clicking on their search benefits,” Sucuri mentioned at the time. “This system artificially sends Google signals that those people webpages are performing properly in lookup.”
What will make the newest marketing campaign major is the use of Bing lookup consequence backlinks and Twitter’s website link shortener (t[.]co) support, along with Google, in their redirects, indicating an enlargement of the menace actor’s footprint.
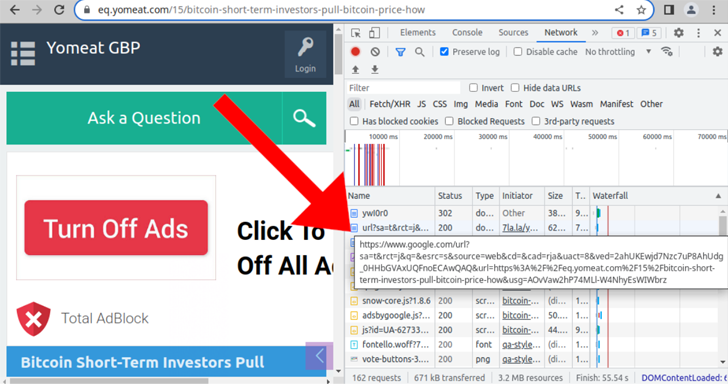
Also place to use are pseudo-quick URL domains that masquerade as well-known URL shortening instruments like Bitly, Cuttly, or ShortURL but in actuality immediate readers to sketchy Q&A web-sites.
Sucuri stated the redirects landed on Q&A web pages speaking about blockchain and cryptocurrency, with the URL domains now hosted on DDoS-Guard, a Russian internet infrastructure provider which has occur less than the scanner for providing bulletproof hosting solutions.
“Unwelcome redirects by using bogus shorter URL to phony Q&A sites result in inflated ad sights/clicks and thus inflated revenue for whomever is guiding this campaign,” Martin discussed. “It is just one really large and ongoing campaign of structured advertising income fraud.”
It is really not acknowledged exactly how the WordPress web-sites develop into contaminated in the to start with location. But when the web site is breached, the risk actor injects backdoor PHP code that makes it possible for for persistent distant obtain as properly as redirect site website visitors.
“Given that the further malware injection is lodged in just the wp-blog-header.php file it will execute every time the web page is loaded and reinfect the web-site,” Martin stated. “This guarantees that the surroundings continues to be infected right up until all traces of the malware are dealt with.”
Uncovered this report exciting? Stick to us on Twitter and LinkedIn to read extra special written content we submit.
Some pieces of this report are sourced from:
thehackernews.com

 LockBit releases entire negotiation history with Royal Mail, ransom set at £65 million
LockBit releases entire negotiation history with Royal Mail, ransom set at £65 million