The risk actor known as TA558 has been attributed to a new significant phishing marketing campaign that targets a extensive range of sectors in Latin The us with the goal of deploying Venom RAT.
The attacks primarily singled out hotel, journey, buying and selling, economic, manufacturing, industrial, and governing administration verticals in Spain, Mexico, United States, Colombia, Portugal, Brazil, Dominican Republic, and Argentina.
Energetic because at the very least 2018, TA558 has a historical past of concentrating on entities in the LATAM region to produce a wide range of malware this kind of as Loda RAT, Vjw0rm, and Revenge RAT.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The most up-to-date an infection chain, in accordance to Notion Level researcher Idan Tarab, leverages phishing e-mail as an original obtain vector to drop Venom RAT, a fork of Quasar RAT that comes with abilities to harvest delicate data and commandeer systems remotely.

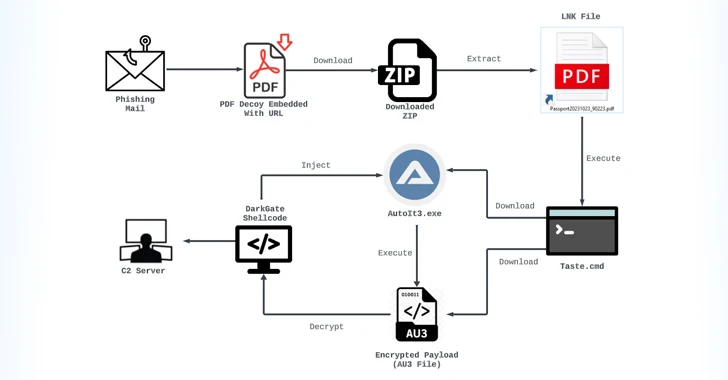
The disclosure arrives as danger actors have been increasingly noticed making use of the DarkGate malware loader next the legislation enforcement takedown of QakBot final yr to target economical institutions in Europe and the U.S.
“Ransomware teams employ DarkGate to produce an initial foothold and to deploy several styles of malware in company networks,” EclecticIQ researcher Arda Büyükkaya mentioned.
“These consist of, but are not confined to, details-stealers, ransomware, and distant management resources. The aim of these menace actors is to increase the amount of contaminated units and the quantity of details exfiltrated from a target.”

It also follows the emergence of malvertising campaigns designed to supply malware like FakeUpdates (aka SocGholish), Nitrogen, and Rhadamanthys.
Earlier this thirty day period, Israeli advert security corporation GeoEdge exposed that a notorious malvertising group tracked as ScamClub “has shifted its target towards video clip malvertising assaults, ensuing in a surge in Extensive-forced redirect volumes due to the fact February 11, 2024.”

The attacks entail the malicious use of Video clip Advert Serving Templates (Huge) tags – which are made use of for video clip advertising and marketing – to redirect unsuspecting people to fraudulent or scam pages but only upon prosperous passage of specified customer-aspect and server-facet fingerprinting tactics.
A greater part of the victims are situated in the U.S. (60.5%), adopted by Canada (7.2%), the U.K. (4.8%), Germany (2.1%), and Malaysia (1.7%), amid some others.
Discovered this post intriguing? Follow us on Twitter and LinkedIn to examine far more special content material we write-up.
Some areas of this report are sourced from:
thehackernews.com

 Indian Government Rescues 250 Citizens Forced into Cybercrime in Cambodia
Indian Government Rescues 250 Citizens Forced into Cybercrime in Cambodia