The identity of the 2nd threat actor at the rear of the Golden Chickens malware has been uncovered courtesy of a lethal operational security blunder, cybersecurity firm eSentire explained.
The person in issue, who lives in Bucharest, Romania, has been specified the codename Jack. He is one particular of the two criminals operating an account on the Russian-language Exploit.in forum below the identify “badbullzvenom,” the other remaining “Chuck from Montreal.”
eSentire characterised Jack as the real mastermind driving Golden Chickens. Proof unearthed by the Canadian corporation reveals that he is also outlined as the operator of a vegetable and fruit import and export small business.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Like ‘Chuck from Montreal,’ ‘Jack’ uses a number of aliases for the underground boards, social media, and Jabber accounts, and he also has gone to fantastic lengths to disguise himself,” eSentire researchers Joe Stewart and Keegan Keplinger stated.
“‘Jack’ has taken terrific pains to obfuscate the Golden Chickens malware, seeking to make it undetectable by most [antivirus] corporations, and strictly letting only a smaller selection of consumers to invest in entry to the Golden Chickens MaaS.”
Golden Chickens (aka Additional_eggs) is a malware suite made use of by financially-inspired cybercrime actors these as Cobalt Group and FIN6. The threat actors driving the malware, also regarded as Venom Spider, function underneath a malware-as-a-company (MaaS) design.
The JavaScript malware is distributed via phishing strategies and will come with quite a few parts to harvest economical information, execute lateral movement, and even drop a ransomware plugin for PureLocker called TerraCrypt.
Jack’s on-line activities, in accordance to eSentire, go all the way back again to 2008, when he was just 15 yrs outdated and signed up for several cybercrime boards as a novice member. All his aliases are being collectively tracked as Blessed.
The investigation, in placing collectively his electronic trail, traces Jack’s development from a teenager fascinated in building destructive courses to a longtime hacker associated in establishing password stealers, crypters, and Much more_eggs.
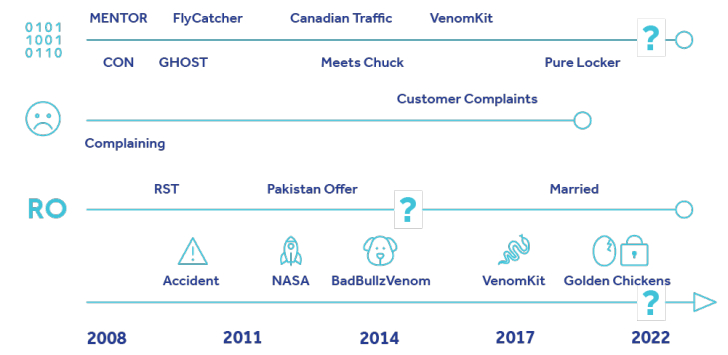
Some of the earliest malware instruments produced by Jack in 2008 consisted of Voyer, which is capable of harvesting a user’s Yahoo quick messages, and an data stealer christened FlyCatcher that can file keystrokes.
A yr later, Jack unveiled a new password stealer dubbed CON that’s built to siphon credentials from distinct web browsers, VPN, and FTP applications as perfectly as now-defunct messaging applications like MSN Messenger and Yahoo! Messenger.
Jack, later that similar 12 months, commenced promotion a crypter referred to as GHOST to help other actors encrypt and obfuscate malware with the objective of evading detection. The sudden demise of his father in a auto accident is thought to have prompted him to pause growth of the resource in 2010.
Quick forward to 2012, Jack began to acquire a status in the cybercriminal neighborhood as a scammer for failing to provide adequate support to prospects getting the item from him.
He also cited “big everyday living challenges” in a discussion board publish on April 27, 2012, stating he is considering moving to Pakistan to work for the government as a security expert and that a single amid his crypter customers “performs at pakistan guv” [read government].
Approaching WEBINARZero Have confidence in + Deception: Understand How to Outsmart Attackers!
Find out how Deception can detect innovative threats, end lateral movement, and improve your Zero Have faith in strategy. Be part of our insightful webinar!
Help you save My Seat!
It can be not promptly obvious if Jack ended up going to Pakistan, but eSentire said it noticed tactical overlaps involving a 2019 marketing campaign carried out by a Pakistani threat actor recognised as SideCopy and Jack’s VenomLNK malware, which functions as the initial entry vector for the Extra_eggs backdoor.
Jack is suspected to have crossed paths with “Chuck from Montreal” sometime concerning late 2012 and Oct 4, 2013, the date on which a information was posted from Chuck’s badbullz account on the Lampeduza discussion board made up of speak to data – a Jabber handle – affiliated with Blessed.
It’s speculated that Jack brokered a deal with Chuck that would let him to submit underneath Chuck’s aliases “badbullz” and “badbullzvenom” on a variety of underground message boards as a way to get around his notoriety as a ripper.
Lending credence to this hypothesis is the point that 1 of LUCKY’s new tools, a kit for creating macros referred to as MULTIPLIER, was produced in 2015 through the badbullzvenom account, while the menace actor behind the Blessed account ceased posting by means of that handle.
“By making use of the badbullzvenom and badbullz accounts, and unbeknownst to discussion board associates, he is basically setting up with a cleanse slate, and he can proceed to construct his credibility less than the account aliases: badbullz and badbullzvenom,” the researcher discussed.
Subsequently in 2017, badbullzvenom (aka Lucky) unveiled a separate instrument known as VenomKit, which has because evolved into the Golden Chickens MaaS. The malware’s means to evade detection also caught the attention of Cobalt Group, a Russia-primarily based cybercrime gang that leveraged it to deploy Cobalt Strike in attacks aimed at monetary entities.
Two many years afterwards, a different fiscally determined danger actor labeled FIN6 (aka ITG08 or Skeleton Spider) was noticed utilizing the Golden Chickens support to anchor its intrusions focusing on place-of-sale (POS) devices utilized by shops in Europe and the U.S.
The cybersecurity agency stated it also discovered the identities of his spouse, mom, and two sisters. He and his wife are claimed to reside in an upscale aspect of Bucharest, with his wife’s social media accounts documenting their excursions to metropolitan areas like London, Paris, and Milan. The photos additional clearly show them donning designer apparel and extras.
“The menace actor who went by the alias Fortunate and who also shares the badbullz and badbullzvenom accounts with the Montreal-based cybercriminal ‘Chuck,’ made his lethal slip-up when he employed the Jabber account,” the scientists explained.
Located this article attention-grabbing? Follow us on Twitter and LinkedIn to go through a lot more distinctive material we put up.
Some sections of this write-up are sourced from:
thehackernews.com


 Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks
Notorious Cyber Gang FIN7 Returns Cl0p Ransomware in New Wave of Attacks