The operators driving the Mekotio banking trojan have resurfaced with a shift in its infection move so as to keep under the radar and evade security software, although staging nearly 100 attacks around the final 3 months.
“Just one of the main qualities […] is the modular attack which offers the attackers the capacity to transform only a compact aspect of the full in get to avoid detection,” researchers from Check Place Investigate claimed in a report shared with The Hacker News. The most recent wave of attacks are said to largely focus on victims positioned in Brazil, Chile, Mexico, Peru, and Spain.
The growth will come right after Spanish legislation enforcement agencies in July 2021 arrested 16 people today belonging to a prison network in connection with working Mekotio and another banking malware termed Grandoreiro as element of a social engineering campaign focusing on economical institutions in Europe.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

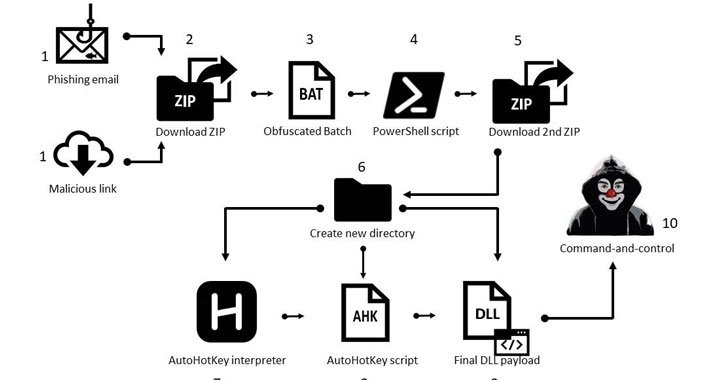
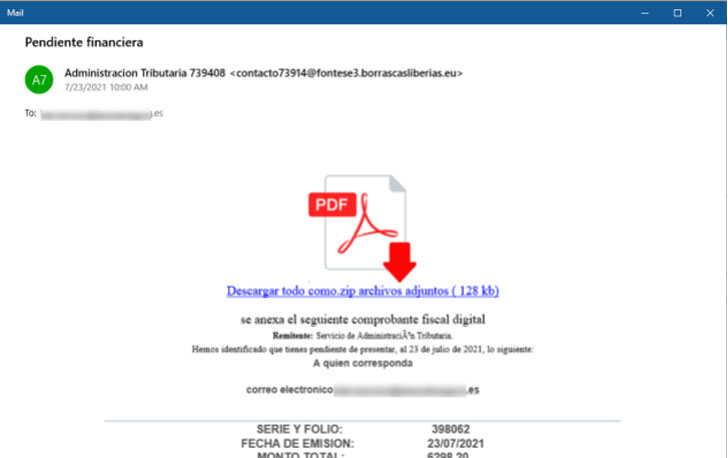
The advanced version of the Mekotio malware pressure is designed for compromising Windows systems with an attack chain that commences with phishing emails masquerading as pending tax receipts and made up of a backlink to a ZIP file or a ZIP file as an attachment. Clicking open the ZIP archive triggers the execution of a batch script that, in convert, runs a PowerShell script to obtain a 2nd-stage ZIP file.
This secondary ZIP file properties 3 distinct information — an AutoHotkey (AHK) interpreter, an AHK script, and the Mekotio DLL payload. The aforementioned PowerShell script then phone calls the AHK interpreter to execute the AHK script, which runs the DLL payload to steal passwords from on-line banking portals and exfiltrate the final results back again to a remote server.
The destructive modules are characterized by the use of basic obfuscation tactics, these types of as substitution ciphers, providing the malware improved stealth capabilities and enabling it to go undetected by most antivirus remedies.

“You can find a really authentic hazard in the Mekotio banker stealing usernames and passwords, in order to achieve entry into money institutions,” Check Point’s Kobi Eisenkraft explained. “That’s why, the arrests stopped the activity of the Spanish gangs, but not the most important cybercrime groups powering Mekotio.”
People in Latin America are remarkably advised to use two-factor authentication to protected their accounts from takeover attacks, and observe out for lookalike domains, spelling mistakes in email messages or web sites, and email messages from unfamiliar senders.
Found this report interesting? Observe THN on Facebook, Twitter and LinkedIn to read through much more exclusive articles we publish.
Some pieces of this posting are sourced from:
thehackernews.com

 Facebook is shutting down its controversial facial recognition system
Facebook is shutting down its controversial facial recognition system