Meta has provided details on how it intends to carry out interoperability in WhatsApp and Messenger with 3rd-party messaging providers as the Digital Marketplaces Act (DMA) went into outcome in the European Union.
“This permits end users of third-party vendors who select to allow interoperability (interop) to deliver and acquire messages with opted-in end users of possibly Messenger or WhatsApp – both designated by the European Fee (EC) as remaining needed to independently provide interoperability to third-party messaging expert services,” Meta’s Dick Brouwer said.
DMA, which officially became enforceable on March 7, 2024, calls for firms in gatekeeper positions – Apple, Alphabet, Meta, Amazon, Microsoft, and ByteDance – to clamp down on anti-competitive tactics from tech gamers, stage the taking part in discipline, as very well as compel them to open up some of their services to competition.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

As component of its initiatives to comply with the landmark restrictions, the social media giant claimed it expects 3rd-party providers to use the Sign Protocol, which is applied in the two WhatsApp and Messenger for close-to-conclusion encryption (E2EE).
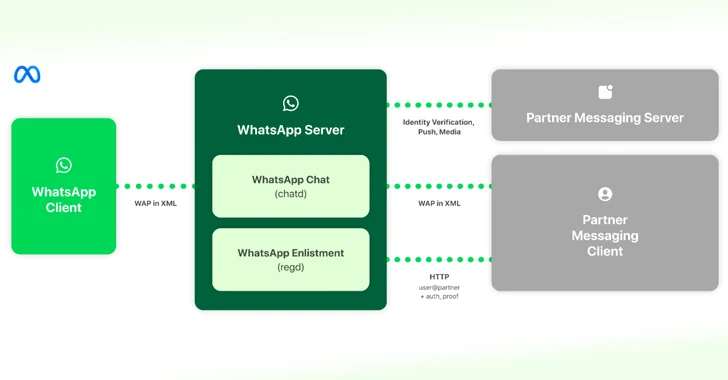
The third-events are also necessary to offer the encrypted communications into information stanzas in eXtensible Markup Language (XML). Should the concept incorporate media articles, an encrypted model is downloaded by Meta purchasers from the third-party messaging servers employing a Meta proxy assistance.
The enterprise is also proposing what is actually named a “plug-and-perform” model that lets 3rd-party companies to join to its infrastructure for achieving interoperability.
“Getting the instance of WhatsApp, 3rd-party customers will join to WhatsApp servers making use of our protocol (primarily based on the Extensible Messaging and Existence Protocol – XMPP),” Brouwer explained.
“The WhatsApp server will interface with a 3rd-party server more than HTTP in get to aid a selection of issues which includes authenticating 3rd-party users and press notifications.”
On top of that, third-party consumers are mandated to execute a WhatsApp Enlistment API when opting into its network, alongside supplying cryptographic proof of their ownership of the third-party person-obvious identifier when connecting or a third-party consumer registers on WhatsApp or Messenger.

The specialized architecture also has provisions for a 3rd-party company to increase a proxy or an intermediary between their customer and the WhatsApp server to deliver additional information and facts about the varieties of content material their shopper can receive from the WhatsApp server.
“The challenge right here is that WhatsApp would no longer have immediate link to both equally shoppers and, as a result, would lose connection level indicators that are vital for keeping consumers risk-free from spam and scams this sort of as TCP fingerprints,” Brouwer pointed out.
“This technique also exposes all the chat metadata to the proxy server, which boosts the probability that this info could be unintentionally or intentionally leaked.”
Observed this article intriguing? Observe us on Twitter and LinkedIn to read much more distinctive content material we write-up.
Some pieces of this report are sourced from:
thehackernews.com

 Secrets Sensei: Conquering Secrets Management Challenges
Secrets Sensei: Conquering Secrets Management Challenges