Cryptocurrency investment decision organizations are the concentrate on of a establishing menace cluster that works by using Telegram teams to look for out prospective victims.
Microsoft’s Security Danger Intelligence Middle (MSTIC) is tracking the action below the name DEV-0139, and builds upon a new report from Volexity that attributed the similar set of attacks to North Korea’s Lazarus Team.
“DEV-0139 joined Telegram groups used to aid interaction concerning VIP customers and cryptocurrency trade platforms and discovered their goal from amongst the users,” the tech giant reported.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The adversary subsequently impersonated one more cryptocurrency expenditure company and invited the victim to join a distinct Telegram chat group beneath the pretext of asking for comments on the trading cost construction employed by exchange platforms across VIP tiers.

It truly is really worth pointing out that the VIP method is built to reward high-volume traders with exclusive buying and selling rate incentives and bargains based on the 30-working day investing volume.
This attack chain notably dovetails with Volexity’s examination of an Oct 2022 campaign, whereby the menace actor pivoted from working with MSI installer documents to a weaponized Microsoft Excel document displaying the intended cryptocurrency coin charges.
Microsoft described the document as that contains possible precise data to raise the likelihood of achievements of the marketing campaign, suggesting that DEV-0139 is nicely versed in the interior workings of the crypto industry.
The malware-laced Excel file, for its part, is tasked with executing a malicious macro that is applied to stealthily fall and execute a second Excel worksheet, which, in change, contains a macro that downloads a PNG image file hosted on OpenDrive.
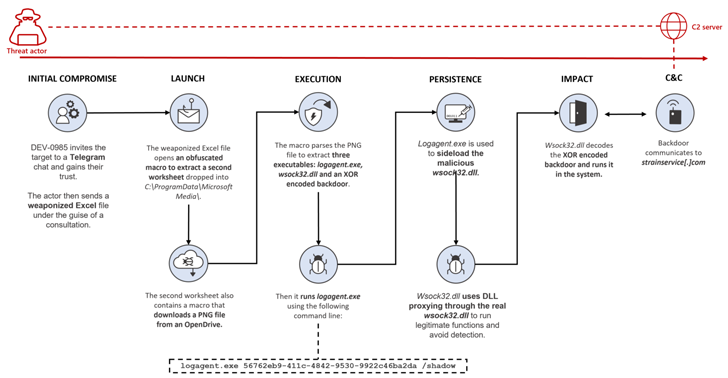
This impression file incorporates 3 executables, each individual of which is employed to launch the upcoming-stage payload, ultimately paving the way for a backdoor that lets the threat actor remotely entry the contaminated method.
Also, the fee structure spreadsheet is password-shielded in a bid to encourage the goal into enabling macros, therefore initiating destructive steps. A metadata examination of the file displays that it was developed on Oct 14, 2022 by a person named Wolf.
DEV-0139 has also been joined to an substitute attack sequence in which an MSI package deal for a phony application named “CryptoDashboardV2” is sent in spot of a destructive Excel doc to deploy the similar implant.
The backdoor predominantly allows distant accessibility to the host by accumulating data from the targeted program and connecting to a command-and-control (C2) server to get added instructions.
“The cryptocurrency marketplace continues to be a field of desire for risk actors,” Microsoft stated. “Targeted consumers are discovered via trustworthy channels to enhance the probability of results.”
In current yrs, Telegram has not only witnessed prevalent adoption in the cryptocurrency marketplace, but also been co-opted by risk actors looking to discuss zero-working day vulnerabilities, provide stolen information, and current market their expert services via the well-liked messaging system.
“With buyers shedding confidence in the anonymity supplied by discussion boards, illicit marketplaces are more and more turning to Telegram,” Optimistic Systems disclosed in a new analyze of 323 general public Telegram channels and groups with around one million subscribers in whole.
“The selection of special cyberattacks is constantly developing, and the market for cybercriminal solutions is growing and relocating into everyday social media and messaging applications, thereby substantially reducing the entry threshold for cybercriminals.”
Identified this report appealing? Follow us on Twitter and LinkedIn to go through a lot more special content we article.
Some areas of this posting are sourced from:
thehackernews.com

 New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network
New Go-based Zerobot Botnet Exploiting Dozen of IoT Vulnerabilities to Expand its Network