Microsoft on Thursday disclosed that it dealt with a pair of issues with the Azure Database for PostgreSQL Flexible Server that could outcome in unauthorized cross-account database obtain in a location.
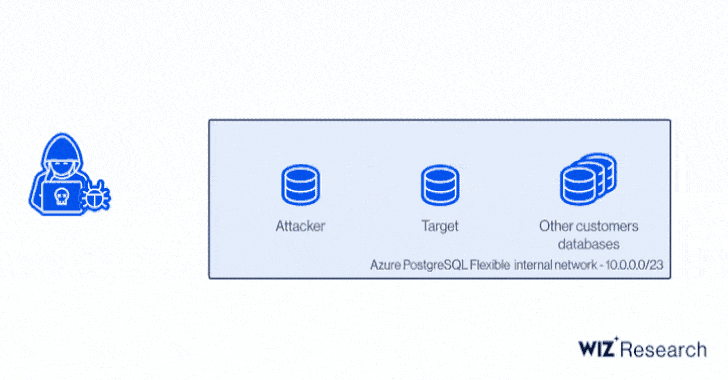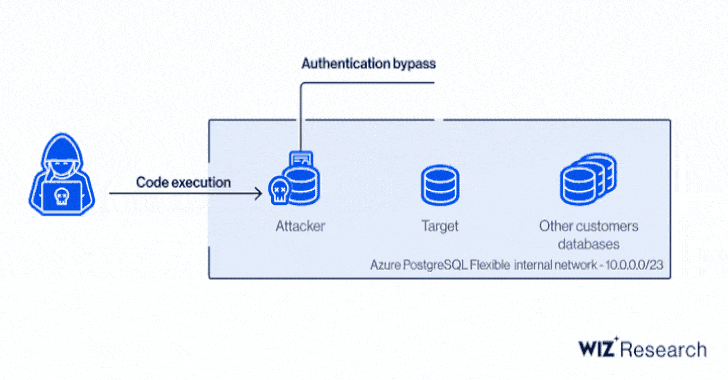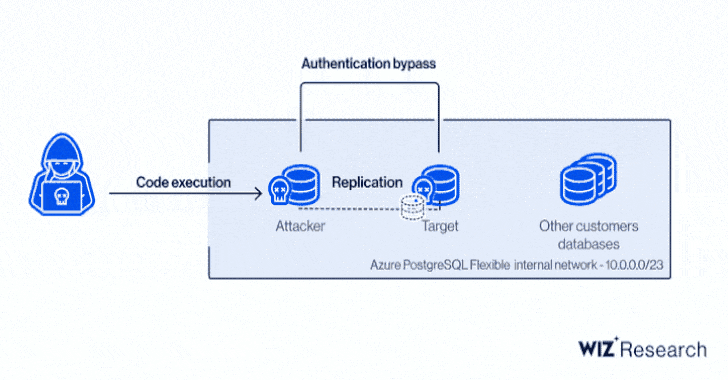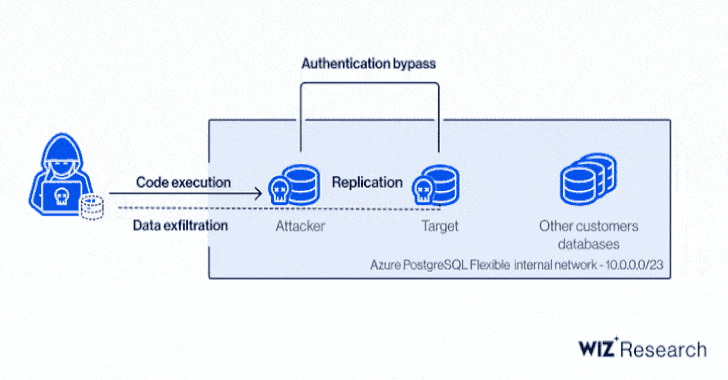
“By exploiting an elevated permissions bug in the Versatile Server authentication system for a replication person, a destructive consumer could leverage an improperly anchored standard expression to bypass authentication to gain entry to other customers’ databases,” Microsoft Security Reaction Centre (MSRC) reported.


Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
New York Town-centered cloud security business Wiz, which uncovered the flaws, dubbed the exploit chain “ExtraReplica.” Microsoft explained it mitigated the bug inside of 48 hrs of disclosure on January 13, 2022.
Precisely, it relates to a circumstance of privilege escalation in the Azure PostgreSQL engine to gain code execution and a cross-account authentication bypass by usually means of a cast certification, enabling an attacker to make a database in the target’s Azure location and exfiltrate delicate information.
In other text, thriving exploitation of the critical flaws could have enabled an adversary to acquire unauthorized study entry to other customers’ PostgreSQL databases, proficiently circumventing tenant isolation.
Wiz zeroed down the privilege escalation to a bug stemming as a consequence of modifications introduced in the PostgreSQL engine to harden their privilege design and increase new attributes. The identify ExtraReplica comes from the simple fact that the exploit leverages a PostgreSQL aspect that permits copying database details from just one server to a different, i.e., “replicating” the databases.

The Windows maker explained the security vulnerability as influencing PostgreSQL Versatile Server cases deployed applying the general public access networking selection, but pressured that it did not locate evidence of the flaw remaining actively exploited and that no client knowledge was accessed.
“No motion is expected by consumers,” MSRC stated. “In purchase to more decrease publicity, we endorse that customers allow personal network entry when environment up their Flexible Server occasions.”
Identified this post interesting? Follow THN on Fb, Twitter and LinkedIn to browse extra exclusive content material we write-up.
Some components of this posting are sourced from:
thehackernews.com

 Indian Govt Orders Organizations to Report Security Breaches Within 6 Hours to CERT-In
Indian Govt Orders Organizations to Report Security Breaches Within 6 Hours to CERT-In