Microsoft on Thursday explained it can be after once more disabling the ms-appinstaller protocol handler by default adhering to its abuse by various risk actors to distribute malware.
“The observed risk actor action abuses the current implementation of the ms-appinstaller protocol handler as an entry vector for malware that may well direct to ransomware distribution,” the Microsoft Threat Intelligence workforce claimed.
It further more observed that a number of cybercriminals are featuring a malware package for sale as a services that leverages the MSIX file format and ms-appinstaller protocol handler. The improvements have gone into impact in Application Installer edition 1.21.3421. or higher.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The attacks choose the type of signed destructive MSIX application deals that are dispersed by way of Microsoft Teams or malicious ads for respectable well-known software on lookup engines like Google.
Upcoming WEBINAR From Person to ADMIN: Study How Hackers Get Whole Control
Explore the mystery methods hackers use to become admins, how to detect and block it before it really is much too late. Sign-up for our webinar right now.
Be part of Now
At minimum 4 distinctive fiscally enthusiastic hacking teams have been observed having gain of the Application Installer services due to the fact mid-November 2023, using it as an entry issue for stick to-on human-operated ransomware exercise –
- Storm-0569, an first entry broker which propagates BATLOADER by research engine optimization (Search engine marketing) poisoning with websites spoofing Zoom, Tableau, TeamViewer, and AnyDesk, and takes advantage of the malware to supply Cobalt Strike and handoff the accessibility to Storm-0506 for Black Basta ransomware deployment.
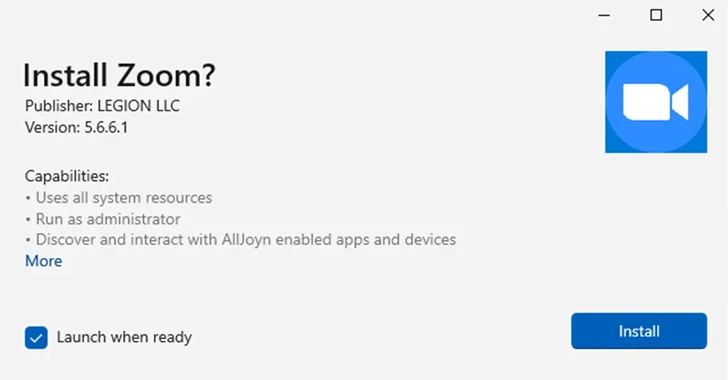
- Storm-1113, an first entry broker that takes advantage of bogus MSIX installers masquerading as Zoom to distribute EugenLoader (aka FakeBat), which functions as a conduit for a variety of stealer malware and remote accessibility trojans.
- Sangria Tempest (aka Carbon Spider and FIN7), which utilizes Storm-1113’s EugenLoader to drop Carbanak that, in convert, delivers an implant known as Gracewire. Alternatively, the group has relied on Google ads to lure people into downloading malicious MSIX application deals from rogue landing webpages to distribute POWERTRASH, which is then applied to load NetSupport RAT and Gracewire.
- Storm-1674, an initial entry broker that sends fake landing webpages masquerading as Microsoft OneDrive and SharePoint via Groups messages working with the TeamsPhisher instrument, urging recipients to open up PDF data files that, when clicked, prompts them to update their Adobe Acrobat Reader to download a destructive MSIX installer that incorporates SectopRAT or DarkGate payloads.
Microsoft explained Storm-1113 as an entity that also dabbles in “as-a-support,” giving destructive installers and landing webpage frameworks mimicking effectively-regarded software program to other menace actors these types of as Sangria Tempest and Storm-1674.

In October 2023, Elastic Security Labs specific an additional campaign in which spurious MSIX Windows app offer documents for Google Chrome, Microsoft Edge, Brave, Grammarly, and Cisco Webex were employed to distribute a malware loader dubbed GHOSTPULSE.
This is not the initially time Microsoft has disabled the MSIX ms-appinstaller protocol handler in Windows. In February 2022, the tech huge took the same phase to prevent threat actors from weaponizing it to produce Emotet, TrickBot, and Bazaloader.
“Menace actors have probably selected the ms-appinstaller protocol handler vector because it can bypass mechanisms designed to support hold end users secure from malware, this kind of as Microsoft Defender SmartScreen and constructed-in browser warnings for downloads of executable file formats,” Microsoft claimed.
Identified this short article intriguing? Follow us on Twitter and LinkedIn to go through additional unique material we post.
Some sections of this post are sourced from:
thehackernews.com

 Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service
Google Cloud Resolves Privilege Escalation Flaw Impacting Kubernetes Service