Microsoft reported it teamed up with Fortra and Wellbeing Facts Sharing and Investigation Middle (Health-ISAC) to deal with the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware.
To that conclude, the tech giant’s Electronic Crimes Unit (DCU) exposed that it secured a courtroom order in the U.S. to “take away illegal, legacy copies of Cobalt Strike so they can no lengthier be employed by cybercriminals.”
While Cobalt Strike, developed and maintained by Fortra (formerly HelpSystems), is a authentic post-exploitation software made use of for adversary simulation, illegal cracked variations of the software package have been weaponized by danger actors about the several years.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Ransomware actors, in unique, have leveraged Cobalt Strike soon after obtaining initial entry to a focus on environment to escalate privileges, lateral go across the network, and deploy file-encrypting malware.
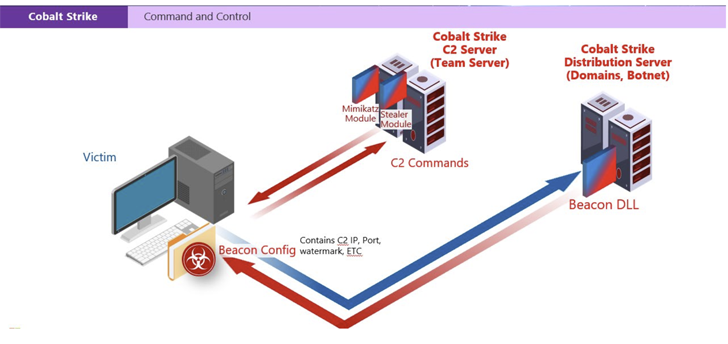
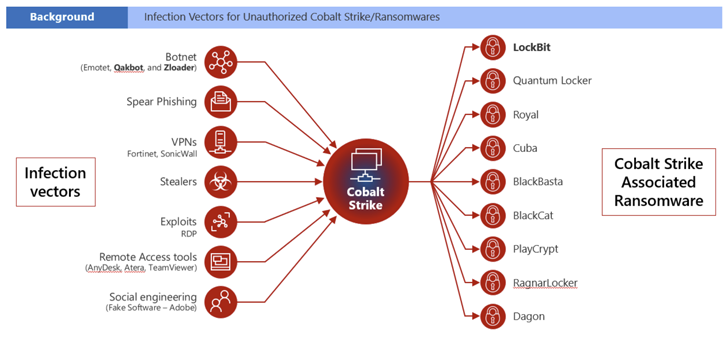
“The ransomware families involved with or deployed by cracked copies of Cobalt Strike have been joined to much more than 68 ransomware attacks impacting healthcare corporations in a lot more than 19 nations all over the planet,” Amy Hogan-Burney, standard manager of DCU, said.
By disrupting the use of legacy copies of Cobalt Strike and compromised Microsoft application, the aim is to hinder the attacks and pressure the adversaries to rethink their ways, the corporation added.
Impending WEBINARLearn to Protected the Identity Perimeter – Verified Techniques
Improve your business enterprise security with our forthcoming professional-led cybersecurity webinar: Check out Identification Perimeter approaches!
You should not Pass up Out – Save Your Seat!
Redmond additional famous the misuse of Cobalt Strike by country-point out groups whose functions align with that of Russia, China, Vietnam, and Iran, introducing it detected malicious infrastructure hosting Cobalt Strike throughout the world, counting China, the U.S., and Russia.
The legal crackdown will come months following Google Cloud recognized 34 unique hacked release versions of the Cobalt Strike device in the wild in an try to “make it more difficult for lousy fellas to abuse.”
Identified this posting appealing? Comply with us on Twitter and LinkedIn to read far more exceptional content we write-up.
Some parts of this posting are sourced from:
thehackernews.com

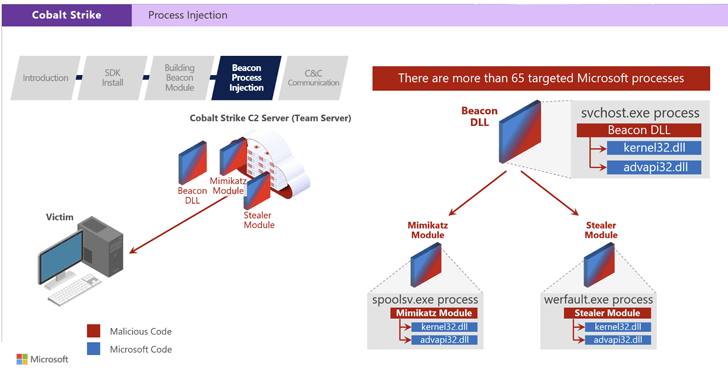
 Are Source Code Leaks the New Threat Software vendors Should Care About?
Are Source Code Leaks the New Threat Software vendors Should Care About?