Microsoft has announced plans to immediately block embedded documents with “dangerous extensions” in OneNote subsequent studies that the observe-using service is being ever more abused for malware shipping.
Up until eventually now, people ended up proven a dialog warning them that opening these kinds of attachments could hurt their personal computer and details, but it was probable to dismiss the prompt and open the data files.
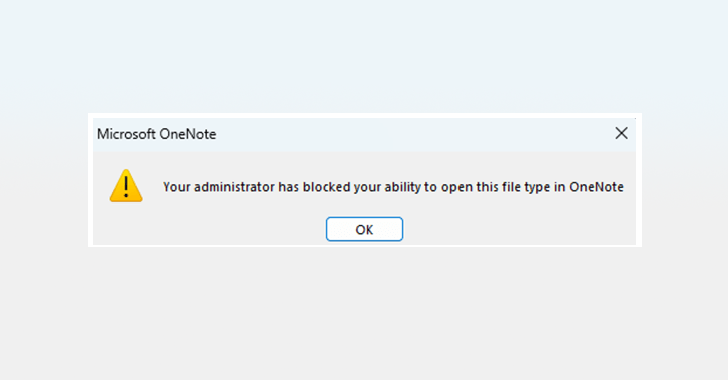
That is likely to alter heading ahead. Microsoft explained it intends to stop consumers from instantly opening an embedded file with a harmful extension and display screen the concept: “Your administrator has blocked your capacity to open up this file kind in OneNote.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The update is expected to start out rolling out with Version 2304 later this thirty day period and only impacts OneNote for Microsoft 365 on gadgets managing Windows. It does not impact other platforms, which include macOS, Android, and iOS, as well as OneNote variations available on the web and for Windows 10.
“By default, OneNote blocks the same extensions that Outlook, Phrase, Excel, and PowerPoint do,” Microsoft reported. “Destructive scripts and executables can result in hurt if clicked by the user. If extensions are extra to this allow for list, they can make OneNote and other apps, such as Word and Excel, considerably less secure.”
The listing of 120 extensions are as follows –
.ade, .adp, .app, .application, .appref-ms, .asp, .aspx, .asx, .bas, .bat, .bgi, .cab, .cer, .chm, .cmd, .cnt, .com, .cpl, .crt, .csh, .der, .diagcab, .exe, .fxp, .gadget, .grp, .hlp, .hpj, .hta, .htc, .inf, .ins, .iso, .isp, .its, .jar, .jnlp, .js, .jse, .ksh, .lnk, .mad, .maf, .mag, .mam, .maq, .mar, .mas, .mat, .mau, .mav, .maw, .mcf, .mda, .mdb, .mde, .mdt, .mdw, .mdz, .msc, .msh, .msh1, .msh2, .mshxml, .msh1xml, .msh2xml, .msi, .msp, .mst, .msu, .ops, .osd, .pcd, .pif, .pl, .plg, .prf, .prg, .printerexport, .ps1, .ps1xml, .ps2, .ps2xml, .psc1, .psc2, .psd1, .psdm1, .pst, .py, .pyc, .pyo, .pyw, .pyz, .pyzw, .reg, .scf, .scr, .sct, .shb, .shs, .theme, .tmp, .url, .vb, .vbe, .vbp, .vbs, .vhd, .vhdx, .vsmacros, .vsw, .webpnp, .site, .ws, .wsc, .wsf, .wsh, .xbap, .xll, and .xnk
THN WEBINARBecome an Incident Response Pro!
Unlock the secrets and techniques to bulletproof incident response – Grasp the 6-Section method with Asaf Perlman, Cynet’s IR Leader!
Never Pass up Out – Save Your Seat!
Consumers who decide to still open up the embedded file can do so by 1st preserving the file regionally to their device and then opening it from there.
The growth comes as Microsoft’s determination to block macros by default in Workplace documents downloaded from the internet spurred menace actors to swap to OneNote attachments to provide malware by means of phishing attacks.
According to cybersecurity firm Trellix, the number of destructive OneNote samples has been progressively growing considering that December 2022, in advance of ramping up in February 2023.
Identified this posting fascinating? Comply with us on Twitter and LinkedIn to read through a lot more exclusive content we article.
Some pieces of this posting are sourced from:
thehackernews.com

 Cryptocurrency Companies Targeted in Sophisticated 3CX Supply Chain Attack
Cryptocurrency Companies Targeted in Sophisticated 3CX Supply Chain Attack