Banking and financial expert services corporations are the targets of a new multi-stage adversary-in-the-center (AitM) phishing and small business email compromise (BEC) attack, Microsoft has revealed.
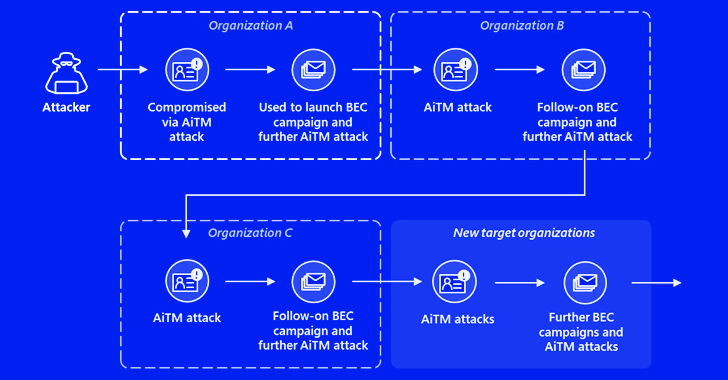
“The attack originated from a compromised trusted vendor and transitioned into a collection of AiTM attacks and comply with-on BEC activity spanning multiple corporations,” the tech large disclosed in a Thursday report.
Microsoft, which is tracking the cluster underneath its emerging moniker Storm-1167, named out the group’s use of oblique proxy to pull off the attack.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This enabled the attackers to flexibly tailor the phishing internet pages to their targets and carry out session cookie theft, underscoring the continued sophistication of AitM attacks.
The modus operandi is not like other AitM campaigns wherever the decoy webpages act as a reverse proxy to harvest credentials and time-primarily based one-time passwords (TOTPs) entered by the victims.

“The attacker offered targets with a site that mimicked the sign-in site of the targeted application, as in regular phishing attacks, hosted on a cloud assistance,” Microsoft mentioned.
“The stated indicator-in page contained sources loaded from an attacker-controlled server, which initiated an authentication session with the authentication provider of the concentrate on application using the victim’s credentials.”
The attack chains commence with a phishing email that points to a url, which, when clicked, redirects a sufferer into checking out a spoofed Microsoft signal-in website page and entering their qualifications and TOTPs.
The harvested passwords and session cookies are then employed to impersonate the user and attain unauthorized access to the email inbox by means of a replay attack. The access is then abused to get maintain of delicate emails and orchestrate a BEC attack.
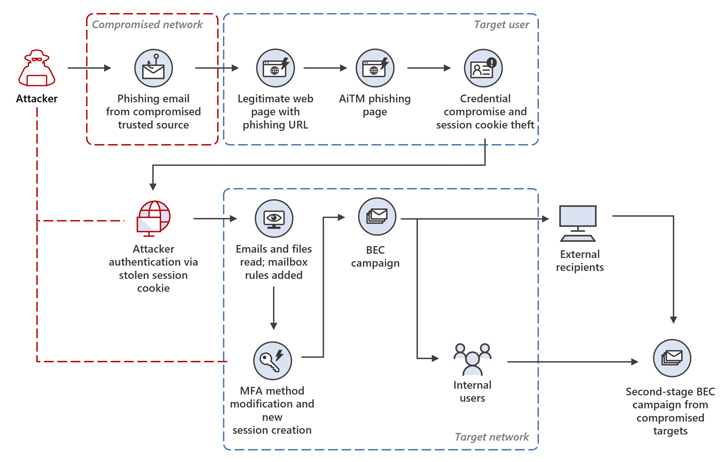
What’s extra, a new SMS-based two-factor authentication method is added to the goal account in buy to indication in applying the pilfered credentials sans attracting any focus.
In the incident analyzed by Microsoft, the attacker is claimed to have initiated a mass spam campaign, sending more than 16,000 emails to the compromised user’s contacts, each inside and exterior of the corporation, as properly as distribution lists.
The adversary has also been noticed getting measures to minimize detection and set up persistence by responding to incoming email messages and subsequently having steps to delete them from the mailbox.
Ultimately, the recipients of the phishing email messages are focused by a second AitM attack to steal their credentials and cause yet yet another phishing marketing campaign from the email inbox of one particular of the customers whose account was hacked as a final result of the AitM attack.
Forthcoming WEBINAR🔐 Mastering API Security: Comprehending Your Legitimate Attack Area
Find out the untapped vulnerabilities in your API ecosystem and consider proactive steps towards ironclad security. Be a part of our insightful webinar!
Be a part of the Session.wn-button,.wn-label,.wn-label:just afterdisplay:inline-block.look at_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-top rated-remaining-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-ideal-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-measurement:13pxmargin:20px 0font-bodyweight:600letter-spacing:.6pxcolor:#596cec.wn-label:afterwidth:50pxheight:6pxcontent:”border-leading:2px stable #d9deffmargin: 8px.wn-titlefont-size:21pxpadding:10px 0font-bodyweight:900textual content-align:leftline-peak:33px.wn-descriptiontextual content-align:leftfont-sizing:15.6pxline-peak:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-coloration:#4469f5font-sizing:15pxcolor:#fff!importantborder:0line-top:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
“This attack reveals the complexity of AiTM and BEC threats, which abuse reliable interactions concerning sellers, suppliers, and other spouse corporations with the intent of economical fraud,” the enterprise added.
The improvement arrives considerably less than a month right after Microsoft warned of a surge in BEC attacks and the evolving techniques used by cybercriminals, such as the use of platforms, like BulletProftLink, for producing industrial-scale destructive mail strategies.
A different tactic involves the use of household internet protocol (IP) addresses to make attack campaigns seem domestically created, the tech big mentioned.
“BEC danger actors then invest in IP addresses from household IP products and services matching the victim’s site creating household IP proxies which empower cybercriminals to mask their origin,” Redmond stated.
“Now, armed with localized handle house to assistance their destructive things to do in addition to usernames and passwords, BEC attackers can obscure movements, circumvent ‘impossible travel’ flags, and open up a gateway to perform further more attacks.”
Discovered this post intriguing? Comply with us on Twitter and LinkedIn to study much more exceptional content material we post.
Some pieces of this posting are sourced from:
thehackernews.com

 University of Manchester Suffers Suspected Data Breach During Cyber Incident
University of Manchester Suffers Suspected Data Breach During Cyber Incident