Getty Images
Microsoft has revealed facts of a “large-scale” phishing attack that demonstrates a new way of circumventing multi-factor authentication (MFA) security actions.
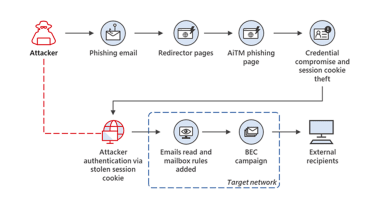
The attack employs an adversary-in-the-middle (AiTM) strategy to hijack a authentic user’s session and steal a cookie that can be utilised to entry a internet site while skipping MFA authentication if it was enabled.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Microsoft stated the campaign has specific much more than 10,000 organisations given that September 2021 with attackers working with the obtain to alter victims’ e-mail and carry out organization email compromise (BEC) attacks in opposition to other targets.
In addition, Microsoft reported attackers have been noticed carrying out economical fraud attempts inside 5 minutes of getting the authenticated session cookie.
They did this by looking for finance-connected e-mail in a victim’s Outlook on the internet account and making use of a range of procedures these kinds of as distributing solid invoices in an try to have their particular accounts paid out, posing as a genuine personnel of a business enterprise.
AiTM attack breakdown
The campaign’s operators initial attain out to victims by way of email, as is normal with phishing attacks, and ship a seemingly legitimate HTML hyperlink to check out as an attachment.
The goal below is to persuade a victim to log into a authentic site, these kinds of as a single necessitating their Microsoft credentials applied for their perform account, and steal the session cookie that is developed when a consumer effectively authenticates them selves.
This is made use of so people really do not have to log into solutions every time they take a look at a new site due to the fact they have now authenticated them selves earlier in the session.
Attaining this cookie permits attackers to visit internet websites and authenticate themselves as if they were the sufferer, and this approach also functions if MFA controls are in place mainly because the user will have previously cleared the authentication required in advance of the cookie was stolen.
To steal the cookie in this article, the attacker deploys a web server that proxies the site visitors to and from the target and the authentic web-site. That usually means nearly anything the person inputs to the website is sent to the phishing web server before it reaches the genuine website, and all the things the real web site returns to the consumer is initially witnessed by the proxy server in the middle of the trade.
Microsoft
Microsoft reported this eliminates the require for an attacker to generate a fake web site that seems to be the authentic a single in buy to steal log-in qualifications, for instance. Only the URL displayed to the sufferer is different.
The attack can also be automatic working with open-supply phishing toolkits, Microsoft said. Popular toolkits made use of include Evilginx2, Modlishka, and Muraena, and the operators of this campaign use Evilginx2 as their infrastructure.
Article-attack things to do
Like quite a few cyber criminals, the operators of this campaign seem to be to be fiscally inspired. Microsoft noticed conditions exactly where it took a subject of minutes for payment fraud makes an attempt to be created.
In the times next the theft of an authenticated session cookie, attackers ended up noticed scanning Outlook on the net inboxes just about every couple of several hours for email chains to exploit for payment fraud. They also established inbox principles to cover replies from the fraud goal from the victim.
Attackers also deployed methods to hide their obtain, this sort of as deleting the unique phishing email from the victim’s inbox. This was a handbook procedure and differed from the first attack which was automatic.
Defending towards AiTM attacks
Microsoft was fast to position out that the attack method does not detect a flaw in MFA technology alone, and that all firms need to deploy MFA options to boost organisation-large security.
A single approach to reduce these forms of attacks would be to set conditional obtain procedures which could see trusted IP addresses or compliant devices extra to authentication customers, filtering out rogue connections attempting to use stolen session cookies.
The other proposed items of information have been to spend in anti-phishing goods that constantly keep an eye on for these attacks and for security groups to keep an eye on logs for suspicious activities.
Some parts of this article are sourced from:
www.itpro.co.uk


 Retbleed hardware-level flaw brings overhead woe to Intel and AMD
Retbleed hardware-level flaw brings overhead woe to Intel and AMD