Microsoft on Monday explained it detected Kremlin-backed country-point out activity exploiting a critical security flaw in its Outlook email company to gain unauthorized entry to victims’ accounts in just Exchange servers.
The tech large attributed the intrusions to a danger actor it known as Forest Blizzard (formerly Strontium), which is also broadly tracked less than the monikers APT28, BlueDelta, Extravagant Bear, FROZENLAKE, Iron Twilight, Sednit, and Sofacy.
The security vulnerability in query is CVE-2023-23397 (CVSS rating: 9.8), a critical privilege escalation bug that could make it possible for an adversary to entry a user’s Net-NTLMv2 hash that could then be applied to perform a relay attack from a further provider to authenticate as the consumer. It was patched by Microsoft in March 2023.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The aim, in accordance to the Polish Cyber Command (DKWOC), was to acquire unauthorized access to mailboxes belonging to community and non-public entities in the nation.
Approaching WEBINAR Master Insider Threat Detection with Application Reaction Procedures
Explore how software detection, response, and automatic behavior modeling can revolutionize your defense against insider threats.
Join Now
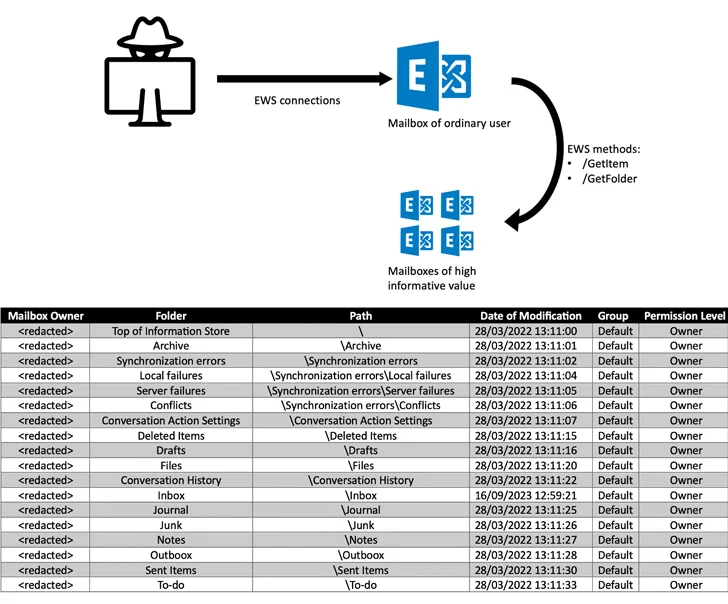
“In the subsequent phase of destructive activity, the adversary modifies folder permissions inside the victim’s mailbox,” DKWOC said. “In most conditions, the modifications are to change the default permissions of the ‘Default’ team (all authenticated consumers in the Exchange group) from ‘None’ to ‘Owner.'”
In accomplishing so, the contents of mailbox folders that have been granted this authorization can be browse by any authenticated person inside the business, enabling the risk actor to extract valuable facts from large-value targets.
“It really should be emphasised that the introduction of this kind of modifications permits for the routine maintenance of unauthorized obtain to the contents of the mailbox even right after losing immediate access to it,” DKWOC additional.
Microsoft earlier disclosed that the security shortcoming experienced been weaponized by Russia-based danger actors as a zero-working day in attacks focusing on government, transportation, vitality, and armed service sectors in Europe since April 2022.
Subsequently, in June 2023, cybersecurity agency Recorded Upcoming uncovered particulars of a spear-phishing campaign orchestrated by APT28 exploiting multiple vulnerabilities in the open up-supply Roundcube webmail software, even though at the same time noting that the campaign overlaps with action employing the Microsoft Outlook vulnerability.
The National Cybersecurity Company of France (ANSSI), in late October, also blamed the hacking outfit for targeting govt entities, organizations, universities, analysis institutes, and imagine tanks given that the next 50 percent of 2021 by taking edge of different flaws, counting CVE-2023-23397, to deploy implants this sort of as CredoMap.
The condition-sponsored group is assessed to be linked to Unit 26165 of the Primary Directorate of the Normal Staff of the Armed Forces of the Russian Federation (GRU), the overseas intelligence arm of the Ministry of Protection.

In modern months, it has also been related to attacks on several corporations in France and Ukraine as nicely as the abuse of the WinRAR flaw (CVE-2023-38831) to steal browser login details applying a PowerShell script named IRONJAW.
“Forest Blizzard regularly refines its footprint by employing new personalized procedures and malware, suggesting that it is a well-resourced and effectively-skilled team posing long-time period troubles to attribution and monitoring its functions,” Microsoft reported.
The attractiveness of Microsoft Outlook in organization environments makes it a rewarding attack vector, generating it “a person of the critical ‘gateways’ responsible for introducing different cyber threats into organizations,” according to Verify Stage, which laid out the various indicates by which the company could be abused by bad actors to produce their exploits.
The progress will come as The Guardian reported that the Sellafield nuclear squander web page in the U.K. experienced been breached by hacking crews connected with Russia and China to deploy “sleeper malware” as considerably back as 2015. Nonetheless, the U.K. federal government reported it located no proof to recommend that its networks experienced been “productively attacked by condition actors.”
Found this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to study much more special written content we article.
Some areas of this article are sourced from:
thehackernews.com


 New BLUFFS Bluetooth Attack Expose Devices to Adversary-in-the-Middle Attacks
New BLUFFS Bluetooth Attack Expose Devices to Adversary-in-the-Middle Attacks