Iranian nation-state teams have now joined economically enthusiastic actors in actively exploiting a critical flaw in PaperCut print management program, Microsoft claimed.
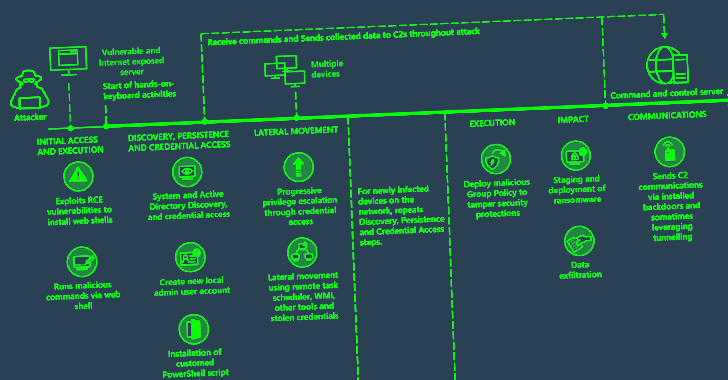
The tech giant’s risk intelligence staff claimed it noticed both Mango Sandstorm (Mercury) and Mint Sandstorm (Phosphorus) weaponizing CVE-2023-27350 in their functions to accomplish first obtain.
“This action exhibits Mint Sandstorm’s continued skill to promptly integrate [proof-of-concept] exploits into their operations,” Microsoft reported in a sequence of tweets.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
On the other hand, CVE-2023-27350 exploitation exercise related with Mango Sandstorm is said to be on the reduce conclude of the spectrum, with the state-sponsored team “making use of tools from prior intrusions to join to their C2 infrastructure.”

It really is worth noting that Mango Sandstorm is connected to Iran’s Ministry of Intelligence and Security (MOIS) and Mint Sandstorm is said to be related with the Islamic Revolutionary Guard Corps (IRGC).
The ongoing assault comes months immediately after Microsoft confirmed the involvement of Lace Tempest, a cybercrime gang that overlaps with other hacking groups like FIN11, TA505, and Evil Corp, in abusing the flaw to supply Cl0p and LockBit ransomware.
CVE-2023-27350 (CVSS rating: 9.8) relates to a critical flaw in PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with Process privileges.
A patch was designed out there by PaperCut on March 8, 2023. Pattern Micro’s Zero Working day Initiative (ZDI), which learned and documented the issue, is anticipated to release a lot more complex information about it on Could 10, 2023.
Cybersecurity organization VulnCheck, past 7 days, printed facts on a new line of attack that can circumvent existing detections, enabling adversaries to leverage the flaw unimpeded.
Upcoming WEBINARLearn to Prevent Ransomware with Actual-Time Defense
Sign up for our webinar and find out how to prevent ransomware attacks in their tracks with authentic-time MFA and support account protection.
Conserve My Seat!
With additional attackers leaping in on the PaperCut exploitation bandwagon to breach vulnerable servers, it really is critical that businesses shift speedily to utilize the required updates (variations 20.1.7, 21.2.11, and 22..9 and afterwards).
The enhancement also follows a report from Microsoft which unveiled that Iranian threat actors in Iran are increasingly relying on a new tactic that combines offensive cyber operations with multi-pronged impact functions to “gasoline geopolitical modify in alignment with the regime’s goals.”
The change coincides with an greater tempo in adopting newly documented vulnerabilities, the use of compromised sites for command-and-management to far better conceal the supply of attacks, and harnessing custom made tooling and tradecraft for highest impression.
Found this short article intriguing? Follow us on Twitter and LinkedIn to read through a lot more distinctive content we publish.
Some elements of this write-up are sourced from:
thehackernews.com

 Operation Power Off: 13 More Booter Sites Seized
Operation Power Off: 13 More Booter Sites Seized