Microsoft on Friday shared steering to assist clients find out indicators of compromise (IoCs) connected with a lately patched Outlook vulnerability.
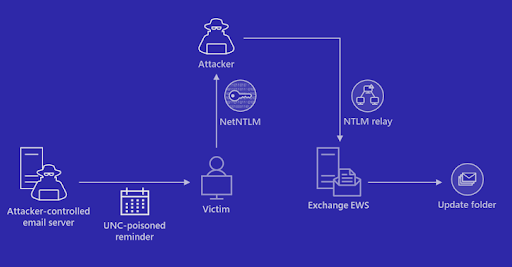
Tracked as CVE-2023-23397 (CVSS score: 9.8), the critical flaw relates to a situation of privilege escalation that could be exploited to steal NT Lan Manager (NTLM) hashes and phase a relay attack without requiring any person interaction.
“External attackers could send specifically crafted e-mail that will lead to a connection from the sufferer to an untrusted location of attackers’ control,” the corporation mentioned in an advisory released this thirty day period.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“This will leak the Net-NTLMv2 hash of the sufferer to the untrusted network which an attacker can then relay to one more support and authenticate as the sufferer.
The vulnerability was settled by Microsoft as component of its Patch Tuesday updates for March 2023, but not right before Russia-based mostly danger actors weaponized the flaw in attacks concentrating on federal government, transportation, energy, and armed service sectors in Europe.
Microsoft’s incident response said it found evidence of probable exploitation of the shortcoming as early as April 2022.
In just one attack chain described by the tech huge, a profitable Net-NTLMv2 Relay attack enabled the risk actor to acquire unauthorized accessibility to an Trade Server and modify mailbox folder permissions for persistent access.
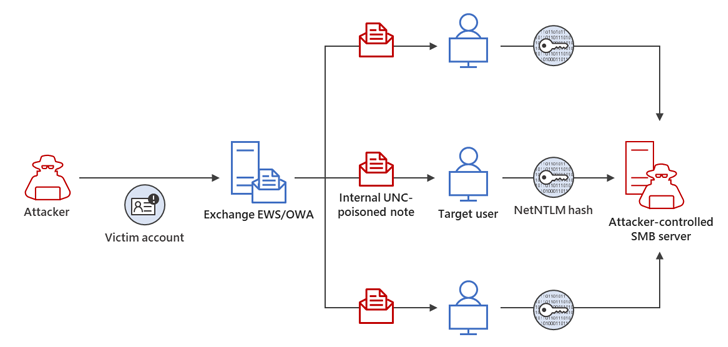
The compromised email account was then applied to lengthen the adversary’s accessibility in the compromised atmosphere by sending more malicious messages to focus on other members of the similar group.
“Though leveraging NTLMv2 hashes to obtain unauthorized entry to methods is not a new method, the exploitation of CVE-2023-23397 is novel and stealthy,” Microsoft said.
“Companies need to review SMBClient function logging, Course of action Development gatherings, and other obtainable network telemetry to discover prospective exploitation by way of CVE-2023-23397.”
WEBINARDiscover the Concealed Dangers of Third-Party SaaS Apps
Are you aware of the dangers linked with third-party application obtain to your company’s SaaS apps? Be a part of our webinar to master about the sorts of permissions staying granted and how to limit risk.
RESERVE YOUR SEAT
The disclosure will come as the U.S. Cybersecurity and Infrastructure Security Company (CISA) introduced a new open resource incident reaction resource that assists detect signs of destructive exercise in Microsoft cloud environments.
Dubbed the Untitled Goose Software, the utility features “novel authentication and info collecting procedures” to analyze Microsoft Azure, Azure Energetic Directory, and Microsoft 365 environments, the agency said.
Earlier this year, Microsoft also urged buyers to hold their on-premises Exchange servers updated as properly as consider actions to bolster their networks to mitigate likely threats.
Found this report attention-grabbing? Comply with us on Twitter and LinkedIn to go through additional unique articles we publish.
Some pieces of this posting are sourced from:
thehackernews.com

 OpenAI Reveals Redis Bug Behind ChatGPT User Data Exposure Incident
OpenAI Reveals Redis Bug Behind ChatGPT User Data Exposure Incident