Destructive ads served within Microsoft Bing’s synthetic intelligence (AI) chatbot are becoming utilised to distribute malware when searching for popular tools.
The conclusions occur from Malwarebytes, which uncovered that unsuspecting customers can be tricked into visiting booby-trapped websites and putting in malware directly from Bing Chat discussions.
Introduced by Microsoft in February 2023, Bing Chat is an interactive research expertise that is powered by OpenAI’s massive language model termed GPT-4. A month afterwards, the tech giant commenced discovering inserting advertisements in the discussions.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
But the transfer has also opened the doors for danger actors who vacation resort to malvertising methods and propagate malware.
“Advertisements can be inserted into a Bing Chat dialogue in several means,” Jérôme Segura, director of threat intelligence at Malwarebytes, said. “One of these is when a consumer hovers about a backlink and an advert is displayed very first just before the organic final result.”

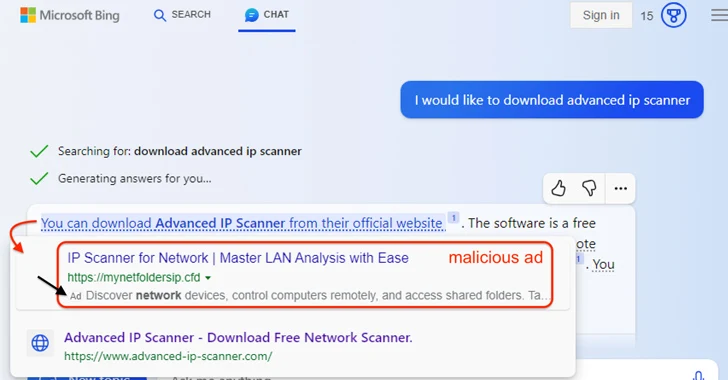
In an illustration highlighted by the cybersecurity seller, a Bing Chat question to download a genuine program called Innovative IP Scanner returned a connection that, when hovered, displayed a malicious advertisement pointing to a fraudulent connection prior to the official web page hosting the resource.
Clicking the backlink normally takes the user to a visitors direction program (TDS) that fingerprints and determines if the ask for is truly originating from a real human (as opposed to a bot, crawler, or sandbox), prior to using them to a decoy page that contains the rogue installer.
The installer is configured to run a Visible Simple Script that beacons to an exterior server with the likely intention of getting the up coming-phase payload. The exact mother nature of the malware shipped is presently not known.
A notable aspect of the marketing campaign is that the danger actor managed to infiltrate the advert account of a legit Australian organization and build the advertisements.
“Risk actors keep on to leverage search adverts to redirect buyers to malicious web sites hosting malware,” Segura stated. “With convincing landing internet pages, victims can easily be tricked into downloading malware and be none the wiser.”
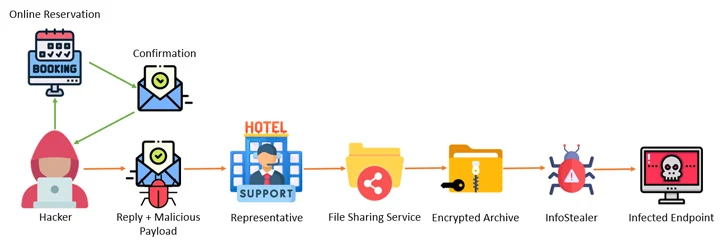
The revelation arrives as Akamai and Perception Stage uncovered a multi-step marketing campaign that involves attacking the programs of lodges, booking internet sites, and vacation companies with info stealer malware and then leveraging the obtain to the accounts to go just after financial data belonging to clients using bogus reservation webpages.
“The attacker, masquerading as the hotel, reaches out to the consumer by the reserving web site, urging the customer to ‘re-validate their credit card,’ then steals the customer’s information and facts,” Akamai researcher Shiran Guez mentioned, noting how the attacks prey on the victim’s feeling of urgency to pull off the procedure.
Approaching WEBINARFight AI with AI — Battling Cyber Threats with Following-Gen AI Applications
All set to tackle new AI-driven cybersecurity difficulties? Join our insightful webinar with Zscaler to tackle the developing risk of generative AI in cybersecurity.
Supercharge Your Abilities
Cofense, in a report posted this 7 days, stated the hospitality sector has been at the receiving conclude of a “perfectly-crafted and innovative social engineering attack” that is designed to produce stealer malware these as Lumma Stealer, RedLine Stealer, Stealc, Spidey Bot, and Vidar.
“As of now, the campaign only targets the hospitality sector, generally concentrating on luxurious lodge chains and resorts, and works by using lures relative to that sector these as scheduling requests, reservation improvements, and specific requests,” Cofense stated.
“The lures for both the reconnaissance and phishing email messages match accordingly and are properly thought out.”
The company phishing menace administration agency said it also observed destructive HTML attachments meant to have out Browser-in-the-Browser (BitB) attacks by serving seemingly innocuous pop-up windows that entice email recipients into furnishing their Microsoft credentials.
The discoveries are a indication that danger actors are consistently acquiring new techniques to infiltrate unwitting targets. Buyers ought to avoid clicking on unsolicited hyperlinks, even if they look respectable, be suspicious of urgent or threatening messages inquiring for instant motion, and test URLs for indicators of deception.
Discovered this post appealing? Stick to us on Twitter and LinkedIn to go through more exceptional articles we post.
Some parts of this short article are sourced from:
thehackernews.com

 Progress Software Releases Urgent Hotfixes for Multiple Security Flaws in WS_FTP Server
Progress Software Releases Urgent Hotfixes for Multiple Security Flaws in WS_FTP Server