Microsoft on Thursday flagged a cross-system botnet that’s generally designed to launch dispersed denial-of-services (DDoS) attacks from private Minecraft servers.
Known as MCCrash, the botnet is characterized by a unique spreading mechanism that will allow it to propagate to Linux-centered units despite originating from destructive program downloads on Windows hosts.
“The botnet spreads by enumerating default qualifications on internet-uncovered Safe Shell (SSH)-enabled equipment,” the organization reported in a report. “Simply because IoT gadgets are normally enabled for distant configuration with perhaps insecure settings, these gadgets could be at risk to attacks like this botnet.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

This also signifies that the malware could persist on IoT gadgets even immediately after getting rid of it from the infected source Pc. The tech giant’s cybersecurity division is monitoring the activity cluster beneath its rising moniker DEV-1028.
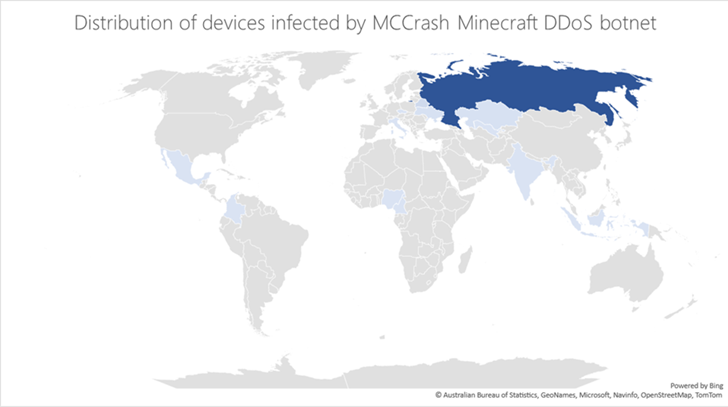
A majority of the infections have been reported in Russia, and to a lesser extent in Kazakhstan, Uzbekistan, Ukraine, Belarus, Czechia, Italy, India, and Indonesia. The company did not disclose the specific scale of the marketing campaign.
The first an infection stage for the botnet is a pool of devices that have been compromised via the installation of cracking equipment that assert to present illegal Windows licenses.
The software program subsequently acts as a conduit to execute a Python payload that consists of the main features of the botnet, like scanning for SSH-enabled Linux devices to start a dictionary attack.
On breaching a Linux host applying the propagation approach, the very same Python payload is deployed to run DDoS instructions, 1 of which is especially set up to crash Minecraft servers (“ATTACK_MCCRASH”).
Microsoft explained the system as “remarkably productive,” noting it really is possible offered as a services on underground discussion boards.
“This form of menace stresses the significance of guaranteeing that companies take care of, hold up to day, and monitor not just conventional endpoints but also IoT gadgets that are usually less secure,” scientists David Atch, Maayan Shaul, Mae Dotan, Yuval Gordon, and Ross Bevington said.
The findings arrive times following Fortinet FortiGuard Labs uncovered facts of a new botnet dubbed GoTrim, which has been noticed brute-forcing self-hosted WordPress internet sites.
Identified this report fascinating? Observe us on Twitter and LinkedIn to go through additional exclusive material we submit.
Some pieces of this post are sourced from:
thehackernews.com


 CISA Alert: Veeam Backup and Replication Vulnerabilities Being Exploited in Attacks
CISA Alert: Veeam Backup and Replication Vulnerabilities Being Exploited in Attacks