The MITRE Corporation has officially manufactured readily available a new risk-modeling framework termed EMB3D for makers of embedded equipment applied in critical infrastructure environments.
“The product delivers a cultivated information base of cyber threats to embedded equipment, offering a popular comprehension of these threats with the security mechanisms demanded to mitigate them,” the non-income reported in a publish saying the move.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A draft variation of the design, which has been conceived in collaboration with Niyo ‘Little Thunder’ Pearson, Crimson Balloon Security, and Narf Industries, was earlier launched on December 13, 2023.
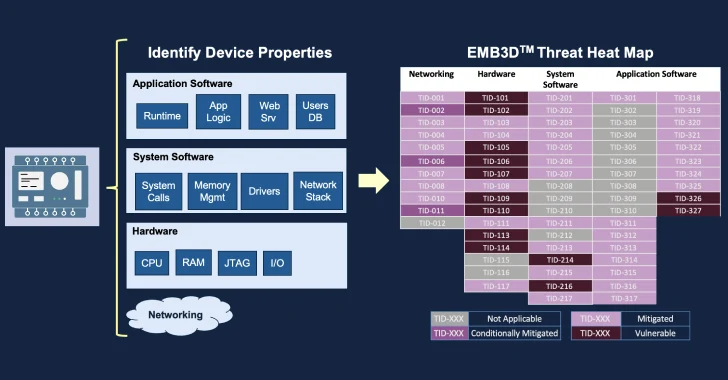
EMB3D, like the ATT&CK framework, is envisioned to be a “residing framework,” with new and mitigations added and updated about time as new actors, vulnerabilities, and attack vectors arise, but with a unique aim on embedded units.

The final objective is to give product distributors with a unified photo of different vulnerabilities in their technologies that are prone to attacks and the security mechanisms for mitigating these shortcomings.
Analogous to how ATT&CK gives a uniform system for monitoring and communicating threats, EMB3D aims to offer a central awareness foundation of threats focusing on embedded units.
“The EMB3D product will deliver a usually means for ICS unit companies to comprehend the evolving threat landscape and opportunity offered mitigations previously in the design and style cycle, ensuing in extra inherently safe equipment,” Pearson observed at the time.
“This will get rid of or lessen the have to have to ‘bolt on’ security soon after the actuality, resulting in much more protected infrastructure and minimized security charges.”
In releasing the framework, the strategy is to embrace a protected-by-layout strategy, thus allowing businesses to release merchandise that have a reduced quantity of exploitable flaws out of the box and have safe configurations enabled by default.

Analysis that operational technology (OT) cybersecurity organization Nozomi Networks introduced final year disclosed that danger actors have opportunistically specific industrial environments by exploiting vulnerabilities, abusing qualifications, and phishing for first accessibility, DDoS tries, and trojan execution.
Adversaries, the firm reported, have specially ramped up attacks concentrating on flaws discovered in OT and IoT products utilized throughout foodstuff and agriculture, chemical, drinking water treatment method, manufacturing, and energy sectors.
“EMB3D gives a cultivated expertise foundation of cyber threats to products, like individuals observed in the discipline ecosystem or demonstrated as a result of proofs-of-principle and/or theoretic exploration,” the non-revenue mentioned.
“These threats are mapped to machine attributes to support consumers develop and tailor precise risk versions for specific embedded units. For each individual danger, instructed mitigations are exclusively focused on complex mechanisms that device vendors need to carry out to secure towards the supplied threat, with the purpose of constructing security into the gadget.”
Uncovered this article fascinating? Observe us on Twitter and LinkedIn to go through much more special articles we put up.
Some pieces of this write-up are sourced from:
thehackernews.com

 The 2024 Browser Security Report Uncovers How Every Web Session Could be a Security Minefield
The 2024 Browser Security Report Uncovers How Every Web Session Could be a Security Minefield