The danger actors powering the Monti ransomware have resurfaced following a two-month break with a new Linux version of the encryptor in its attacks focusing on governing administration and authorized sectors.
Monti emerged in June 2022, months after the Conti ransomware group shut down its operations, intentionally imitating the tactics and equipment linked with the latter, including its leaked source code. Not any longer.
The new version, for each Craze Micro, is a departure of types, exhibiting major modifications from its other Linux-dependent predecessors.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“As opposed to the previously variant, which is generally centered on the leaked Conti resource code, this new edition employs a distinct encryptor with more distinctive behaviors,” Development Micro researchers Nathaniel Morales and Joshua Paul Ignacio said.
A BinDiff assessment has unveiled that even though the more mature iterations had a 99% similarity level with Conti, the most recent version has only a 29% similarity charge, suggesting an overhaul.

Some of the critical modifications consist of the addition of a ‘–whitelist’ parameter to instruct the locker to skip a list of digital devices as nicely as the elimination of command-line arguments –size, –log, and –vmlist.
The Linux variant is also built to tamper with the motd (aka information of the working day) file to show the ransom notice, employ AES-256-CTR encryption alternatively of Salsa20, and solely depend on the file measurement for its encryption process.
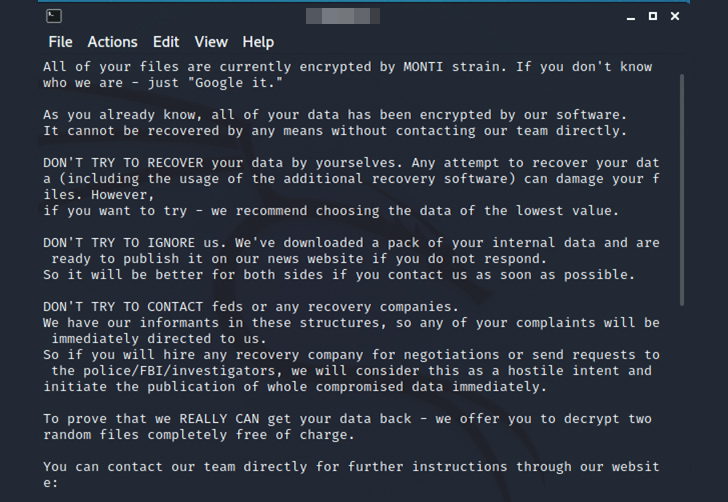
In other terms, information bigger than 1.048 MB but lesser than 4.19 MB will only have the to start with 100,000 (0xFFFFF) bytes of the file encrypted, whilst those people exceeding 4.19 MB have a chunk of their information locked based on the outcoming of a Change Ideal procedure.
Data files that have a measurement scaled-down than 1.048 MB will have all their contents encrypted.
“It is really possible that the threat actors guiding Monti however utilized parts of the Conti resource code as the base for the new variant, as evidenced by some very similar functions, but implemented major modifications to the code — especially to the encryption algorithm,” the scientists explained.
“Also, by altering the code, Monti’s operators are maximizing its capability to evade detection, making their malicious functions even far more difficult to recognize and mitigate.”
Identified this post exciting? Adhere to us on Twitter and LinkedIn to browse extra special content we publish.
Some areas of this posting are sourced from:
thehackernews.com

 Malware Unleashed: Public Sector Hit in Sudden Surge, Reveals New Report
Malware Unleashed: Public Sector Hit in Sudden Surge, Reveals New Report