The Procedure Triangulation spy ware attacks targeting Apple iOS units leveraged in no way-just before-seen exploits that produced it possible to even bypass pivotal components-centered security protections erected by the company.
Russian cybersecurity firm Kaspersky, which identified the campaign at the starting of 2023 right after getting one particular of the targets, explained it as the “most advanced attack chain” it has at any time observed to date. The marketing campaign is believed to have been energetic due to the fact 2019.
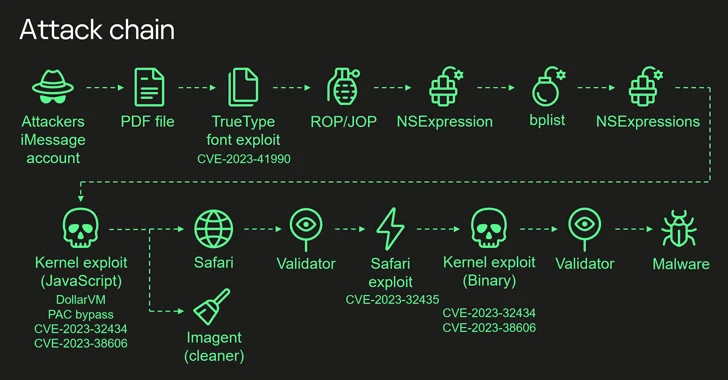
The exploitation exercise associated the use of 4 zero-working day flaws that have been fashioned into a chain to receive an unprecedented degree of accessibility and backdoor target devices operating iOS versions up to iOS 16.2 with the greatest aim of accumulating delicate information and facts.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Approaching WEBINAR From User to ADMIN: Understand How Hackers Attain Complete Regulate
Uncover the key methods hackers use to turn into admins, how to detect and block it right before it really is as well late. Sign-up for our webinar now.
Be a part of Now
The starting place of the zero-simply click attack is an iMessage bearing a destructive attachment, which is mechanically processed sans any user interaction to in the long run get elevated permissions and deploy a spyware module. Specifically, it will involve the weaponization of the next vulnerabilities –
- CVE-2023-41990 – A flaw in the FontParser part that could guide to arbitrary code execution when processing a specially crafted font file, which is despatched by way of iMessage. (Resolved in iOS 15.7.8 and iOS 16.3)
- CVE-2023-32434 – An integer overflow vulnerability in the Kernel that could be exploited by a malicious application to execute arbitrary code with kernel privileges. (Addressed in iOS 15.7.7, iOS 15.8, and iOS 16.5.1 )
- CVE-2023-32435 – A memory corruption vulnerability in WebKit that could direct to arbitrary code execution when processing specially crafted web content material. (Resolved in iOS 15.7.7 and iOS 16.5.1)
- CVE-2023-38606 – An issue in the kernel that permits a malicious application to modify sensitive kernel condition. (Dealt with in iOS 16.6)
It’s truly worth noting that patches for CVE-2023-41990 were released by Apple in January 2023, whilst specifics about the exploitation ended up only manufactured public by the firm on September 8, 2023, the similar day it delivered iOS 16.6.1 to solve two other flaws (CVE-2023-41061 and CVE-2023-41064) that were actively abused in connection with a Pegasus spy ware marketing campaign.
This also brings the tally of the amount of actively exploited zero-times settled by Apple since the start out of the 12 months to 20.
Of the 4 vulnerabilities, CVE-2023-38606 warrants a distinctive mention as it facilitates a bypass of hardware-based security security for sensitive locations of the kernel memory by leveraging memory-mapped I/O (MMIO) registers, a aspect that was in no way known or documented until now.
The exploit, in certain, targets Apple A12-A16 Bionic SoCs, singling out unidentified MMIO blocks of registers that belong to the GPU coprocessor. It truly is at the moment not regarded how the mysterious menace actors at the rear of the operation figured out about its existence. Also unclear is no matter if it was produced by Apple or it is a third-party element like ARM CoreSight.
To place it in one more way, CVE-2023-38606 is the important url in the exploit chain which is closely intertwined with the results of the Procedure Triangulation campaign, given the point that it permits the menace actor to obtain complete management of the compromised process.

“Our guess is that this unfamiliar hardware characteristic was most very likely meant to be applied for debugging or testing reasons by Apple engineers or the factory, or that it was provided by oversight,” security researcher Boris Larin claimed. “For the reason that this function is not used by the firmware, we have no notion how attackers would know how to use it.”
“Components security quite frequently relies on ‘security as a result of obscurity,’ and it is a great deal much more tough to reverse-engineer than software, but this is a flawed solution, because quicker or afterwards, all techniques are revealed. Devices that count on “security through obscurity” can by no means be truly protected.”
The improvement arrives as the Washington Put up reported that Apple’s warnings in late Oct about Indian journalists and opposition politicians could have been focused by point out-sponsored spyware attacks prompted the government to dilemma the veracity of the claims and explain them as a scenario of “algorithmic malfunction” in the tech giant’s units.
In addition, senior administration officers demanded that the business soften the political affect of the warnings and pressed the organization to give different explanations as to why the warnings could have been despatched. So considerably, India has neither verified nor denied applying spy ware this kind of as all those by NSO Group’s Pegasus.
Citing people today with information of the make a difference, the Washington Submit mentioned that “Indian officers questioned Apple to withdraw the warnings and say it experienced manufactured a mistake,” and that “Apple India’s company communications executives commenced privately inquiring Indian technology journalists to emphasize in their tales that Apple’s warnings could be bogus alarms” to change the highlight away from the federal government.
Discovered this article fascinating? Adhere to us on Twitter and LinkedIn to examine far more special material we submit.
Some parts of this short article are sourced from:
thehackernews.com

 New Rugmi Malware Loader Surges with Hundreds of Daily Detections
New Rugmi Malware Loader Surges with Hundreds of Daily Detections